Enhancing Microsoft Teams Security: Essential Controls & Best Practice
Apr 26, 2021 | Industry Insight
The shift to remote work has accelerated the adoption of collaboration tools like Microsoft Teams, often outpacing the necessary security considerations. This rapid deployment, coupled with an increase in demand, has highlighted several security and operational challenges, particularly as Teams extends into critical areas like healthcare and education, which demand stringent access control and confidentiality measures.
This article outlines key security service controls for Microsoft Teams, aiming to secure configurations and educate users, particularly those hosting and moderating meetings. Given the diverse applications of Teams across different organizations, these security measures should be tailored to fit specific operational needs.
Recommended Foundational Security Controls for Microsoft Teams
SecureSky recommends the following twelve Microsoft Teams security controls be evaluated by organizations.
1. Policy Packages
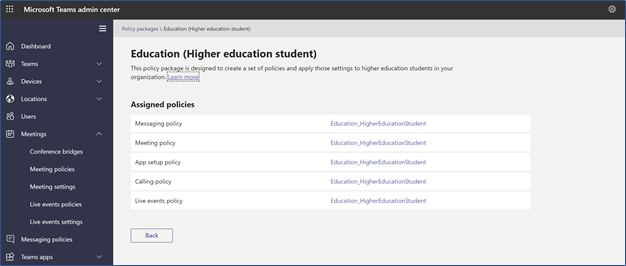
In-call settings are highly dependent upon the anticipated organizational use of Teams. Microsoft has defined Global or organization-wide defaults and created several policy packages that include configuration settings for different use cases, as presented in the following screenshot:
Policy Packages
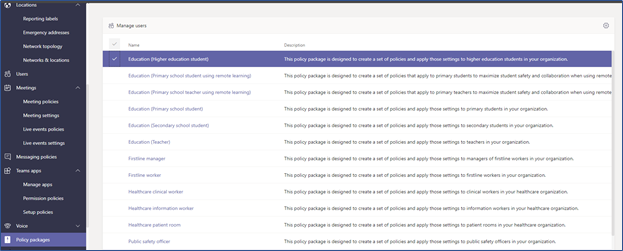 These policy packages cover Messaging, Meeting, App setup, Calling, and Live event policies and can be customized to align with company and call requirements at a user group level.
These policy packages cover Messaging, Meeting, App setup, Calling, and Live event policies and can be customized to align with company and call requirements at a user group level.
Example Education Policy Package
Recommendation
Implement default or customized policy packages for each Teams component that applies to your organization's needs. In many organizations, multiple policies packages may be required to secure different types of organization meetings. The recommendations that follow are intended to help customize policies and gain visibility to detect threats against your Team's environment.
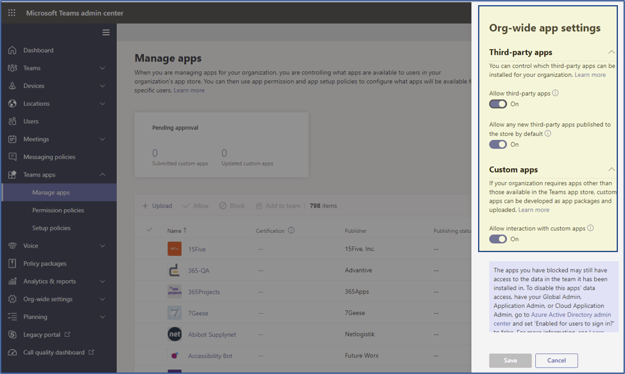
2. Organizational Teams Apps Management
Organizations can control third-party apps that their users can install. Use of malicious third-party apps have become another attack vector for organizational data.
Third-Party Apps Menu
Recommendation
Where possible, third-party app access and custom app interaction should be disabled:
- The Allow third-party apps setting should be turn Off.
- Allow any new third-party apps published to the store by default' should be set to Off.
- Custom Apps should also be set to Off.
