Essential Office 365 Security Controls for Modern Workforces
Jun 10, 2020 | Industry Insight
In the wake of a shifting global workforce towards remote operations, the reliance on cloud-based services has surged. As Microsoft CEO Satya Nadella highlighted, the digital landscape has experienced a dramatic transformation, accelerating two years of digital change into a mere two months. This article aims to guide organizations newly adopt Office 365 or expand their use, ensuring a secure transition in this rapidly evolving digital era.
It's crucial to recognize that Microsoft's platform is continually advancing, and the security recommendations provided here are reflective of the most current best practices.
Implementing Foundational Security Controls in Office 365
This post outlines 12 critical security controls indispensable for every Office 365 environment. These measures are designed to mitigate risks associated with business email compromise (BEC), account takeovers (ATO), and unauthorized data access. The accompanying diagram demonstrates how strategic security configurations can interrupt the tactics employed by cybercriminals to infiltrate Office 365 environments. Each number in the cyber-attack lifecycle diagram correlates with one of the 12 foundational security controls, pinpointing the specific phase of a cyber attack that the control effectively counters.
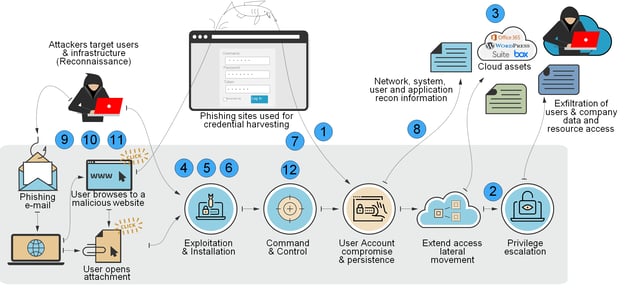
Optimizing Office 365 Security: Implementing Foundational Controls
Essential Security Practices for Office 365
Despite the unique ways organizations utilize Office 365, certain security controls are universally crucial. While higher-level Office 365 licenses (e.g., E3, E5 Security) offer additional security features, the foundational controls outlined here do not require advanced licensing. Yet, SecureSky's experience in cloud security posture management and incident response reveals a surprising gap: few organizations fully implement even these basic controls.
SecureSky's Essential Office 365 Security Controls
-
Multi-Factor Authentication (MFA) for Privileged Roles: The cornerstone of Office 365 security, MFA is vital for all users, especially those in privileged roles. It combines knowledge (password) with possession (mobile device access) to verify user identity. Prioritize MFA for Azure Active Directory privileged roles to prevent comprehensive system compromises.
-
Minimize Global Administrator Accounts: Limit superuser privileges by reducing the number of global administrators. SecureSky advises a review of these accounts to delegate less privileged permissions without sacrificing functionality, adhering to best practices of maintaining 3 to 5 global administrators.
-
Guest User Privilege Restrictions: Default settings allow unchecked guest access, increasing vulnerability. SecureSky recommends policies that restrict guest invitations to Admins and designated "Guest Inviters," limit guest permissions, and enforce "Collaboration Restrictions" to authorized domains only.
-
Third-Party Application Integration Controls: Default settings permit users to register potentially malicious applications. Administrators should oversee application registrations to safeguard organizational data.
-
Outlook Add-in Permissions: By default, users can install Outlook add-ins, potentially exposing email data. SecureSky suggests controlling permissible add-ins and restricting user installation capabilities through the "Default Role Assignment Policy."
-
Office Add-in Permissions (Word, Excel, PowerPoint): Similar to Outlook, default settings allow add-in installations in Word, Excel, and PowerPoint. SecureSky recommends limiting add-in installations and disabling access to the Office Store and trial applications via the Microsoft Admin Portal.
-
SharePoint Legacy Authentication Disabling: Legacy authentication methods bypass modern security mechanisms like MFA. SecureSky advocates for disabling legacy authentication in SharePoint to enforce modern authentication protocols.
