Leveraging Azure Sentinel for Enhanced Security in Office 365 Environments
Sep 1, 2020 | Industry Insight
In today's digital workspace, safeguarding user accounts in Office 365 against compromises is a critical challenge for organizations. Azure Sentinel, Microsoft's premier cloud-native SIEM platform, plays a pivotal role in enhancing security measures within Office 365 environments. This blog post explores the native tools and techniques available through Azure Sentinel that organizations can leverage to effectively manage and investigate user account compromises.
Azure Sentinel: A Comprehensive Security Solution for Office 365
Microsoft Azure Sentinel offers a robust set of capabilities for monitoring and investigating suspicious activities and compromised accounts within Office 365. Despite the complexity and scattered nature of security tools, Azure Sentinel provides a centralized and intuitive solution for security operations teams.
Key Features of Azure Sentinel in Office 365 Security
1. Tracking Logins with Azure Active Directory Integration
Azure Sentinel integrates seamlessly with Azure Active Directory, providing invaluable insights into authentication activities. This integration is crucial for identifying unauthorized access attempts and patterns indicative of compromised accounts, such as unusual login locations, new IP addresses, and unexpected client application usage.
The first step of an account compromise investigation often begins with identifying the attacker and authenticating to the environment. Azure Active Directory Sign-in logs are the most important resource to identify this activity. (Please note: if your organization uses a third-party identity provider, like Okta or Duo, records from that provider should replace or supplement the steps presented in this section). Access Azure Active Directory sign-in
A screen shot of this page is presented below:
Azure Active Directory Sign in History
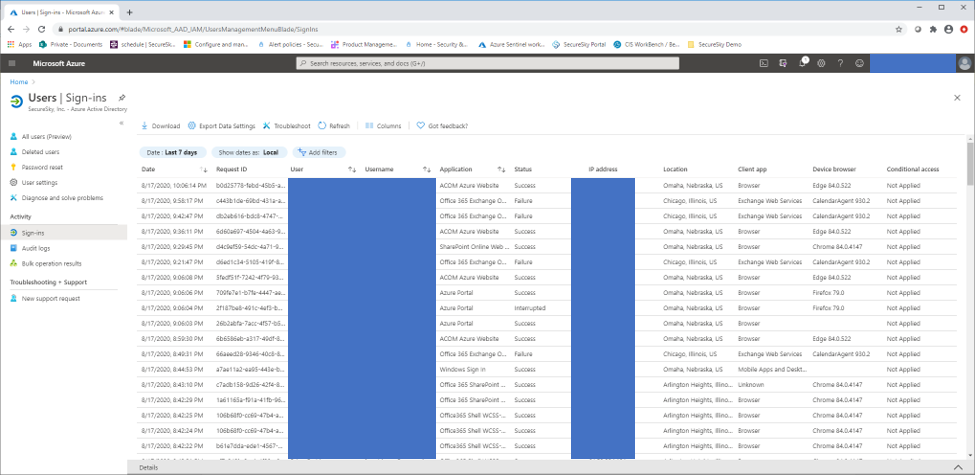
To analyze the data presented in this interface, use the integrated filters presented in the UI, or download the data to Excel for analysis. Unauthorized logins in an Azure Active Directory environment typically display one or more of the following characteristics:
- Connection from a different location – Attackers typically connect to environments from different physical locations than where victims usually authenticate from.
- Use of new IP address – Directly related to the above, the source IP address of an attacker connection will be different that addresses historically utilized by victims.
- Use of different Client Applications – many attacks against organizations that have two-factor authentication utilize legacy protocols, like IMAP and SMTP, that bypass two-factor authentication requirements. Wherever possible, organizations should ensure that legacy authentication has been disabled in their environment. A full list of legacy protocols used by Office365 is available at the following URL: https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/block-legacy-authentication.
- Changes to client operating system and browser – Users typically only connect from a limited number of different devices (e.g. a phone and a laptop), that have fairly static browser and operating system profiles, so that a login from a browser or operating system not previously seen merits investigation.
- Changes to authentication response patterns – Changes to response sequences, such as an increase in the volume of login failures, or an even an increase in the volume of successful logins can be potential indications of malicious behavior.
- Changes to IP address usage patterns – One account that is simultaneously authenticating from multiple IP addresses, or multiple accounts simultaneously authenticating from one previously unknown IP address can be an indication of malicious behavior.
- Changes to login days and times – Changes to login days and times, such as a user suddenly authenticating on weekends, or authenticating late at night can be an indication of malicious behavior.