Note: The apps you have blocked may still have access to the data in the team it has been installed in. To disable this apps' data access, have your Global Admin, Application Admin, or Cloud Application Admin, go to Azure Active Directory admin center, select the desired application, and set 'Enabled for users to sign in?' to false. For more information, please see the related Microsoft documentation.
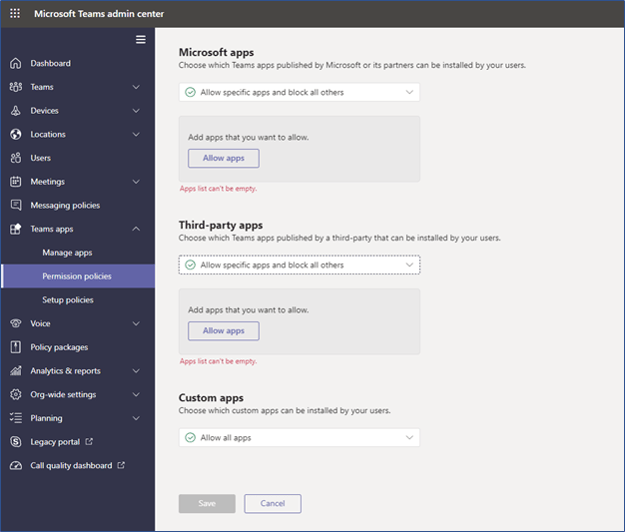
3. Organizational Teams App Permissions Policies
Organizations can specify granular application installation permissions for Microsoft apps, third-party apps, and custom apps:
Recommendation
Permitted and denied Microsoft applications should be specified. If custom and third-party apps will be allowed, all applications should be reviewed and granular permissions set or blocked.
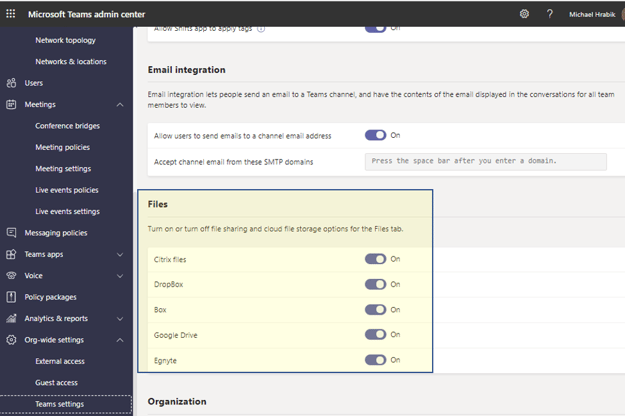
4. Third-Party File Storage
Teams provides an option to share files in third-party applications, like Box and Google Drive, as presented in the following screenshot:
Third-Party File Sharing
Recommendation
Turn off all cloud file storage options except authorized and protected file storage locations. If third-party file sharing is required, limit file sharing and cloud file storage options to approved and monitored applications.
5. Teams Meeting Recording
Teams meeting recording's locations have moved from Streams to OneDrive and SharePoint. Default permissions have also changed in late 2020 (MC222640) and early 2021 (MC230505) with the introduction of permissions and role-based access. The enhanced security and privacy permissions set will be deployed by default and cannot be overridden, but these settings do not affect previously recorded Teams meetings.
Details on new defaults:
Use OneDrive for Business and SharePoint for meeting recordings - Microsoft Teams | Microsoft Docs
Teams Live recent update (MC246706) default to Never record, all live events will have the recordings disabled for everyone: the presenter, organizer, and attendees have three options:
- Always record
- Never record
- The organizer can choose to record or not to record
Live Event Policies
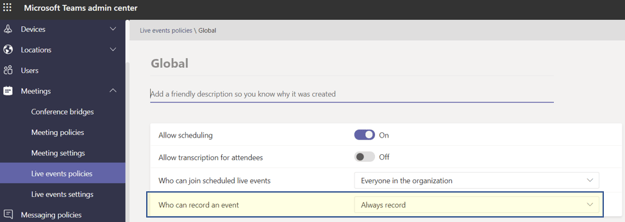
Before this update, the Teams live events organizer could enable attendee recordings despite the event Recording policy being set to Never record.
