For small and medium-sized businesses (SMBs), the cybersecurity landscape has shifted dramatically. Threat actors no longer discriminate by company size; they target vulnerabilities wherever they...


For small and medium-sized businesses (SMBs), the cybersecurity landscape has shifted dramatically. Threat actors no longer discriminate by company size; they target vulnerabilities wherever they...

In today’s digital-first world, LinkedIn has become a critical platform for professionals to network, share insights, and discover opportunities. But attackers are taking notice, and they’re using...
SecureSky has been named in the 2025 Frost Radar™ for Managed Detection and Response, recognized for pioneering the integration of Continuous Threat Exposure Management (CTEM) into traditional MDR...
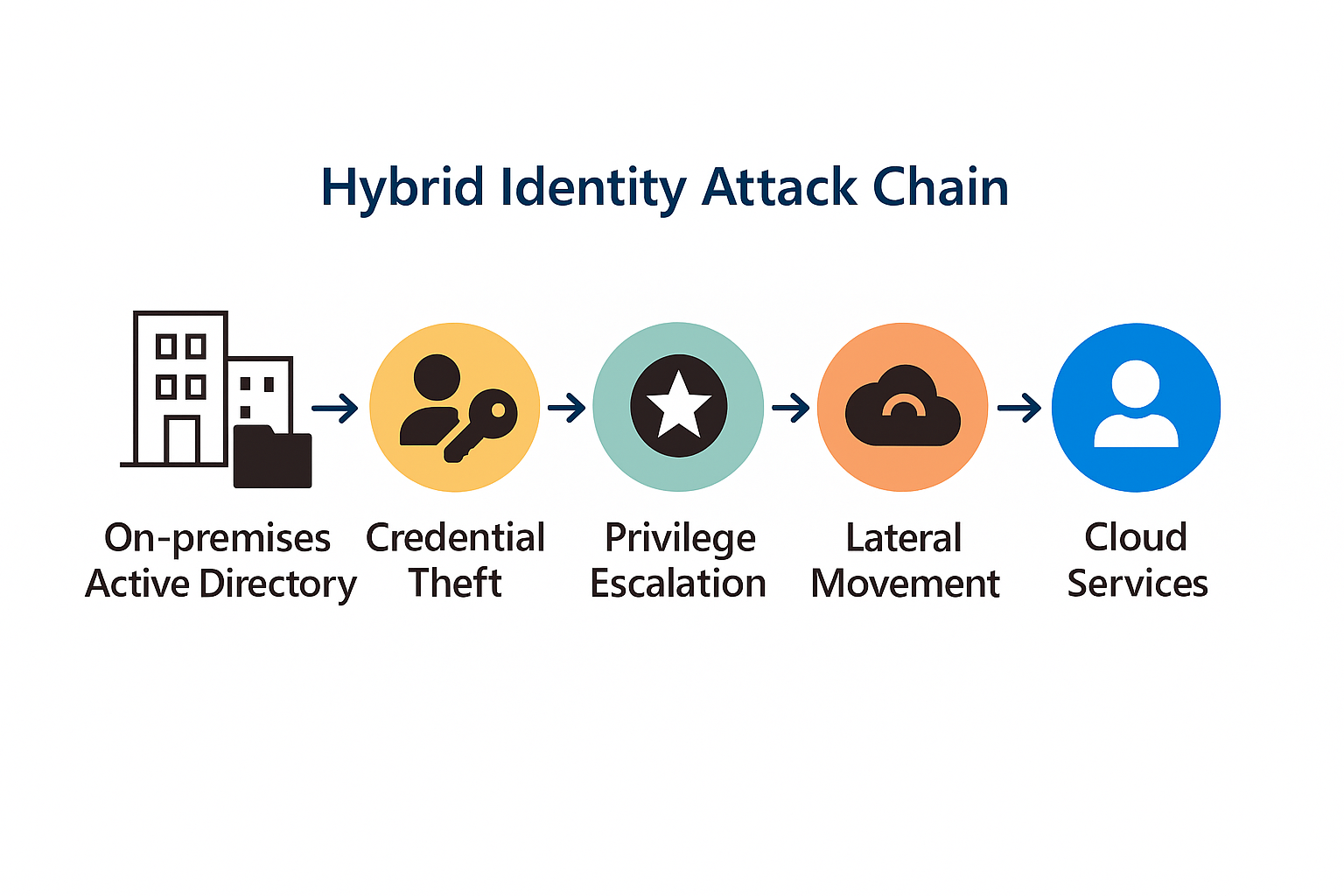
The move to the cloud has reshaped the cybersecurity landscape, shifting our focus to SaaS applications, cloud infrastructure, and the identities that access them. But for many organizations, the...

Ross Haleliuk’s recent post on Venture in Security offers one of the most comprehensive visualizations of cybersecurity consolidation to date. His breakdown shows how over 200 companies have merged,...

In today’s data-driven world, organizations are swimming in information—across clouds, apps, and platforms. Microsoft Purview offers a unified solution to help you discover, classify, protect, and...

Microsoft Sentinel delivers powerful security capabilities—but many organizations struggle with its unpredictable cost structure.
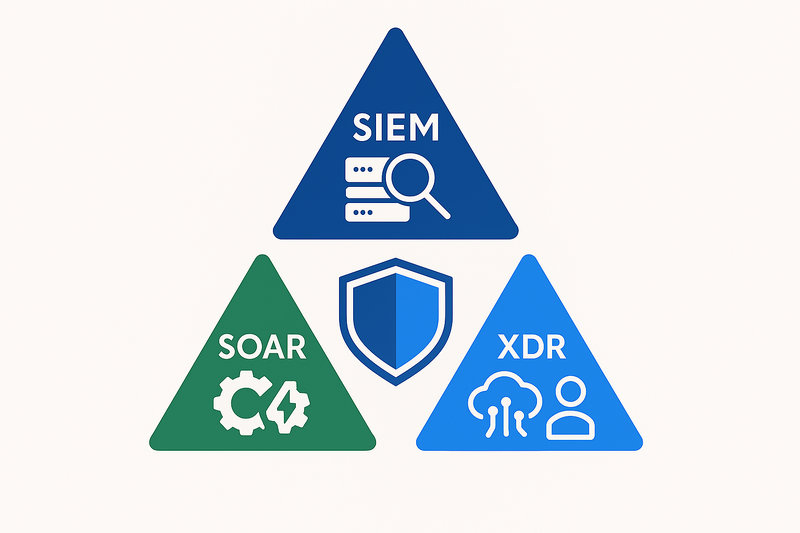
In previous blogs, we’ve explored Microsoft’s evolving branding for security tools, but we continue to get questions—especially around how Microsoft Sentinel (SIEM/SOAR) and Microsoft Defender XDR...
Microsoft will retire the Microsoft Monitoring Agent (MMA), also known as the Log Analytics Agent (OMS), on August 31, 2024, and replace it with Azure Monitor Agent (AMA). File Integrity Monitoring...

The cybersecurity landscape is in a constant state of flux, with new threats emerging at an alarming pace. As technology advances, so do the methods employed by cybercriminals, making the digital...