SecureSky 2023 Mid-Year Azure Compliance Trends
Jun 22, 2023
In this blog, we delve into the security configurations within Microsoft Azure, leveraging insights from SecureSky's Multi-Cloud Threat Exposure Management (CTEM) Platform for the years 2022-2023. Our analysis spans clients from various industries, encompassing both recent and mature hybrid cloud environments.
Our platform assessed client security configurations against industry standards, benchmarks, and regulatory requirements to set a baseline for security enhancement efforts. It's important to note that our initial assessments often reveal a lower security posture, as many clients turn to SecureSky seeking assistance in bolstering their security measures.
Interestingly, our findings predominantly show that configurations tend to stick close to Azure's default settings, mirroring the Microsoft Secure Score averages seen across Microsoft’s clientele. This observation suggests a widespread need for heightened security awareness and action across Azure deployments.
Regardless of whether you're in the early stages of cloud adoption or managing a complex, mature environment, our insights can highlight critical security gaps needing attention.
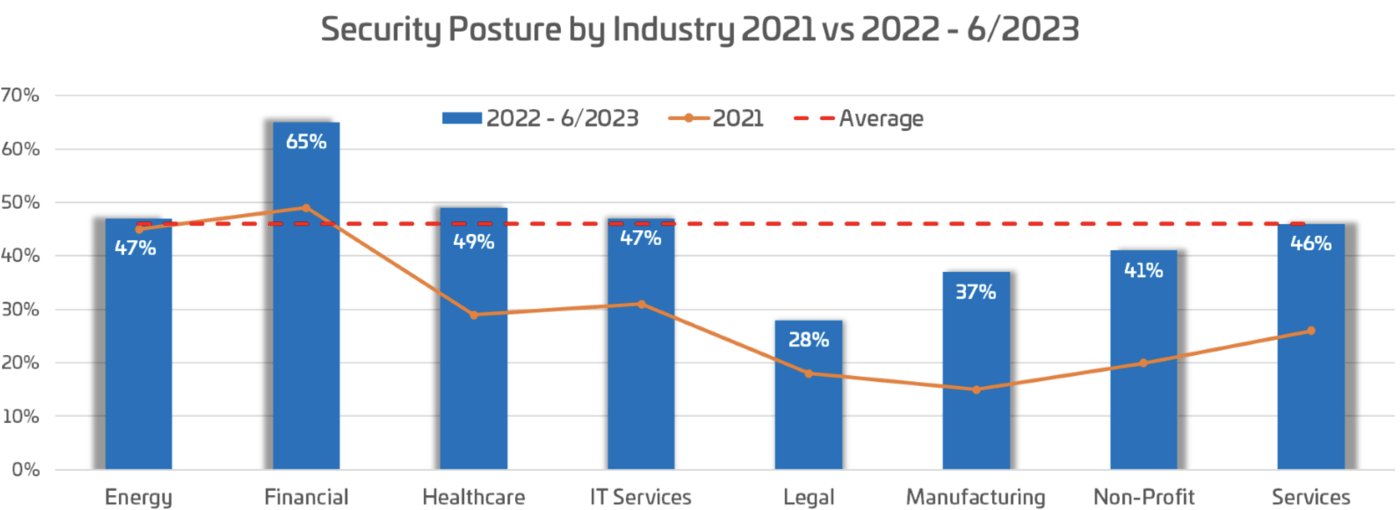
Year-over-year, we've observed incremental improvements in adherence to security best practices across all sectors, with the average compliance rate rising to 45% in 2022 from 37% in 2021. Despite these gains, there remains a significant gap in achieving optimal security configurations, as evidenced by the underperformance of certain industries against established best practices. These findings, consistent with Microsoft Secure Score averages, underscore the prevalent challenge of securing Azure environments effectively.
