In the ever-evolving landscape of cybersecurity, Managed Detection and Response (MDR) services have been a game-changer for organizations striving to safeguard their digital assets.


In the ever-evolving landscape of cybersecurity, Managed Detection and Response (MDR) services have been a game-changer for organizations striving to safeguard their digital assets.

In today's digital landscape, where a reported 75-80% of organizations face cyber attacks annually, the need for robust cybersecurity solutions has never been more critical. With the number of...
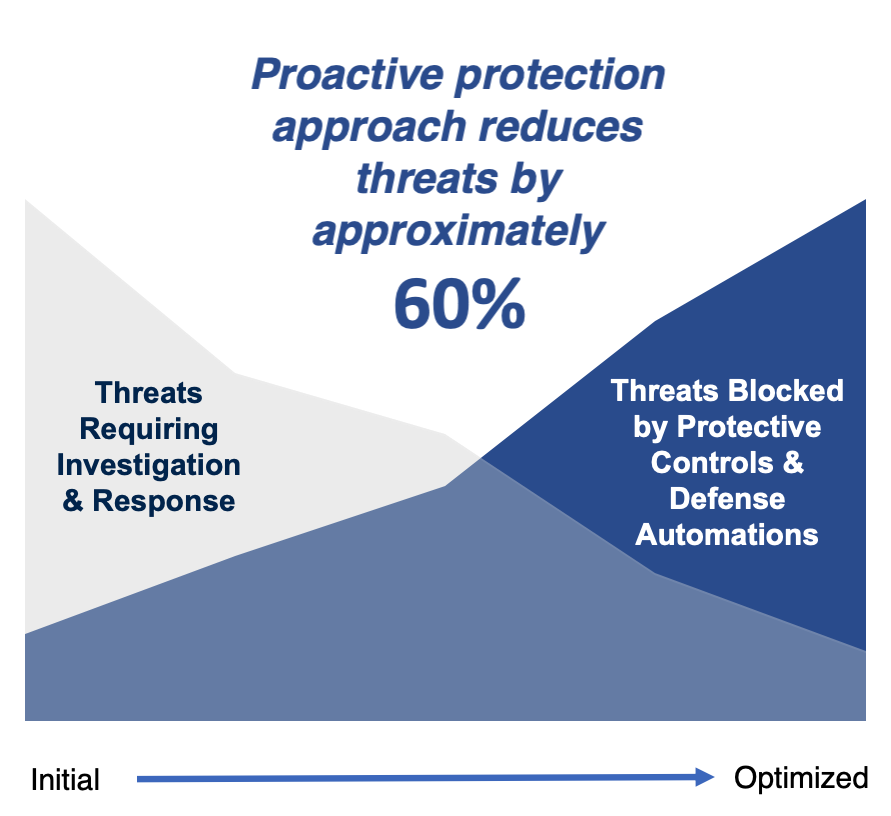
The digital threat landscape is evolving, with cybersecurity breaches becoming almost daily headlines. Attacks have increased by up to 300% since 2019, and breach costs are soaring. The IBM 2023 Cost...

In recent times, the cybersecurity landscape has faced unprecedented challenges, particularly with the onset of the COVID-19 pandemic. The SecureSky Cyber Threat Center reports a staggering 6x-7x...

The rapid advancements in technology demand constant adaptation, especially in the realm of security data collection. Microsoft's Monitoring Agent (MMA) and Operations Management Suite (OMS) Agent...