Addressing Basic & Modern Authentication for Exchange Online: Microsoft's postponement of Basic Authentication decommissioning due to COVID-19 requires organizations to assess and plan for the transition to modern authentication methods to mitigate security risks.
- Disallow External Mail Forwards: Attackers often use mail forwarding rules to divert messages externally. SecureSky advises against allowing users to create auto-forwarding rules to external mailboxes to prevent data leakage.
Forwarding enabled in user account in Office 365
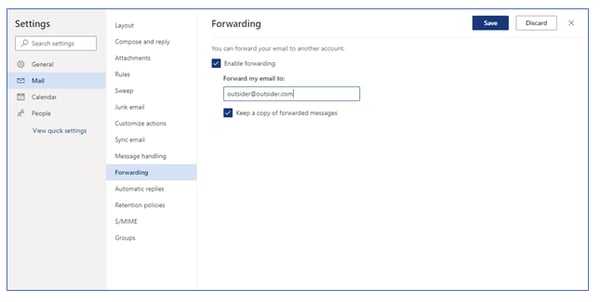
The intent of this forwarding is to ensure that the attacker can see and archive inbound emails to compromised accounts, including any potential responses to phishing emails the attacker sends.
Because of this risk, users should not be permitted to create auto-forwarding rules to inboxes that are not located within the organization. To learn about the best way to limit email forwarding in your environment, please refer to the SecureSky blog here.
9. Email Flow Phishing Customizations – Mail flow policies should be enforced to protect end-users from suspicious emails indicating possible phishing attempts and can be customized for different environments. The following rules should be considered for implementation in Office 365 environments:- Implement a mail flow rule that provides a notification to users when messages are received from outside the company, enhancing user awareness for messages that are internal vs. external.
- Where feasible, implement a rule that notifies the email recipient of the use of key words associated with phishing and Business E-mail Compromise attacks. For instance, user warnings can be prepended to emails with attachments with filenames that include keywords “remittance,” “invoice,” “bill,” or “payroll” to ensure that the recipient is aware that these messages could potentially be phishing attacks.
- Where feasible, implement a rule that notifies the email recipient of the use of URL shorteners, which are used frequently in phishing attacks. For instance, user warnings can be prepended to emails that include URL shorteners, including “bit.ly,” “goo.gl,” and “tinyurl.com” to ensure that the recipient is aware that these messages could potentially be phishing attacks.
11. Mailbox Auditing - Mailbox auditing will track users accessing and performing actions within their own mailbox. Other mailbox statistics and telemetry data are also collected. When mailbox auditing is turned on, actions performed by administrators, delegates, and mailbox owners are logged by default. SecureSky recommends reviewing the actions that can be audited to potentially identify common indicators or compromise; listed at the following URL: https://docs.microsoft.com/en-us/microsoft-365/compliance/enable-mailbox-auditing.
12. Office 365 Security Monitoring - Office 365 Security Monitoring enables response to security alerts that are generated. Default alert policies allow events to go unnoticed. SecureSky recommends creating custom alert policies that trigger on suspicious behavior and responding to alerts promptly.
Understand Office 365 Security Controls
Configuring these security controls builds a foundation for your organization’s Office 365 security configuration standard. While numerous security controls can be configured (SecureSky Office 365 Security Configuration Assessment checks for over 100 individual configuration settings), we believe these 12 controls, available at all license levels, are essential to implement in any Office 365 environment.
SecureSky works closely with law enforcement, proprietary BEC threat-sharing consortiums, and leading security, and compliance standards organizations, and has extensive experience helping clients secure and monitor Office 365 environments. To learn more about some of the work we have done for clients, and recommendations for improving Office 365 security, please see our website and blog series on Office 365 Business Email Compromise here.
Look to our next blogs in this series for guidance on how to enable and configure these 12 security controls to defend against growing and evolving cyber-attacks.