Key Findings Snapshot - 2022
Visibility
-
Cloud visibility has doubled since 2021 (17% to 38.5%), still leaving a 61% coverage gap
-
Only 10% of serverless resources have granular logging and protection policies enabled
Identity Management
- 77% of accounts use weak authentication (SMS)
- Fewer than 11% of accounts use phishing-resistant MFA
Privileged Management
- 30% of accounts are over-privileged
- Under 20% of priviliged accounts are using Just-in-Time access
Microsoft XDR
- 95% of clients are considering consolidating to Microsoft's XDR to reduce cost
- Less than 50% of the Microsoft XDR capabilities are utilized
Cloud Resources
- 62% of VMs don't follow best practices configurations
- 90% of authentication keys are exposed
- 70% of companies do not manage application connections and privileges
Azure Compliance: Key Security Trends Analysis
Throughout 2022 and into the first half of 2023, SecureSky has closely monitored the cybersecurity landscape, responding to an uptick in cyberattacks, new governmental regulations, stringent insurance protocols, and the shift toward more secure authentication practices. This blog highlights overarching security trends SecureSky has pinpointed within Azure environments, focusing on broader security categories rather than isolated incidents or findings. Our approach normalizes data for a comprehensive analysis, aligning our findings with the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) to offer actionable insights.
Key Security Categories Analyzed:
- User and API Access / Identity and Entitlements: Examining how users and applications interact with and access Azure resources.
- Data Storage and Access Controls: Assessing the security measures in place for moderndata storage and access within Azure.
- Application Configuration: Reviewing configurations of Azure applications for potential security enhancements.
- OS / Containers: Analyzing the security posture of operating systems and containerized applications in Azure.
- Network Security: Evaluating the network security measures implemented to protect Azure environments.
Additionally, our recommendations are categorized according to the NIST CSF functions: Identify, Protect, Detect, Respond, and Recover. This structured approach allows us to provide targeted advice for improving Azure compliance and security across these critical areas.

In-Depth Analysis: Enhancing Cloud Security and Compliance
SecureSky's comprehensive review of security program pillars within the cloud stack, adhering to the "shared responsibility" model, has unearthed pivotal insights into the evolving landscape of cloud security and compliance.
Key Findings:
-
Enhanced Logging and Monitoring: There's been a notable 2x increase in the logging and monitoring of traditional cloud components such as VMs, networks, and security products compared to last year. This improvement reflects a growing response to the surge in cloud-targeted attacks and new compliance mandates.
-
Gaps in Serverless Resource Monitoring: Despite advancements, monitoring for serverless resources, automation, configuration drifts, and the validation of native controls remain underutilized. Many organizations transitioning to the cloud fail to fully leverage cloud-native auditing, detection, and automation tools, missing out on crucial visibility and protection against threats like lateral movement, and unauthorized access to keys/secrets and SaaS activities.
-
Secure Application Configuration: A significant leap from 13% in 2021 to 48% in 2022/23 in secure application configuration demonstrates a heightened focus on securing SaaS and workload-hosted applications, including M365, Salesforce, and ServiceNow. This shift, driven by the need to combat phishing and credential theft, is further supported by a 15% improvement in the secure configuration of Cloud VM and Network infrastructure.
-
Legacy Protocols and MFA Enforcement: Organizations are actively replacing outdated protocols and enforcing Multi-Factor Authentication (MFA) as the expansion of SaaS Applications and remote work becomes standard. Despite the widespread adoption of Conditional Access Policies (CAP) to streamline MFA implementation, 79% of organizations still fall short of best practices in account management and strong authentication, leaving them vulnerable to account takeovers.
Modern IT Environment Challenges:
Today's IT environments demand a proactive cybersecurity approach to threat and exposure management, emphasizing real-time visibility and control validation. SecureSky's analysis underscores the necessity of addressing common pitfalls in account management and authentication to align with cloud security best practices.
For further insights, explore our detailed analyses on Microsoft Legacy Authentication Deprecation and Multi-Factor Authentication Effectiveness.
