Maximizing Office 365 Security: Implementing Comprehensive Controls
Apr 21, 2020
In the digital age, Office 365 security and safeguarding your environment is paramount. This guide delves into the essential security controls necessary to protect against prevalent threats such as Business Email Compromise (BEC), Account Takeover (ATO) attacks, and unauthorized data access. With Microsoft's platform continually evolving, the strategies outlined here adhere to the most up-to-date best practices.
If you have created a new Office 365 tenant recently, or if you administer an Office 365 environment, you may have noticed a few changes.
First – as you can see in the following screenshots, new tenants are created with ‘Security Defaults’ enabled:
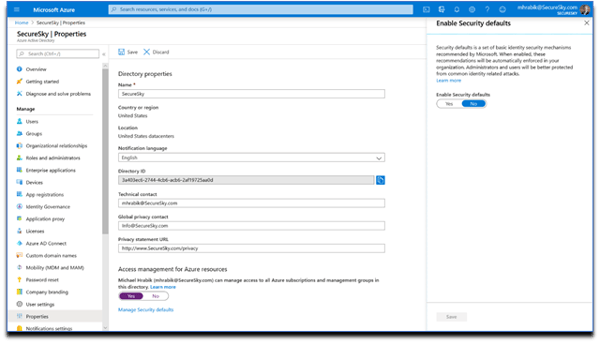
Second, users of Azure Active Directory will see that some baseline conditional access policies have been deprecated and can no longer be used, as presented in the following screenshot:
So – what are ‘Security Defaults’, and why are some legacy features being deprecated now?
Evolving Azure Active Directory Security: A Leap Forward with Security Defaults
On January 9th, Microsoft took a significant step in bolstering Azure Active Directory (AAD) security by introducing Security Defaults. This initiative builds on the foundation laid in 2012 when Microsoft's Identity Protection team began setting stringent security standards for consumer accounts, including personal emails, Xbox, and Skype. These standards encompassed multi-factor authentication (MFA), access challenges upon detecting abnormal activity, and mandatory password resets following breach exposures.
The impact of these measures has been profound, leading to a sixfold reduction in account compromise rates. Remarkably, despite the growing user base, Microsoft accounts have never been more secure.
In 2014, Microsoft extended these advanced security technologies to Azure Active Directory organizational customers, demonstrating their effectiveness in the corporate realm. Microsoft's data reveals that implementing MFA and disabling legacy authentication could prevent over 99.9% of organizational account compromises. Furthermore, Google's research supports these findings, showing that account recovery measures, including MFA, can thwart up to 100% of automated bots, 99% of bulk phishing attacks, and 66% of targeted attacks (Source: Google Security Blog).
However, the challenge remains in the widespread adoption of these critical security controls. Despite Microsoft's concerted efforts to promote MFA, only about 9% of organizational users have encountered an MFA prompt, indicating a significant gap in the adoption of essential security measures.
At SecureSky, our observations mirror Microsoft's findings. Across various client sectors, we've noted a consistent lack of improvement in security postures, as evidenced by stagnant Secure Scores. This underscores the urgent need for organizations to embrace and implement the available security technologies to safeguard their digital environments effectively.
CSP/MSP Secure Score Average
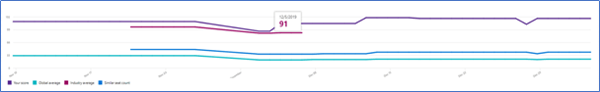
Manufacturing Secure Score Average

Healthcare Secure Score Average
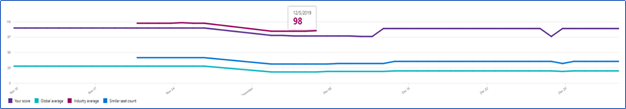
Security Defaults
Microsoft needed to take a different tack – to protect organizational accounts just like they do with consumer accounts. Security Defaults provide secure default settings that Microsoft manages on behalf of organizations to keep customers safe until they are ready to manage their own identity security.
What are Security Defaults? To begin, Microsoft is doing the following:
- Requiring all users and admins to register for MFA.
- Challenging users with MFA - mostly when they show up on a new device or app, but more often for critical roles and tasks.
- Disabling authentication from legacy authentication clients, which can’t do MFA.
These controls are intended for organizations that are not configuring their own security. If you have configured security settings in your own environment, Microsoft isn’t going to jump in and change your settings – clients that are already using Conditional Access will not see Security Defaults implemented in their tenant.
A Great Step Forward in Office 365 Security
SecureSky is happy to see Microsoft enforcing Multi-factor Authentication as part of Security Defaults. It is a critical control for securing Office 365 environments.
The big question is will companies respond to Microsoft’s nudge to securely configure your O365 and Azure environment, hopefully, history isn’t an indicator.
However, Multifactor Authentication is not a silver bullet. With the wider adoption of MFA, we anticipate seeing more attack techniques designed to circumvent it. Multi-factor Auth protects against password guessing or brute-force attacks and credential disclosure via data breaches. However, it is critical to remember that any authentication that relies on something the user knows and types in can be phished. Attacks against MFA include:
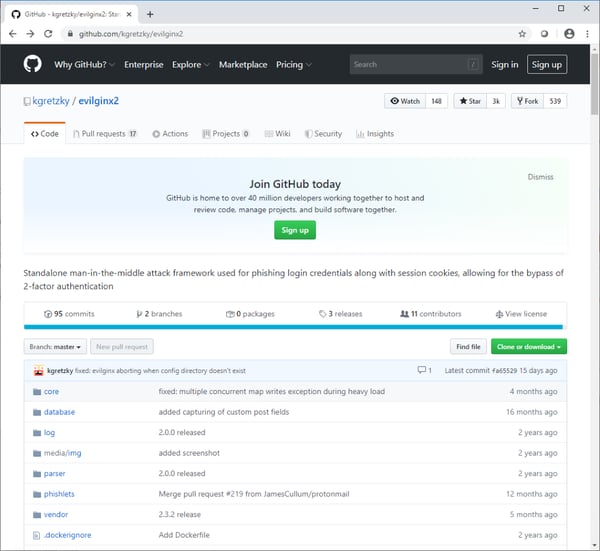
Man-in-the-middle frameworks – There are several open source projects that exist to help attackers build infrastructure to sit between a victim and MFA websites, so that the attacker can steal all tokens and take over sessions. A screenshot of the Github repository for a popular framework is presented in the following screenshot:
MFA attack approaches include:
SMS Phishing attacks – Social engineering of users
SIM Swap Attacks – Social engineering of provider to change SIM/phone linkage
Compromised Endpoint Attacks – Attack can steal session credentials and start second sessions.
Login Recovery Attacks – Can bypass MFA to recover account, potentially change user settings.
Attacks that use these techniques are often highly targeted. For example, a SIM swap attack was recently used to compromise the account of Twitter CEO Jack Dorsey and SMS.
Going beyond MFA
While Default Security is a great first step by Microsoft, organizations must take it upon themselves to extend the security controls implemented in their cloud environments.
- Organizations must properly configure and harden their entire O365 environment. Recommendations of key settings to implement in Office 365 environment are presented in the following SecureSky blog posts. Additionally, we recommend that organizations evaluate the comprehensive controls provided in the Center for Internet Security Microsoft 365 Foundations Benchmark, to which SecureSky contributes.
- Enablement of effective detection capabilities in O365, as well as timely monitoring and analysis of detected threat events.
As always if you have more questions about Microsoft Security Defaults please feel free to reach out to us any time. info@securesky.com