Recommendation
Since the introduction of more secure defaults, permissions, and role-based access did not affect the previous recordings, we recommend reviewing recordings created before April 2021 (expected rollout date) in Streams, OneDrive, and SharePoint to ensure appropriate permissions are applied.
6. Teams Calling (Voice) Policies
Teams’ calling policies control users' calling and forwarding features such as: making private calls, using call forwarding or simultaneous ringing to other users or external phone numbers, routing calls to voicemail, sending calls to call groups, using delegation for inbound and outbound calls. The default Global Policy Package (1.10) can be used, or the organization can create and assign custom policies.
Security and Cost Controls
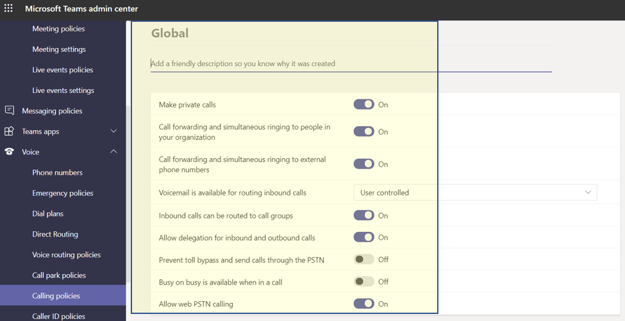
Recommendation
Implement policy packages or customize a policy that uses the least privilege principle on calling needs, the same as tenant(s) or data access needs.
The following should be considered risky and should be reviewed and only allowed with users or groups not considered a security risk. These settings should be part of the ongoing monitoring, alert and hunting regiment.
- Allow delegation for inbound and outbound calls: This setting enables inbound calls to be routed to delegates, allowing delegates to make outbound calls on behalf of the users they have delegated permissions. This setting should be set to Off.
- Prevent toll bypass and send calls through the PSTN: Setting this to On will send calls through the PSTN and incur charges rather than sending them through the network and bypassing the tolls. This setting should be set to Off.
- Allow web PSTN calling: This setting enables users to call PSTN numbers using the Teams web client. This setting should be set to Off.
7. User Meeting Control Options
In-call settings are highly dependent upon Teams' anticipated organizational use and, in many cases, the actual meeting and participants. Microsoft has created and continues to add multiple controls for meeting hosts and moderators. Options for a Schedule Meeting can be customized by double-clicking the Schedule meeting and select Meeting options near the top of the screen.
Click Meeting Options
Meeting Options Settings
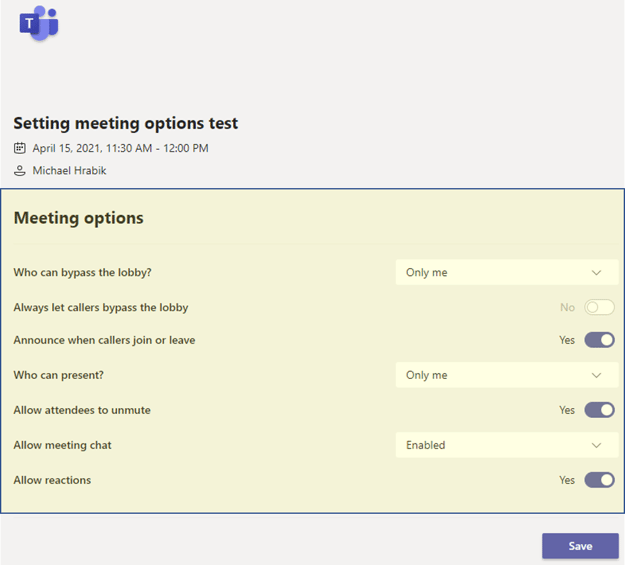
In the April 2021 rollout, meeting organizers and presenters will be able to prevent meeting attendees from turning their cameras on to share videos during a meeting. Currently, meeting organizers and presenters have no control over whether meeting attendees can share a video or prevent attendees from sharing a video feed in Teams Meetings. By default, camera sharing is enabled, which means that attendees can share their video feed.
