Cybersecurity Defense from Reactive to Proactive with MDR Security
Sep 11, 2023
The digital threat landscape is evolving, with cybersecurity breaches becoming almost daily headlines. Attacks have increased by up to 300% since 2019, and breach costs are soaring. The IBM 2023 Cost of a Data Breach Report shows the average cost of a data breach has hit an all-time high of USD 4.45 million. This situation underscores the urgent need to shift from traditional reactive security measures to more robust MDR security (Managed Detection and Response security).
MDR security not only addresses immediate threats but also equips organizations to proactively anticipate and neutralize potential attacks, offering a significant advantage over-reactive security approaches. As we navigate through cybersecurity defense, the transition to MDR security emerges as a crucial strategy for safeguarding organizations against the growing wave of cyber threats.
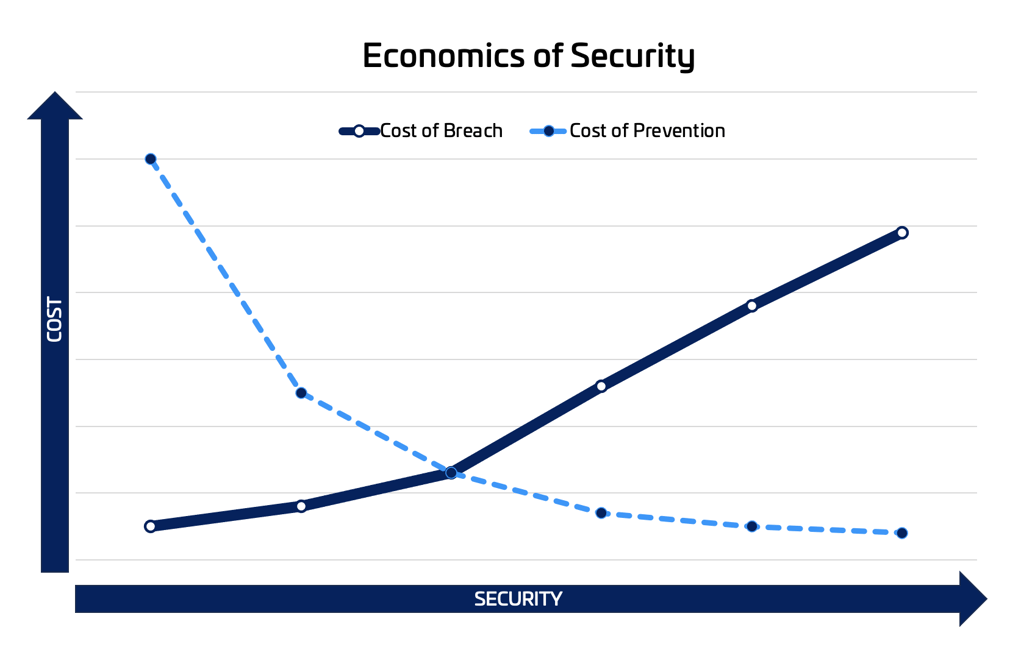
The Economics of Cybersecurity
This is important because of what it tells us about our ability to manage the cost of our security programs. The true cost of an organization’s security is a combination of the cost of their security program, and the cost of any breaches. You spend planned money to try to meet your security goals – protecting your environment and enabling business processes. You expend unplanned money and resources to manage a breach.
Once a breach is identified, the costs of that breach tend to be split fairly evenly across detection and escalation, lost business (current and future), and post-breach response/notifications.
To see the real value of these numbers, it is important to know that the actual cost of a breach is often related to how long an attacker has been in your environment. This is the mean time to identify (MTTI) the breach – often informally called the dwell time. Proactive technologies like MDR (managed detection and response) have reduced dwell times, but according to SecureSky 2023 Mid-Year Azure Compliance Trends, only 38.5% of organizations are using activity monitoring, detection, and response. This problem is compounded by the fact that dwell times have not improved dramatically for organizations that operate more reactively.
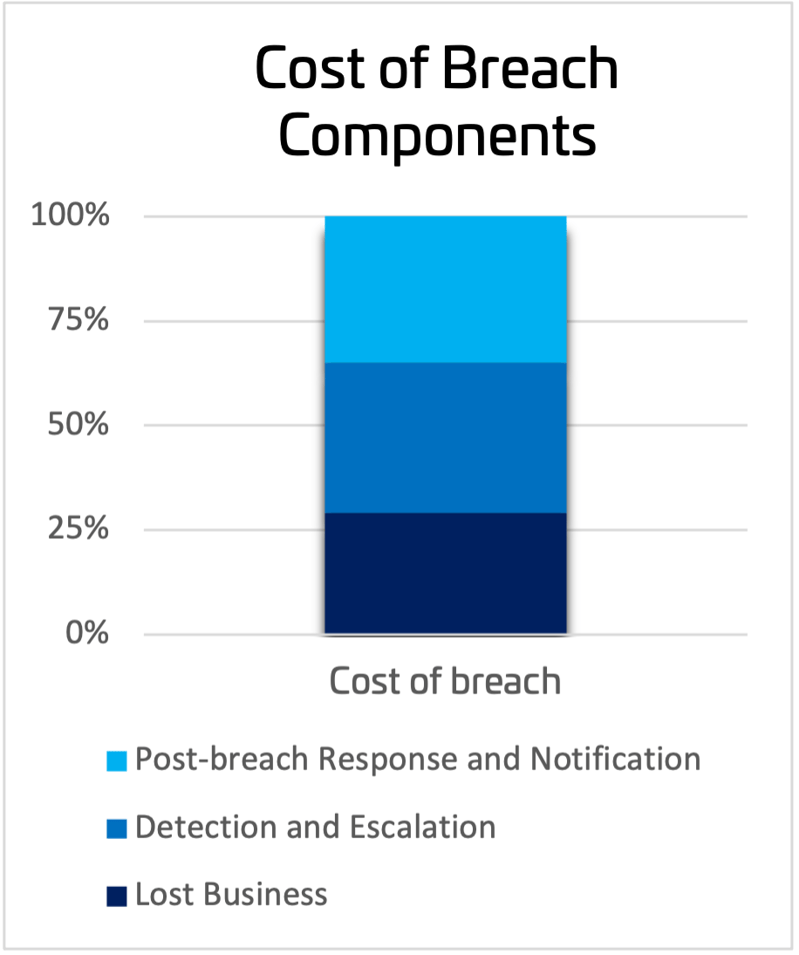
The Cost of Reactive Security
Only about 1 in 3 attacks are identified by an organization’s own security controls since those controls do not fulfill organizational needs for timely, accurate information about attacks and breaches. The other attacks are being identified by an uninvolved third party (like someone else who saw your data online and contacted you), or by the attacker (like an attacker reaching out for a ransomware payment). Not surprisingly, organizations that detect their breaches show dwell times that are as much as 25% shorter, resulting in costs that can be 18% lower than organizations that learn about the breaches from other sources.