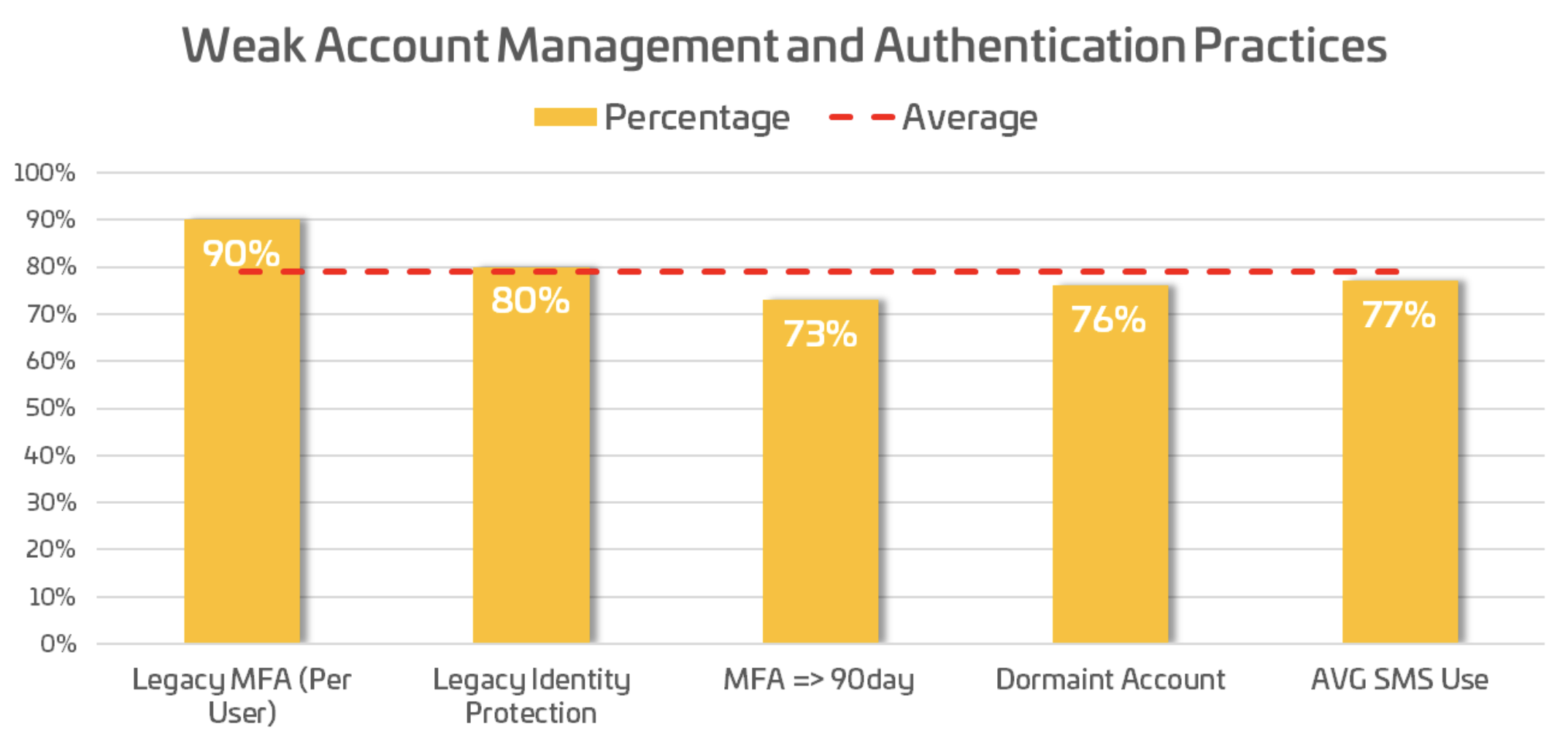
[caption] 79% of organizations failed in basic account management, and enforcement of strong authentication led to compromises.
