This article delves into the pivotal cybersecurity trends emerging from SecureSky's comprehensive security assessments of Microsoft Azure environments throughout 2021. Our analysis spans a diverse...


This article delves into the pivotal cybersecurity trends emerging from SecureSky's comprehensive security assessments of Microsoft Azure environments throughout 2021. Our analysis spans a diverse...

In light of growing cybersecurity concerns and response to our community's feedback on a recent LinkedIn update, there's a pressing need for Microsoft Sentinel users to effectively monitor their...

Since its introduction in 2019, Microsoft Sentinel has quickly become a frontrunner in the cloud-native SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation,...

In 2021, the cybersecurity landscape witnessed an alarming rise in ransomware attacks, occurring at a staggering rate of every 11 seconds. This uptick is not just in frequency; the financial stakes...

The shift to remote work has accelerated the adoption of collaboration tools like Microsoft Teams, often outpacing the necessary security considerations. This rapid deployment, coupled with an...

The COVID-19 pandemic has not only reshaped our daily lives but also opened new avenues for cybercriminals to exploit our generosity and quest for holiday deals. With the holiday season expected...
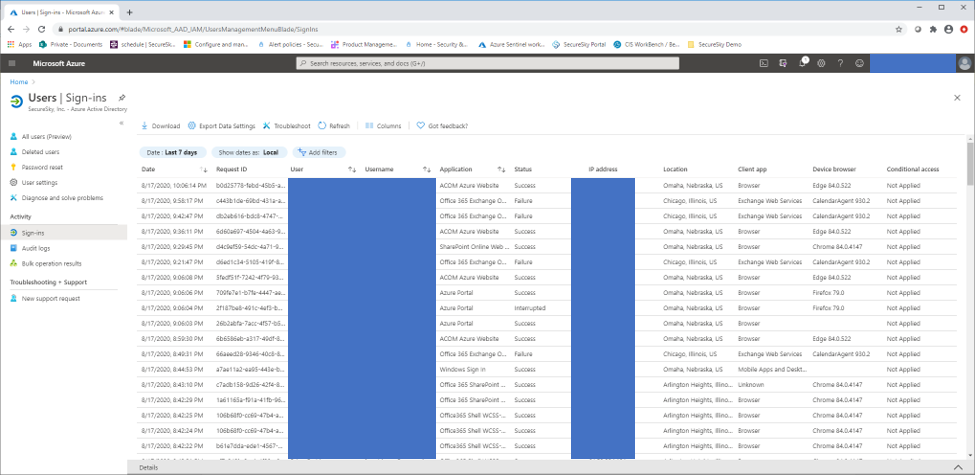
In today's digital workspace, safeguarding user accounts in Office 365 against compromises is a critical challenge for organizations. Azure Sentinel, Microsoft's premier cloud-native SIEM platform,...

In our preceding discussion, we delved into the critical importance of the 12 Foundational Security Controls essential for safeguarding every Office 365 environment against threats such as Business...

In the wake of a shifting global workforce towards remote operations, the reliance on cloud-based services has surged. As Microsoft CEO Satya Nadella highlighted, the digital landscape has...

In the current digital era, where remote work has become the norm, the security of audio/video conferencing software is paramount. Following up on SecureSky's "Top 10 Audio/Video Conferencing...