April, 2021 Feature Rollout
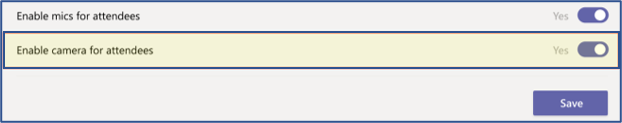
The meeting organizer can also prevent attendees from unmuting during the meeting. With this setting enabled, all attendees (but not presenters) will be muted when they join the meeting and won't be able to unmute themselves. In the current state, attendees must raise their hand to request to speak before a meeting organizer or presenter can unmute the attendee.
Note: Organizers and presenters cannot prevent attendees who dial into a meeting using the phone number provided in the meeting details from unmuting. This functionality is in development. Additionally, organizers and presenters joining from Teams meeting room devices cannot modify attendee ability to use their microphone.
Recommendation
Set appropriate global and group policies, educate employees, and set meeting standards and protocols when possible.
Examples of some potential protocol items for meeting with sensitive content:
- Meeting Setup
- Use waiting room to validate and screen attendees.
- Restrict attendees to unmute and present.
- Record meeting only when necessary, limit and control sharing.
- Disable chat or file-sharing feature.
- Meeting Protocol
- Host or Moderator should take roll call.
- Summarize meeting protocol before starting meeting.
- Remind the attendees not to share other sensitive information during the meeting inadvertently.
Some additional guidance for employees to conduct secure meetings are included at the following links:
Admin training resources - Microsoft Teams | Microsoft Docs
8. Anonymous User Access
Teams provide an option to block anonymous users from joining and interacting with apps during meetings, as presented in the following screenshot:
Note: The term anonymous users means users that are not authenticated to the organization's tenant. In this context, all external users are considered anonymous. Authenticated users include tenant users and Guest users of the tenant.
Anonymous User Access
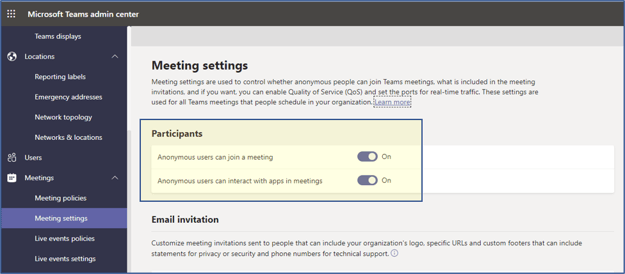
Recommendation
This setting is not applicable to all environments. However, those organizations that limit Teams use to internal participants could implement this setting to block external users from joining meetings.
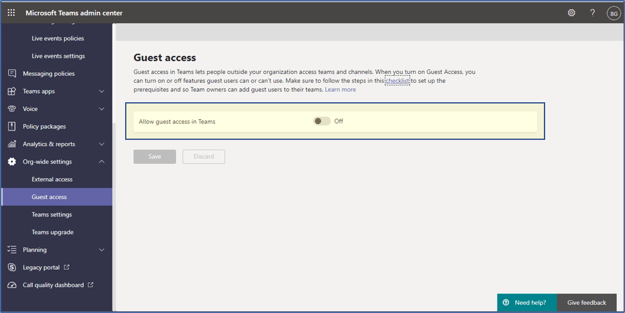
9. Guest User Access Permissions
Guest access in Teams allows users outside of an organization to access teams and channels, as presented in the following screenshot:
Note: Guest access is someone who is not an employee, student, or member of your organization, but they have been invited to collaborate, have accepted the invitation, and have a guest account in your Azure Active Directory tenant. For example, guests may include partners, vendors, suppliers, or consultants.