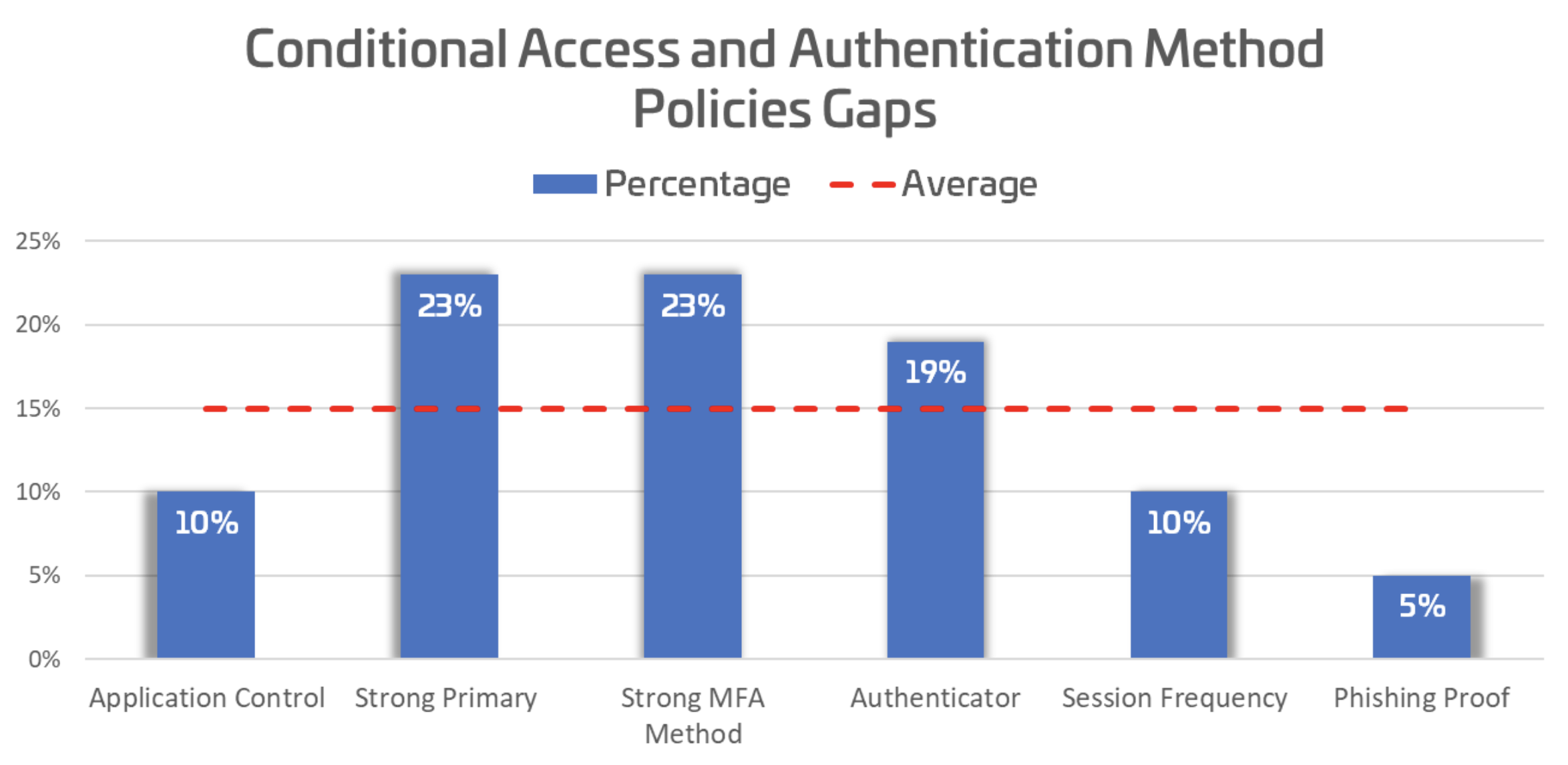
[caption] 15% adoption of strong authentication and access control exposes organizations.
Addressing Gaps in Cloud Security Configuration Management
Despite noticeable improvements over the past year, the challenge of achieving fully hardened security configurations within the cloud stack remains. This issue is particularly evident when examining the "shared responsibility" model adopted by many cloud service providers.
