Strengthening Your Defense: A Guide to Office 365 Security Controls
Aug 4, 2020 | Industry Insight
In our preceding discussion, we delved into the critical importance of the 12 Foundational Security Controls essential for safeguarding every Office 365 environment against threats such as Business Email Compromise (BEC), Account Takeover (ATO) attacks, and unauthorized data access.
It's important to recognize that Microsoft's platform is continuously evolving, and the recommendations provided are reflective of the latest best practices as of this writing.
This article aims to guide you through the practical steps for effectively implementing these essential Office 365 security controls, ensuring your organization's digital assets are robustly protected.
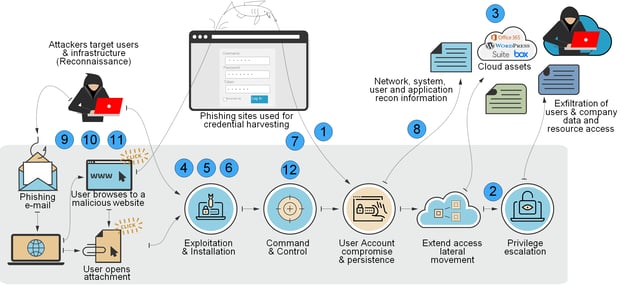
Strengthening Office 365 Security with Essential Controls
Leveraging the Cyber Kill Chain framework developed by Lockheed Martin, one of the most critical steps in fortifying your Office 365 environment against cyber threats is the implementation of Multi-Factor Authentication (MFA), especially for privileged roles. MFA stands as a formidable barrier against account compromise, requiring users to provide two or more verification factors to gain access.
Implementing MFA Across Your Office 365 Environment
To effectively deploy MFA, there are several strategies organizations can adopt, including direct configuration enforcement within Office 365, setting up conditional access policies, or integrating with third-party authentication solutions such as Okta or DUO. This section focuses on the approach of configuration enforcement to bolster Office 365 security.
Key Steps for MFA Configuration Enforcement:
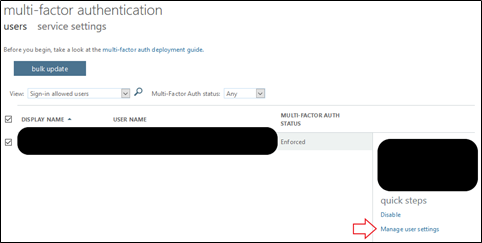
1. Review Current MFA Settings: Begin by logging into your Office 365 environment. To assess your current MFA configurations and ensure they align with best practices, visit this link.From this page, MFA status for all users in the environment can be viewed and modified.
Configure MFA Settings
2. Limit Number of Global Administrator Accounts – Global administrators should be kept to a minimum to limit accounts with superuser privileges. SecureSky recommends reviewing accounts with global administrator privileges and identifying those that can be given less privileged permissions while still able to perform necessary functions. Microsoft recommends 3 to 5 global administrators per environment.
To confirm the number of global administrators in your environment, authenticate to your M365/Azure environment, and then browse this link.
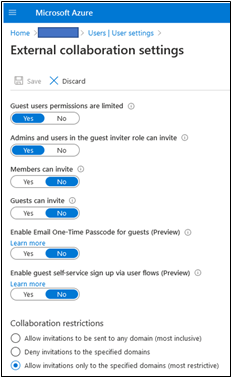
3. Limit User Privileges – By default, all users can invite guests, guests can invite guests, and guest invites can be sent to any domain. Unmanaged guest creation multiplies the chances an attacker can remain a persistent threat in your environment. SecureSky recommends configuring the policy so that:
- Only Admins and Users in the “Guest Inviter” role can invite guests
- “Guest” user permissions are limited
- “Members” and “Guests” cannot invite guests
- If possible, enable “Collaboration Restrictions” which permits invitations only to authorized domains
To confirm Guest user privileges in your environment, authenticate to your M365/Azure environment, browse to the following URL, and select “Manage external collaboration settings:"
These settings are presented in the following screenshot:
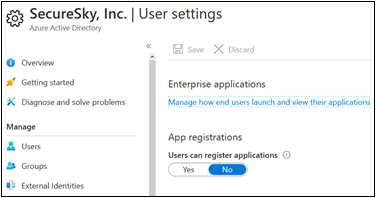
4. Restrict 3rd Party Application Integrations - By default, all users can register applications that can access organizational data. Attackers can create malicious applications and trick users into registering them. SecureSky recommends administrators control which applications that are registered.