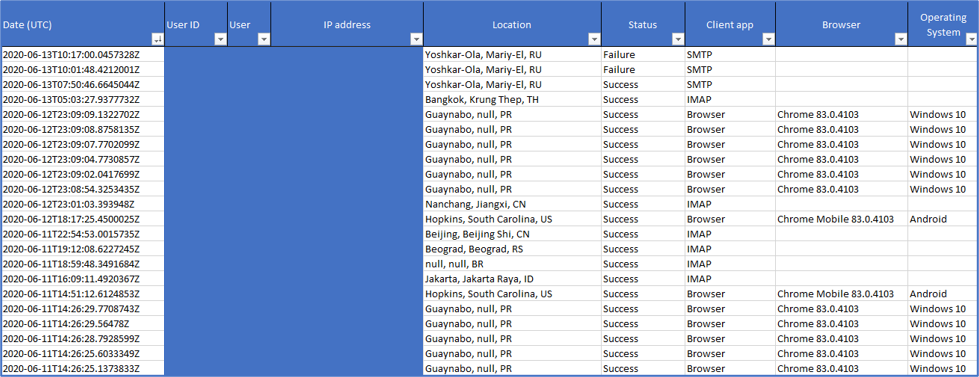
The following logs from a compromised user account demonstrate some of these characteristics:
- The user account began authenticating from a new address, in a new location – user’s standard logins from Puerto Rico (“Guaynabo, null, PR”)
- New client apps (IMAP and SMTP) were used – use of IMAP and SMTP are also reflected in Browser and Operating System fields being blank.
Azure Active Directory Sign In History from Compromised Account
2. Investigating with Office 365 Alerts
Azure Sentinel enhances the visibility of security alerts within Office 365, including suspicious email forwarding rules, abnormal external file sharing, and potential data exfiltration attempts. By aggregating and analyzing alerts, Azure Sentinel helps identify and respond to security incidents more efficiently.
If an account has been compromised, the activity may have triggered Office 365 alerts. These records are available in the Office 365 Protection Portal.
A screen shot of this menu is presented below:
Office 365 Alert Menu
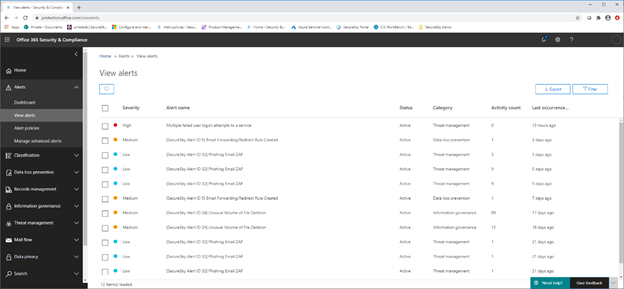
Key default alerts that may be indicative of an account compromise include:
- Email forwarding or redirect rule created – Attackers often make changes to Email forwarding and redirect settings when accessing a tenant, to hide their presence from the victim, as well as to ensure that the attacker has visibility into emails being sent to the victim.
- Unusual volume of external file sharing – An attacker may change file-sharing settings in an environment or upload their files to share.
- eDiscovery search started or exported – Attackers may look to take advantage of eDiscovery search capabilities in client environments to find potentially sensitive information in the environment.
- A Potentially Malicious URL click was detected – Clicking on a malicious URL sent to a victim may have been the event that triggered the incident.
Organizations can also establish custom alerts to detect potentially malicious actions specific to their tenant.
3. Unified Audit Log Analysis
The Unified Audit Log in Office 365, accessible through Azure Sentinel, is a goldmine for investigating the actions taken by a compromised account. Azure Sentinel facilitates the examination of SharePoint and Exchange Online activities, enabling organizations to trace the attacker's movements and impact within the environment.
If we have identified an account compromise from Azure Active Directory Sign-Ins and Office alerts, we need to identify what actions the attacker may have taken, both to maintain persistence in the environment, to attack other tenants, or to exfiltrate data from the victim environment. Logs associated with the activity that the attacker took in Microsoft Exchange and SharePoint Online are accessible in the Unified Audit Log.