Guest User Access In Teams (1)
Recommendation
If Teams is intended only for internal user use, Guest access should be restricted. If Guest access in Teams is required, specific Guest access permissions should be configured, as described below:
Guest User Access In Teams (2)
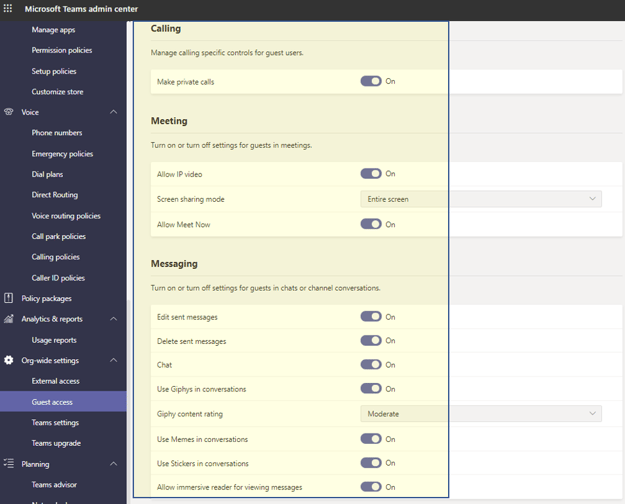
| Configuration Setting | Recommendation |
| Make private call | Off |
| Allow Meet Now | Off |
| Edit and Delete sent messages | Off |
| Screen sharing mode | Single application |
| Use Giphy content rating | Strict - strictly restricted from adult content |
There are multiple settings that affect how and who can invite guests to your tenant. Some additional guidance for administrators to review Teams, Azure Active Directory ,and SharePoint settings are provided in the link below:
https://docs.microsoft.com/en-us/microsoft-365/solutions/collaborate-as-team?view=o365-worldwide
10. Participant and Guest Meeting Permissions
Participant and Guest Settings set the configuration for how participants and guests can interact with a meeting or Team. It is important to consider changing the default settings for Guest Access.
Participants and Guest Access Settings
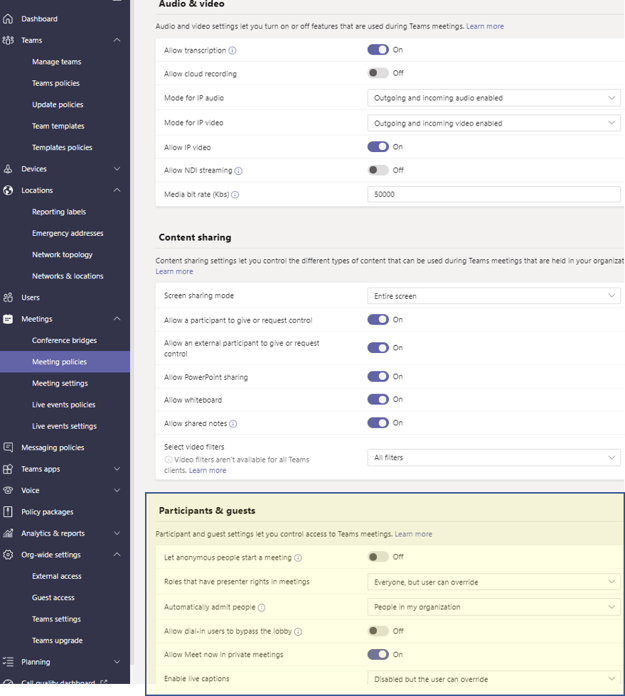
Recommendation
Review guest user settings and implement the appropriate settings for your environment. We recommend deploying the following configuration setting for how Guests can join and participate in a Teams meeting.
| Configuration Setting | Recommendation |
| Guest Access Settings | Off |
| Let anonymous people start a meeting | Off (Non-Guest can override this setting) |
| Admit people automatically | People in my organization |
| Allow dial-in users to bypass the lobby | Off |
| Allow Meet now in private meetings | Off |
| Enable live captions | Disabled (User can override this default setting) |
11. Enabling Supervised Chats Monitoring - Education
Supervised chat allows designated educators to initiate chats with students and blocks students from starting new chats unless an appropriate educator is present. When chat supervision is enabled, supervisors aren't allowed to leave chats and other participants aren't allowed to remove them, ensuring that chats involving students are properly supervised.