URL to Access User Application Registration Permissions
https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/UserSettings
Azure Active Directory - User Settings
5. Outlook Add-in Permissions – Outlook add-ins are programs that run within Outlook to perform actions that Outlook does not provide. By default, users can install add-ins in their Outlook client, allowing the add-ins to access emails and the data contained within them. SecureSky recommends controlling which add-ins are permitted and removing a user’s ability to install them by modifying the “Default Role Assignment Policy.” Administrators can select and deploy add-ins for users as required.
To confirm Outlook Add-in privileges in your environment, authenticate to your M365/Azure environment, browse to the following URL.
From here, select “Permissions”, then “User Roles”, then select “Edit” to review the Default Role Assignment Policy. To prevent users from installing Outlook add-ins, remove the following roles: “My Custom Apps”, “My Marketplace Apps”, “My ReadWriteMailbox Apps.”
A screen shot of Outlook Add-in Permissions in a Default Role Assignment Policy is presented below:
Default Role Assignment Policy

6. Add-in Permissions (Word, Excel, PowerPoint) - Office add-ins are programs that run within Microsoft applications (Word, Excel, and PowerPoint) and perform actions that these applications do not provide. By default, users can install add-ins in their Word, Excel, and PowerPoint applications, allowing the add-ins to access the data contained within Word, Excel, and PowerPoint. SecureSky recommends controlling which add-ins are permitted and removing a user’s ability to install them by removing their ability to access the Office Store and preventing them from installing trial applications and services in the Microsoft Admin Portal.
To confirm Word, Excel, and PowerPoint Add-in privileges in your environment, authenticate to your M365/Azure environment, browse to the following URL.
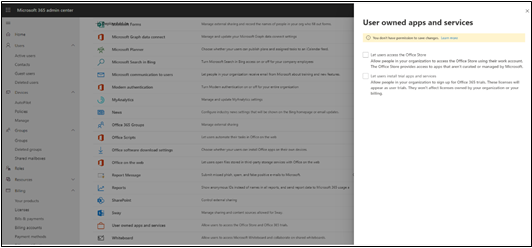
This URL is presented in the following screenshot. Select “User owned apps and services” and disable both "Let users access the Office Store" and "Let users install trial apps and services:"
Add-in Permissions for Word, Excel, PowerPoint
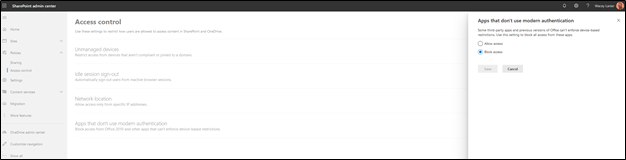
7. SharePoint Legacy Authentication - Legacy authentication in SharePoint uses only username and password for client access, effectively bypassing modern authentication mechanisms such as MFA. SecureSky recommends disabling legacy authentication in SharePoint to require modern authentication for client access requests.
To confirm Word, Excel, and PowerPoint Add-in privileges in your environment, authenticate to your M365/Azure environment, browse to the following URL.