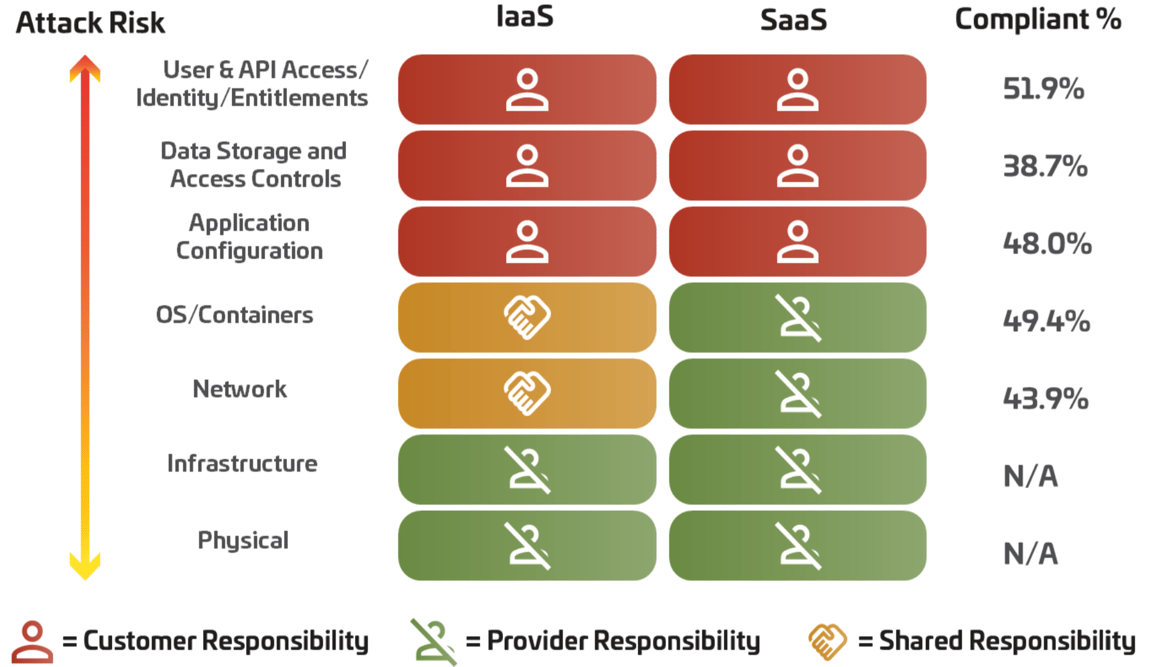
Understanding Shared Responsibility in Cloud Security:
The graphic below illustrates how the responsibility for security controls shifts across the cloud stack. As we move upwards, from infrastructure layers to user and application levels, the customer's share of the security responsibility increases. This model places the onus on customers to secure User & API Access, Identity and Entitlements, Data Storage and Access Controls, and Application Configuration.
Current State of Security Configurations:
Although there's been a 16% improvement in security configurations since last year, it's both surprising and concerning that the average percentage of adequately hardened security configurations in areas where customers hold responsibility still lingers around 50%. This statistic underscores a critical need for organizations to reassess and strengthen their approach to cloud security, ensuring that configurations are robust and in line with best practices.
Moving Forward with Enhanced Cloud Security:
To navigate the complexities of the shared responsibility model and improve cloud security posture, organizations must prioritize comprehensive security configuration management. This involves regular reviews, updates, and adherence to industry standards and best practices for all elements within the cloud stack under their control.
By addressing these gaps, organizations can better protect their cloud environments against evolving threats, ensuring a more secure and resilient cloud infrastructure.