Chat Permission Roles
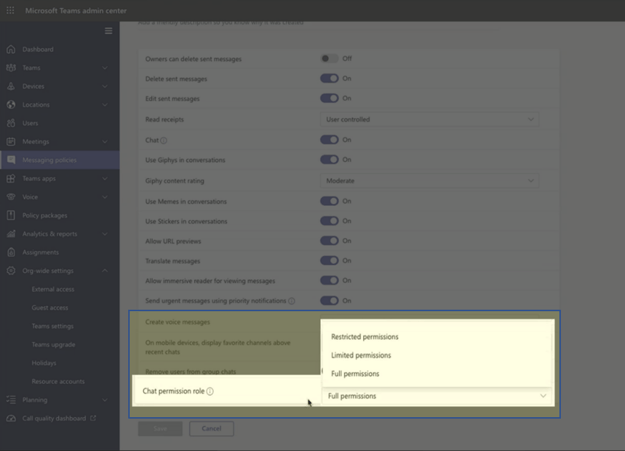
Supervised Chat
For supervised chat to work as expected each user within your environment needs to be assigned the correct chat permission role. There are three roles that a user can have assigned:
- Full permissions – This role is for educators who should have full access to students and other staff members. They can start chats with any user within your environment. Users with full permissions are expected to supervise the chats they participate in. They can't leave or be removed from chats that they start or chats that they're watching in federated tenants.
- Limited permissions – This role is for staff members who should only have supervised access to students and have full access to other staff and educators. They can start chats with any full or limited users but can't start chats with restricted users. If a user with full permissions begins a chat with a restricted user, limited users can be brought into the conversation. This access happens because a user with full permissions is present to supervise collaboration between limited and restricted users.
- Restricted permissions – This role is for students who need to be supervised. They can only start chats with users who have full permissions. They can participate in any conversation that a user with full permissions invites them to. In federated chat cases, restricted users can only be added to chats by a user with full permissions from the restricted user's tenant.
Recommendation
Enable supervised chat (it is disabled by default). After setting chat permission roles for users, enable supervised chat within the tenant by going to Org-wide settings > Teams Settings and setting the role-based chat permissions policy to On.
For additional information, see:
12. Overall Security Controls and Monitoring
Teams are tightly integrated with other Microsoft and Office 365 components like Azure Active Directory SharePoint, and OneDrive. SecureSky, therefore, recommends including Teams in your organization's security monitoring scope and reviewing previous SecureSky blogs for related control and configuration best practices:
Foundational Security Controls for Every Office 365 Environment
Implementing Foundational Security Controls for Every Office 365 Environment
In addition to the implementation of relevant security controls, organizations must monitor Teams environment for potential attacks and misuse. Microsoft now has a native O365 connector for Azure Sentinel, enabling security and operational personnel to monitor, handle alerts, and conduct hunting activity in Exchange, SharePoint, OneDrive, and Teams. Teams activity captured in these events includes file downloads, access requests sent, changes to group events, mailbox operations, and Teams events such as chat, team, member, and channel events.
Recommendation
Enable Office 365 auditing and leverage Azure Sentinel, or a third-party SIEM, to view and analyze Teams () and other Office 365 event data.
Thank you for reading the SecureSky Dynamic Cloud Security Blog.
For more information about SecureSky, or assistance in protecting your Microsoft Teams and cloud SaaS and IaaS environments, please contact us at:
+1 833.473.2759 (+1 833.4SecSky)