A note on Basic & Modern Authentication for Exchange Online: Last year, Microsoft announced they would fully decommission Basic Authentication on October 13th, 2020. However, in their April 2020 update, Microsoft announced they are deferring this effort until 20201 in response to COVID-19. Microsoft will continue to disable Basic Authentication for newly created tenants by default and disable Basic Authentication in tenants that have no recorded usage starting October 2020. As disabling Basic Authentication can affect multiple points of authentication, SecureSky recommends investigating where Basic Authentication is being used and establish a plan for disabling and transitioning to close this attack vector. Update URL: https://techcommunity.microsoft.com/t5/exchange-team-blog/basic-authentication-and-exchange-online-april-2020-update/ba-p/1275508
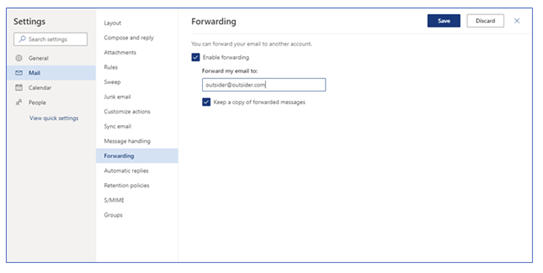
8. Disallow Forwards Outside of Organization - It is common for attackers to set up mail forwarding rules to auto-forward messages to an external mailbox, as presented in the following screenshot:Forwarding Enabled in User Account in Office 365
This forwarding intends to ensure that the attacker can see and archive inbound emails to compromised accounts, including any potential responses to phishing emails the attacker sends. Because of this risk, users should not be permitted to create auto-forwarding rules to inboxes that are not located within the organization.
The best approach to limit auto-forwarding in an environment can be dependent upon organizational needs. To learn more about approaches to limit e-mail forwarding in your environment, please refer to the SecureSky blog here.
9. Email Flow Phishing Customizations – Mail flow policies should be enforced to protect end-users from suspicious emails indicating possible phishing attempts and can be customized for different environments. The following rules should be considered for implementation in Office 365 environments:- Implement a mail flow rule that provides a notification to users when messages are received from outside the company, enhancing user awareness of messages that are internal vs. external.
- Where feasible, implement a rule that notifies the email recipient of the use of keywords associated with phishing and Business E-mail Compromise attacks. For instance, user warnings can be prepended to emails with attachments with filenames that include keywords “remittance,” “invoice,” “bill,” or “payroll” to ensure that the recipient is aware that these messages could potentially be phishing attacks.
- Where feasible, implement a rule that notifies the email recipient of the use of URL shorteners, which are used frequently in phishing attacks. For instance, user warnings can be prepended to emails that include URL shorteners, including “bit.ly,” “goo.gl,” and “tinyurl.com” to ensure that the recipient is aware that these messages could potentially be phishing attacks.
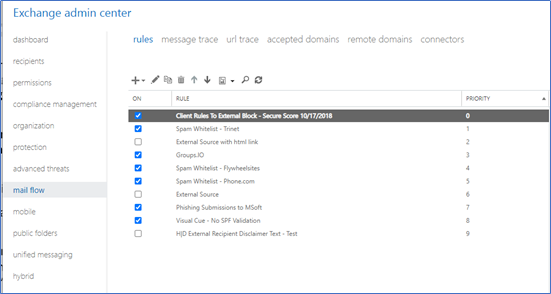
To review e-mail flow policy settings, access the following URL, then select “Mail Flow” and “Rules”:
URL to Access E-mail Flow Customization Settings
E-mail Flow Customization Settings
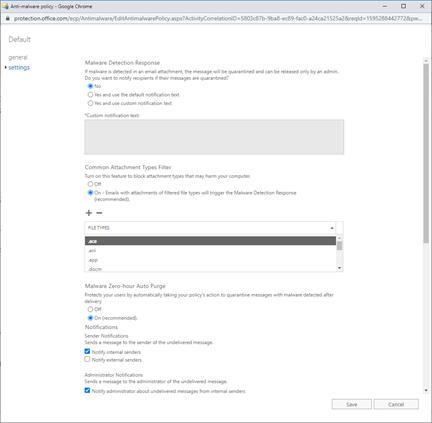
10. Anti-Malware Policy Customization - The anti-malware policy can be customized to align with current and unique threats to the environment. SecureSky recommends configuring the policy to:
- Notify admins when internal users are sending malware
- To prevent skipping outbound and inbound messages (for On-Prem Exchange Only)
- To delete malicious messages
- To block specific file types
- To enable Zero-Hour auto-purge
To review anti-malware policy settings, access the following URL:
URL to Access Anti-Malware Settings