If you are not the one detecting attacks and breaches, you tend to have a more reactive or passive security program. Most security programs have matured in a “watch and respond” mode. You may have robust security monitoring in place, including active log gathering and analysis – but this is still reviewing historic data – it is looking at what has already happened, and trying to manage the results of that past event, minimizing the impacts of negative outcomes. According to the SecureSky 2023 Mid-Year Azure Compliance Trends report, only 55% of organizations are using protective controls effectively. Ultimately, a reactive security program can be described by the old idiom “closing the barn door after the horse got out.”
A reactive security program accepts that you will be breached and that you expect long dwell times and the associated increased loss, as well as more complex and more expensive recovery. There are well-known costs of a breach, like lost revenue, fines, and damage to your reputation. Some costs are not as well known, like the impact a breach can have on your ability to meet operational goals if your IT and security teams spend their time chasing breaches. Another one is the stress a breach puts on employees – resulting in extra work, high stress, and increasing turnover of key employees.
A more reactive security program ends up increasing your total cost of security. It also reduces your ability to operate normally and impacts your business goals, since attack and breach response creates unplanned resource costs that could be better dedicated to your business.
Proactive Approach: MDR Security
SecureSky’s basic philosophy supports a proactive security model, providing you with the security-relevant information you need to operate securely and efficiently. Experience shows that evolving to a proactive security model can reduce threats by approximately 60%. Consider that breaches you detect are 18% less expensive than breaches someone else detects for you. Then consider how much more you can save when you are taking additional proactive actions like implementing best-of-breed controls, threat hunting, active vulnerability management, and active posture management. Finally, proactive controls and active management enable you to detect, respond to, and recover from breaches more effectively, providing better security and lower overall cost on two of the three cost components of a breach (detection and escalation; and post-breach response and notifications).
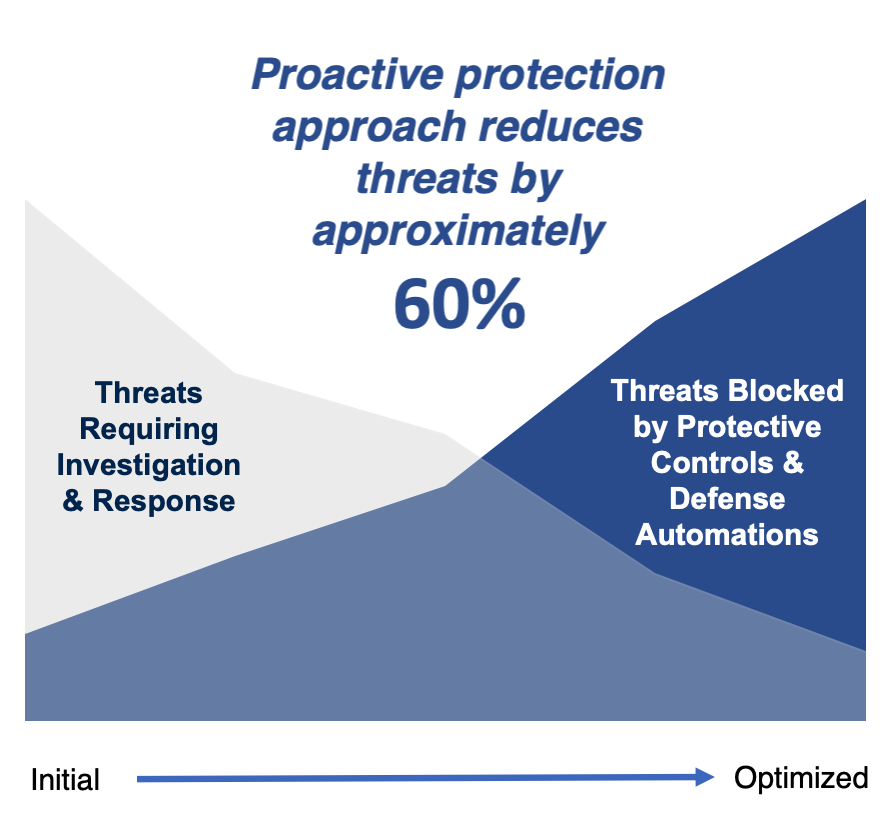
There is, after all, a reason people still use another idiom that helps describe effective, proactive security programs – “An ounce of prevention is worth a pound of cure.”