2022-23
We also evaluated the NIST categories (functions) as they align with our assessment findings:
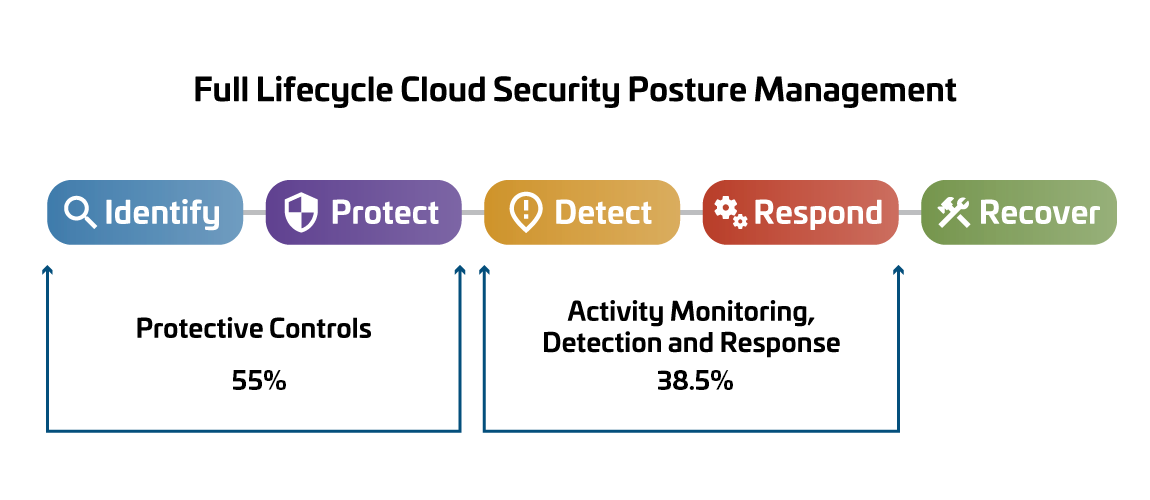
Enhancing Cloud Security: Progress and Challenges
Identify and Protect
Over the past year, there has been noticeable progress in the realm of client-protected controls, with an increase from 34% in 2021 to 55% in 2022/23. This improvement reflects the ongoing efforts to adapt to rapid cloud developments, security enhancements, and the dynamic nature of cyber threats.
Detect and Respond
Despite advancements, challenges persist in achieving comprehensive visibility within modern cloud infrastructures. While general activity logging saw a significant rise from 17% to 38.5%, visibility into modern cloud infrastructure remains low at just 9.8%. This gap underscores the complexities of monitoring and interpreting activities within contemporary cloud environments. To bridge this gap, organizations are increasingly leveraging Microsoft's native controls and the Defender suite of products. However, it's noted that only about half (50.2%) of these product features are currently aligned with security best practices.
Microsoft's Evolution in Security Solutions
In recent years, Microsoft has emerged as a formidable force in the security sector, thanks to its extensive portfolio of email, productivity tools, the Windows operating system, Azure, and numerous security acquisitions. This strategic expansion, coupled with Microsoft's ability to analyze trillions of security signals and protect billions of systems daily, positions it as a leader in various security domains. This transformation didn't happen overnight; Microsoft has been laying the groundwork and developing its security tools for over a decade.
As Microsoft Security continues to evolve, there have been several changes to branding, product categories, names, and licensing options. Despite these changes, the core strength of Microsoft Security remains its integrated approach to managing identity, device, and multi-cloud security controls and threat detection.
Microsoft's Integrated Security Suite
Microsoft's current suite of XDR/Defender services, including Microsoft XDR, Azure AD, and Microsoft Sentinel, exemplifies their commitment to providing a comprehensive security solution. This suite represents a unified approach to securing identities, devices, and cloud environments against a backdrop of increasing cyber threats.
Below illustrates the deployment summary of the Microsoft XDR suite configuration compared to the security best practices settings.
Learn more about The Modern Enterprise-Level Security Stack in our free eBook (securesky.com). For more information on the Microsoft Security Suite, check out our blog to dive into the various Microsoft Defender technologies.