Click on policy to edit, then select “settings” option in the anti-malware page are presented in the following screen shot:
Access Anti-Malware Settings
11. Mailbox Auditing - Mailbox auditing will track users accessing and performing actions within their own mailbox. Other mailbox statistics and telemetry data are also collected. When mailbox auditing is enabled, actions performed by administrators, delegates, and mailbox owners are logged by default. Starting in January 2019, Microsoft is turning on mailbox audit logging by default for all organizations. This means that certain actions performed by mailbox owners, delegates, and admins are automatically logged, and the corresponding mailbox audit records will be available when you search for them in the mailbox audit log. Before mailbox auditing was turned on by default, you had to manually enable it for every user mailbox in your organization. User, shared, and Microsoft 365 Group Mailboxes support this default mailbox auditing. However, resource, public folder, and the discovery search mailbox do not and must be enabled manually.
The following PowerShell can be utilized to ensure that mailbox auditing is enabled:
Mailbox Auditing PowerShell
Verify mailbox auditing is on by default (User, Shared, and MS 365 Group Mailboxes:
Get-OrganizationConfig | Format-List AuditDisabled
Identify mailboxes not covered by the default mailbox auditing:
Get-Mailbox -ResultSize Unlimited | Where-Object {$_.AuditEnabled -eq $false}
Remediate mailboxes identified in the above step:
Get-Mailbox -ResultSize Unlimited | Where-Object {$_.AuditEnabled -eq $false} | ForEach-Object {Set-Mailbox -Identity $_.PrimarySmtpAddress -AuditEnabled $true}
12. Office 365 Security Monitoring – Establishing an effective security event detection and response process is a core element of information security programs. SecureSky recommends creating custom alert policies that trigger on suspicious behavior and responding to alerts in a timely manner. Effective Office 365 Security Monitoring requires development and maintenance of an organizational process to escalate, analyze, and respond to alerts generated by Office 365 (outsourcing this process to a security service provider is another alternative).
Some characteristics to look for to confirm that effective Office 365 Security Monitoring is in place in an environment include:
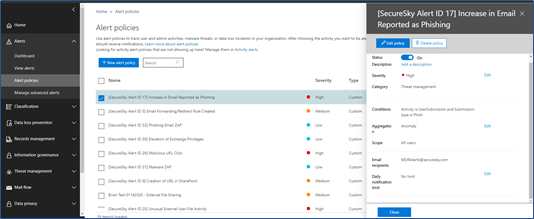
- Configure Alert Notifications - Ensure that alerts are configured to be e-mailed to all appropriate parties. To ensure alerts are configured to be escalated properly, access the following URL:
URL to Access Alert Configuration
From here, select an alert, and confirm that e-mail recipients are properly configured, as presented in the following screen shot:
E-mail Alert Recipient Configuration
- Investigate Alerts - Ensure that actions are being take in response to alert notifications. To do this, review alerts that have triggered in the environment, and ensure that they are being properly investigated, addressed, and closed.
URL to Access Current Alerts
Current Alerts

- Customize Alerts – Organizations that effectively monitor their environment will customize default Microsoft rules, as well as develop their own rules to detect potentially malicious activity. To review current alerts in the environment, access the following URL:
URL to View Current Alerts
Configuration of these 12 security controls builds a foundation for your organization’s Office 365 security configuration standard. While numerous security controls can be configured (SecureSky Office 365 Security Configuration Assessment checks for over 100 individual configuration settings), we believe these 12 controls, available at all license levels, are essential security controls for every Office 365 environment.
