Improve Office 365 Security: Mitigating Email Forwarding Risks
Apr 30, 2020
Updated July 28, 2020: Microsoft is addressing the complexities around email forwarding in Office 365 by updating its configuration settings. SecureSky is currently evaluating these updates, detailed in Microsoft's official documentation, and will provide further insights upon completing our analysis.
The surge in remote work has led to an increased reliance on collaboration tools like Microsoft Teams and Zoom, often deployed without comprehensive security assessments. This rapid adoption has exposed vulnerabilities, particularly in email security within Office 365, as attackers exploit gaps in best practice guidelines for undetected eavesdropping.
Email Forwarding: A Gateway for Attackers
Attackers gaining access to an Office 365 account frequently set up email forwarding to monitor incoming messages, aiding in phishing schemes and information gathering for impersonation attacks. This tactic, known as "email eavesdropping," poses significant risks, yet Office 365 lacks a straightforward solution to block email forwarding across the tenant.
Current Office 365 Security Solutions and Their Limitations
The common workaround involves creating mail transport flow rules to block external message forwarding. However, this does not prevent forwarding via the Office 365 Outlook web client (OWA), leaving a significant security gap.
Mail Flow Rules
Recommended for blocking auto-forwarding within the Office 365 Outlook client, though ineffective for OWA.
This guidance instructs the reader to create Exchange mail flow rule with the following attributes:
- If the sender is inside the organization
- If the message type is Auto-forward
- Reject the message and include an explanation
This guidance works well within the Office 365 Outlook client. A blocked email is presented below:
Mail Transport Flow Rule Blocks Message
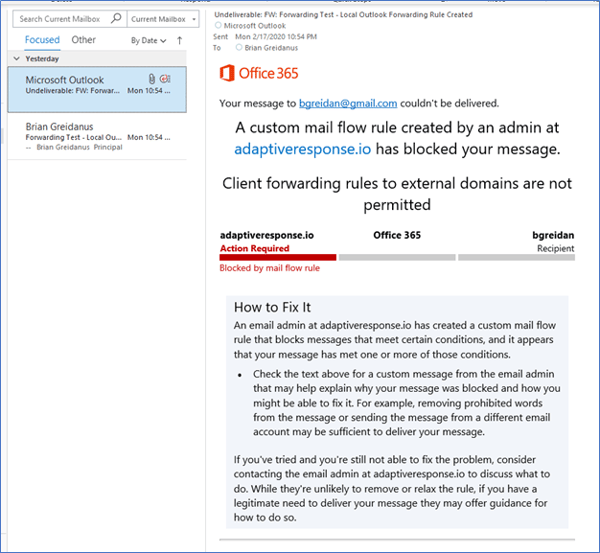
However, this guidance does not apply to the Office 365 Outlook web client (OWA). Email forwarding can still be configured in the Outlook Web Client, as presented in the following screenshot, and emails are successfully forwarded.
Mail Forwarding Set on Outlook Web Access
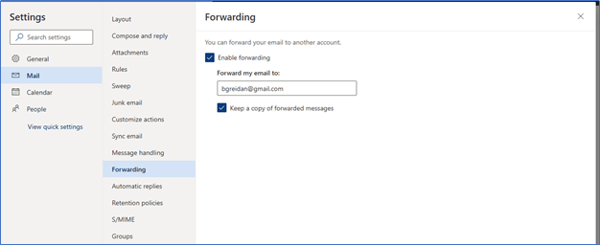
When considering that attackers will often use OWA to access compromised client credentials, use of Mail Flow rules can be considered incomplete at best.
Remote Domains
A more comprehensive solution for blocking all email is using the remote domains setting in Microsoft Exchange, which is presented below:
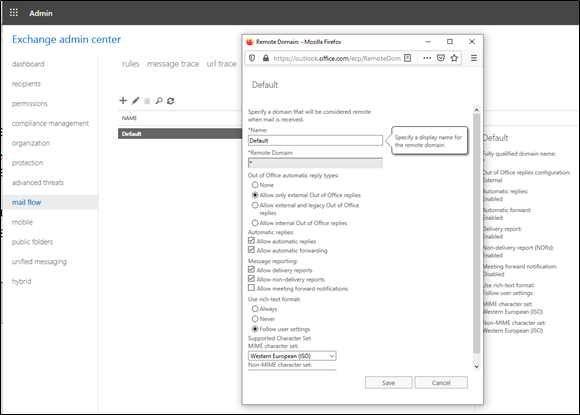
While this fix implements protection against email forwarding for all mailboxes, it is not a perfect solution. There are two known limitations to this approach:
- Lack of visibility - When the Remote Domains ‘allow automatic forwarding’ setting is disabled, the warning message from the mail flow rule will no longer trigger. As a result, visibility into whether email forwarding was turned on in an Outlook client will be lost. Even if forwarding is disabled, this visibility is important to identify if attempts to enable forwarding are made. These attempts may still be indicative of an account breach.
- Lack of granularity in implementation – The Remote Domains setting is on or off, it does not allow for potential exclusions (e.g. if one employee temporarily requires forwarding because of leave or travel requirements). The mail flow rule, if functional for both OWA and Outlook client, would enable greater granularity.
PowerShell Commands
The third type of guidance uses PowerShell commands to create a new user mailbox role that removes the parameters responsible for the email forwarding functionality in OWA. We have not included that guidance in this discussion for two reasons:
- Implementation of multiple PowerShell commands to change Microsoft exchange settings is not a practical solution for many organizations, especially small and medium businesses
- SecureSky’s testing of the PowerShell guidance indicates that it is not effective.
For those interested, a link to the PowerShell guidance is presented below:
PowerShell remediation guidance
SecureSky's Recommendations
Given these challenges, organizations should adopt a multi-faceted approach to manage email forwarding securely:
- Block All Forwarding: Ideal for environments where email forwarding is unnecessary, utilizing Exchange Remote Domains to eliminate forwarding.
- Monitor and Allow General Forwarding: Where forwarding is needed, vigilant monitoring of Office 365 alerts is crucial to detect misuse or account compromises.
- IT-Approved Forwarding Only: Combining Mail Flow rules with Exchange Remote Domain blocking offers a secure method, allowing whitelisting of specific users for forwarding.
Moving Forward with Office 365 Security
Understanding and mitigating the risks associated with email forwarding in Office 365 is critical for maintaining secure communication channels. SecureSky remains committed to providing up-to-date guidance and support for navigating these challenges. For further assistance, contact our Office 365 Security team at info@securesky.com.