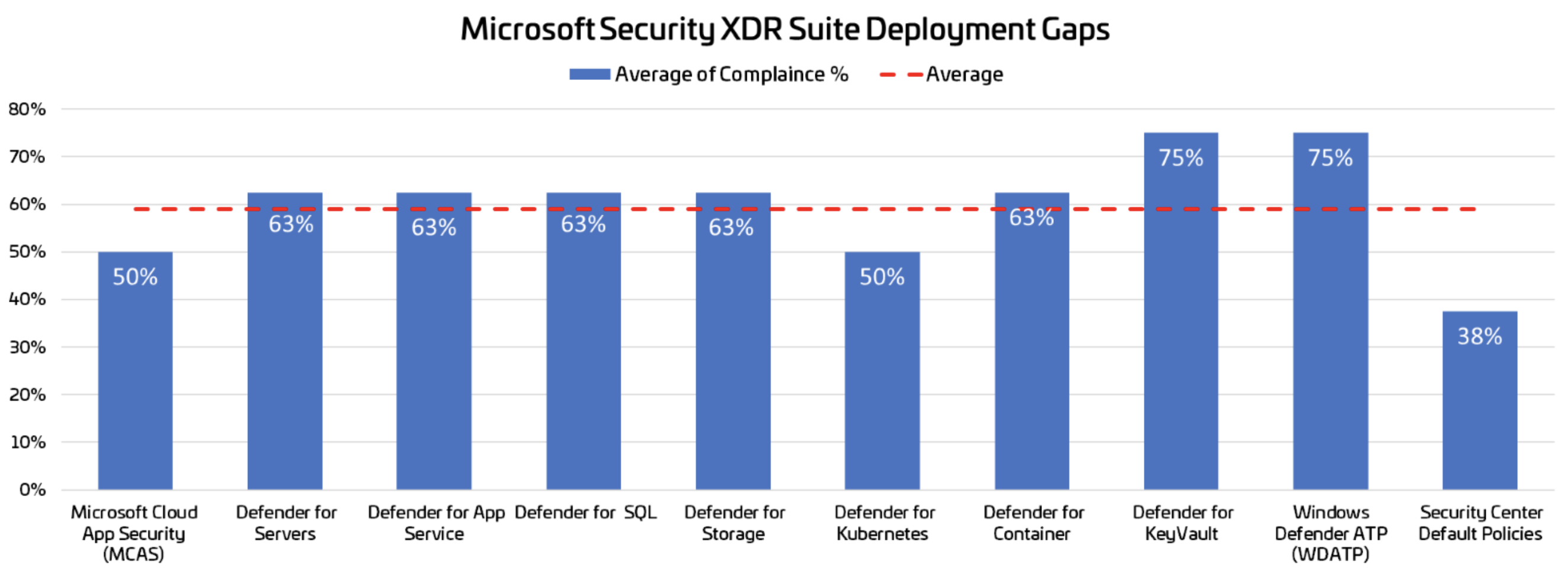
[caption] Only 58.2% of the Installed Defender is configured according to security best practices.
Navigating Cloud Security Challenges
SecureSky has observed a promising trend towards strengthening cloud infrastructure security, spurred by insurance requirements, compliance demands, and government directives. Despite the eagerness of security teams to implement new security solutions and features, the fast-paced evolution of cloud environments, coupled with resource constraints, presents significant challenges and potential vulnerabilities.
While incremental progress in security hardening is evident, overarching policies that are either too broad or flawed, along with partial implementations, continue to place cloud environments at considerable risk.
Persistent vulnerabilities in Activity Monitoring, Detection and Response, and configurations across the cloud stack, as outlined in the "shared responsibility" model, highlight critical areas of concern. The most significant gaps were identified in Identity and Access Management, Key Management, Application Logging, and Security Product Configuration. These areas offer the greatest potential for organizations to enhance their cloud security posture and mitigate risks effectively.
SecureSky's insights underscore the importance of a comprehensive approach to cloud security, emphasizing the need for continuous monitoring, robust identity management, and strategic deployment of security solutions. As organizations navigate the complexities of cloud security, prioritizing these key areas will be crucial in building a resilient and secure cloud infrastructure.
Recommendations
Throughout this blog, we have stressed the importance of proper configuration and visibility as part of your tactical roadmap. With the dynamic nature of cloud environments, we also stress the importance of continuous assessments to ensure the ongoing validation of security-hardened configurations.