In this blog, we delve into the security configurations within Microsoft Azure, leveraging insights from SecureSky's Multi-Cloud Threat Exposure Management (CTEM) Platform for the years 2022-2023....
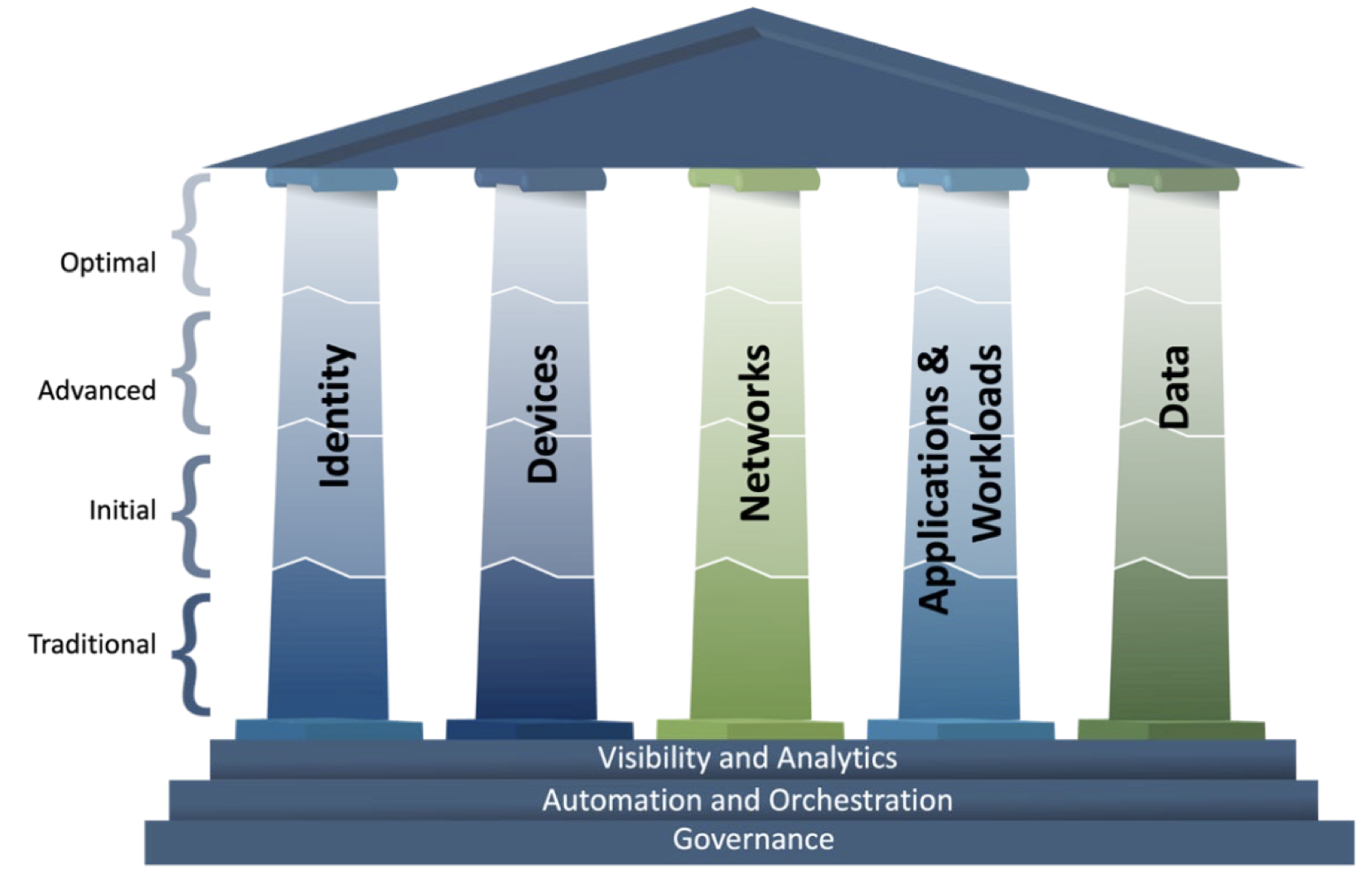
On April 11, 2023, the Cybersecurity and Infrastructure Security Agency (CISA) under the Department of Homeland Security (DHS) introduced an updated draft of the Zero Trust Maturity Model (ZTMM 2.0)....

In our ongoing exploration of Microsoft's Defender technologies, SecureSky aims to demystify the suite and highlight how these tools, particularly Microsoft Defender for DNS, can be enhanced by ...

In our comprehensive series, SecureSky aims to clarify the functionalities and applications of Microsoft's evolving Defender suite, focusing on the integration of Microsoft Defender for Resource...

In our ongoing series, SecureSky aims to shed light on the expansive suite of Microsoft Defender technologies, focusing on the integration of Microsoft Defender for Key Vault with Managed Detection...