A screen shot of this page is presented below:
Unified Audit Log
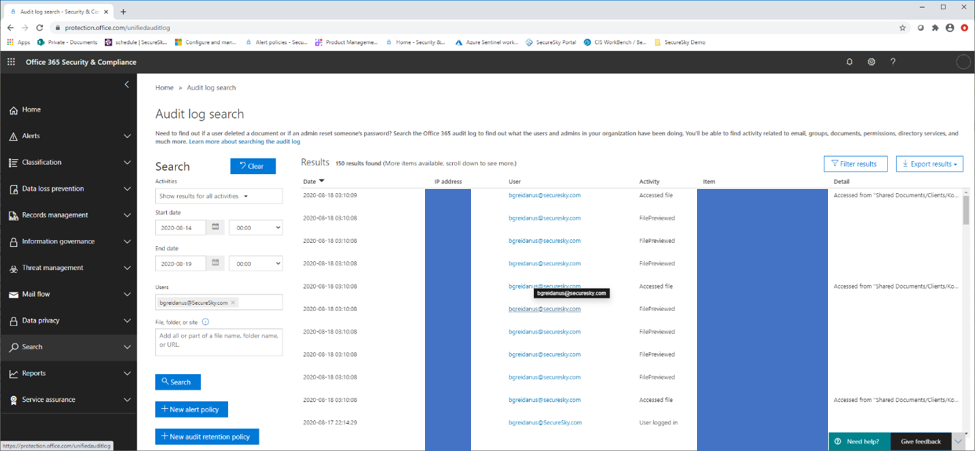
Please Note – if you access this URL, but don’t see any logs, you will need to enable audit logging.
Logs can also be exported from this menu. These logs are a combination of comma delimited and JSON by default. To parse them properly, follow the instructions here: https://docs.microsoft.com/en-us/microsoft-365/compliance/export-view-audit-log-records?view=o365-worldwide
Parsed logs from the unified audit log are presented in the following screen shot:
Parsed Logs From Unified Audit Log
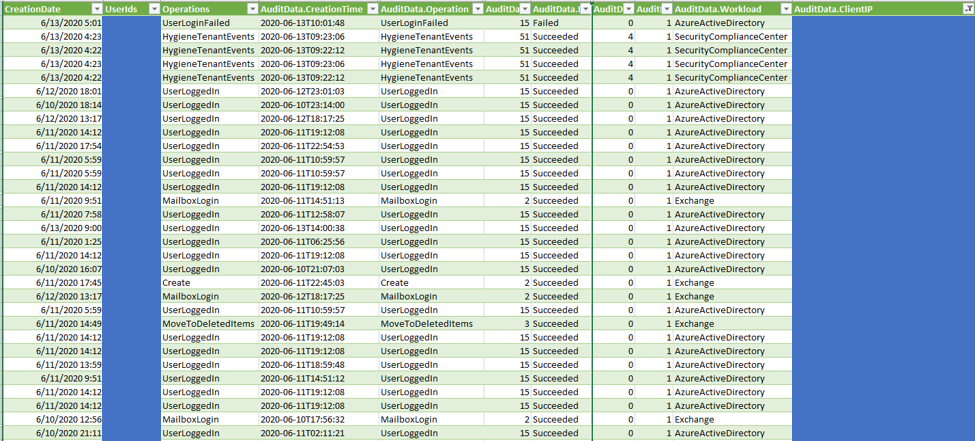
The Unified Audit Log can be used to trace SharePoint and Exchange online activities taken by the attacker in the environment.
4. Detailed Exchange Message Activity Review
Azure Sentinel's advanced analytics extend to monitoring email activities, helping to trace emails sent from compromised accounts. This capability is essential for understanding the scope of an attack and mitigating potential damages.
Message trace in the Security & Compliance Center follows email messages as they travel through your Exchange Online organization. Organizations can determine if a message was received, rejected, deferred, or delivered by the service. Message trace functionality in Office 365 is necessary if attackers send email messages using a victim's account. Visit the Email Message Trace menu.
This menu is presented in the following screen shot:
Email message trace menu
Microsoft provides the following overview for Email trace report types:
- Summary: Available if the time range is less than 10 days and requires no additional filtering options. The results are available almost immediately after you click Search. The report returns up to 20000 results.
- Enhanced summary or Extended: These reports are only available as downloadable CSV files, and require one or more of the following filtering options regardless of the time range: By these people, To these people, or Message ID. You can use wildcards for the senders or the recipients (for example, *@contoso.com). The Enhanced summary report returns up to 50000 results. The Extended report returns up to 1000 results.
Future Directions: Azure Sentinel's Role in Cloud Security
Looking ahead, Azure Sentinel is set to expand its capabilities, offering even more sophisticated detection and investigation tools for Office 365 and beyond. As organizations increasingly move their infrastructure and applications to the cloud, Azure Sentinel stands as a critical ally in securing digital assets against evolving threats.
Azure Sentinel represents a significant advancement in the fight against user account compromises in Office 365. By harnessing the power of Azure Sentinel, organizations can not only detect and investigate incidents more effectively but also enhance their overall security posture in the cloud. As we continue to explore Azure Sentinel's potential, its role in cloud security is undoubtedly poised for growth, offering a beacon of hope for organizations navigating the complexities of digital security.
Stay tuned for future posts where we will delve deeper into Azure Sentinel's additional security detection and investigation capabilities, further empowering organizations to safeguard their Office 365 environments against sophisticated cyber threats.