For more strategic recommendations, see our eBook, The Modern Enterprise-Level Security Stack, which includes the following recommendations apply to securing all cloud environments:
- Understand the capabilities and roadmaps of security tools and audit settings available from your cloud provider(s) compared with your current security technology stack. In cloud migration planning and deployments, incorporate security measures in your strategies. Base your future-state objectives on proven and peer-reviewed configuration standards like Center for Internet Security (CIS) benchmarks.
- Review your existing cloud licensing to find redundant functionality you may be paying for twice. This redundancy may be between your legacy security technology stack and cloud-native functionality included with your current licenses. Determine if the tools available provide adequate cloud coverage to assess risk or security control status in real-time and offer automation capabilities for security posture management enforcement and threat response.
- Develop, deploy, validate, and improve your modern security architecture, extending your zero-trust model to include cloud resources, and invest in training and optimizing security controls to detect, investigate and respond to threats using new automated techniques. Roadmap continuous improvement into your control schema, for example moving from weak to stronger MFA methodologies.
- Reference Link: https://blog.securesky.com/zero-trust-maturity-model-ztmm-2.0-a-transition-to-zta
- Reference Link: https://blog.securesky.com/zero-trust-maturity-model-ztmm-2.0-a-transition-to-zta
- Extend your enterprise risk program to include data flows and other risk factors associated with each cloud environment, for example, authentication policies, access controls, file sharing, guest users, and application connections. Expand your exposure management practices to include Cloud Security Posture Management (CSPM), SaaS Security Posture Management (SSPM), and, most importantly, control and policy validation. In terms of continuous control validation, ensure your controls are not only in place but also effective, for example measuring how often users are asked to MFA based on their privileges and blast radius.
- Train corporate leaders and Board members on their upcoming regulatory and compliance requirements related to enterprise and cloud security. As discussed throughout this paper, major IaaS and SaaS providers are or will soon be more secure than on-premises solutions because they tightly integrate operational and security tools, automate functions that were once almost exclusively manual, and collect and apply massive amounts of threat intelligence. The caveat to this, of course, is the ability of IT and security practitioners to take advantage of these capabilities.
Appendix
User and API Access / Identity and Entitlements
This category covers users, user permissions, Azure Active Directory settings, groups and roles, Multi-Factor Authentication settings, guest users, and their permissions, among a few settings assessed. Identity and Access Management (IAM), controls to ensure approved individuals can access specific resources at certain times, is a subcategory in this category.
Data Storage and Access Controls (including Key Management)
This category compares SQL Server, PostgreSQL, and MySQL settings against industry best practices, ranging from encryption settings for databases, firewall rules, network access, Azure Key Vault, Kubernetes, resource locks, and security-related settings within the Microsoft Azure Storage Account service.
Application Configuration
This category covers security-related settings with the Microsoft Azure Application Service and includes everything from programming language version support, remote file transfer configuration, and application secrets storage settings.
OS / Containers
Settings within this category pertain to virtual machine disk encryption settings, patching and updates, virtual machine extension provisioning, and general virtual machine security settings.
Network Security
This category looks at Network Security Group rules for misconfigurations, default rule settings, and remote protocol-specific configuration settings.
Protective Controls
Settings within this category look at whether an organization subscribes to the extra security settings as part of the standard tier and whether an organization takes full advantage of the various settings within this area of Microsoft Azure. This includes Microsoft (Defender for Cloud, Microsoft Defender Endpoint, Defender for Storage, etc.), third-party products, and cloud-native security policy and control settings.
Activity Monitoring, Detection, and Response
Diagnostic and Activity log settings are the primary focus of this category, where logs are stored and the configuration settings of those storage mechanisms. Also, as the category name indicates, it includes Detection and Response enablement.
In future postings, this blog will be discussing more mid-year cybersecurity compliance trends based on our findings along with recommendations on how to comply with best practices in 2023. If you would like more information about SecureSky and our proactive managed security services, please do not hesitate to reach out to our experts at https://securesky.com/contact-us/.
SecureSky's core assessment does not include an evaluation of patch management of workloads. However, we see confusion in interpreting the "shared responsibility" model related to patching and inconsistency between cloud and on-premises environments.