Zero Trust Maturity Model (ZTMM 2.0): A Transition to ZTA
May 2, 2023
On April 11, 2023, the Cybersecurity and Infrastructure Security Agency (CISA) under the Department of Homeland Security (DHS) introduced an updated draft of the Zero Trust Maturity Model (ZTMM 2.0). This comprehensive framework serves as a guide for federal agencies embarking on the journey towards a Zero Trust Architecture (ZTA), marking a significant step in the evolution of cybersecurity protocols.
Understanding Zero Trust Architecture
At its core, ZTA embodies a strategic shift in cybersecurity, encapsulating the principle of "never trust, always verify." Unlike traditional security models that grant access based on initial authentication, ZTA insists on continuous verification of all users, devices, and services for every interaction with the organization's IT resources. This approach is crucial in today's digital landscape, where conventional network perimeters have dissolved, giving way to a complex network of cloud services, SaaS applications, and a variety of devices including BYOD and IoT.
The Catalyst of Change: Pandemic and Cloud Adoption
The rapid transition to cloud and edge computing, accelerated by the pandemic, has positioned ZTA as a cornerstone of contemporary security strategies. Organizations now face the challenge of securing a dispersed digital ecosystem, making the principles of Zero Trust more relevant than ever.
ZTMM 2.0: A Roadmap to Zero Trust Maturity
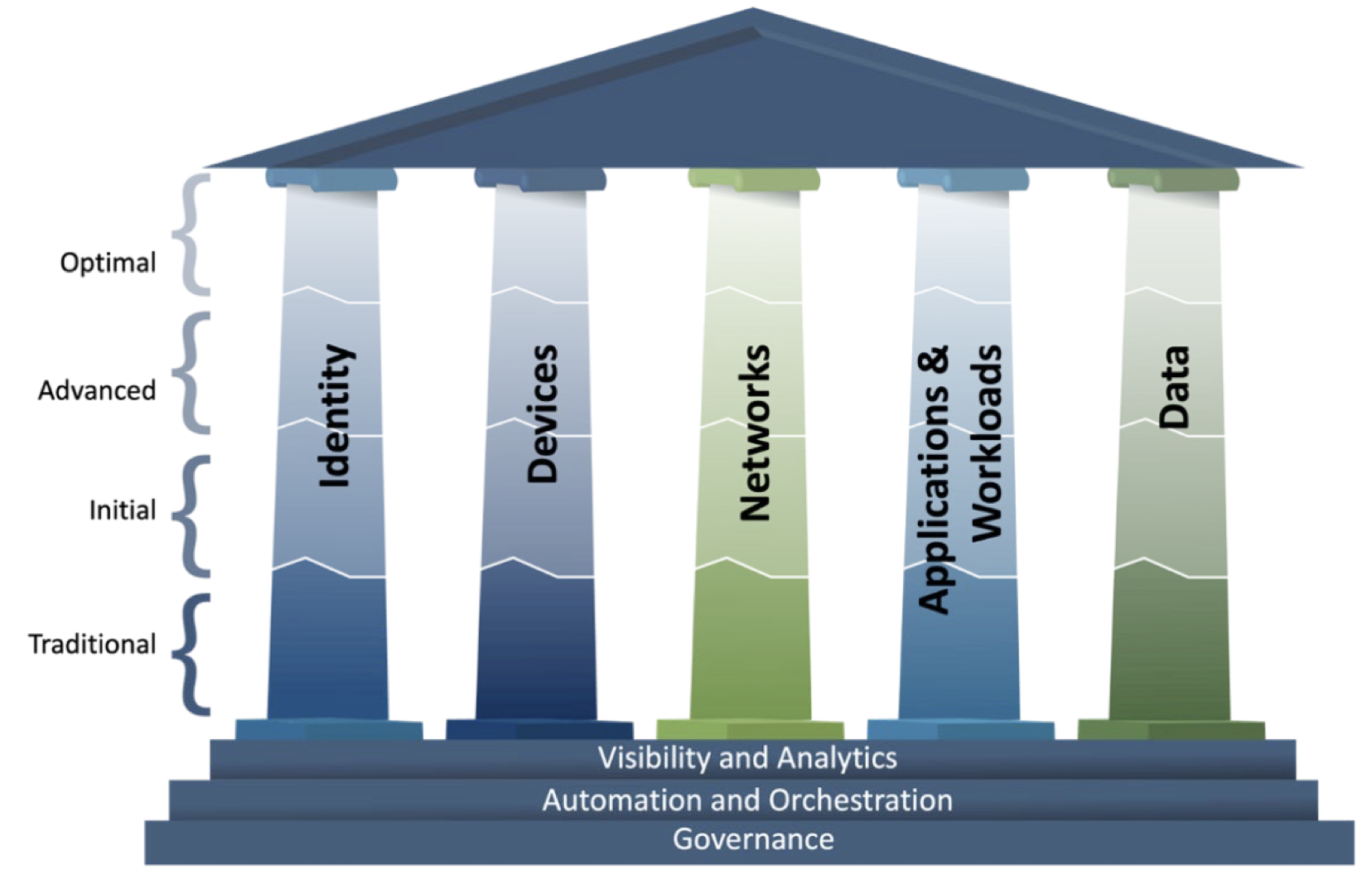
CISA's ZTMM 2.0 outlines a path to achieving maturity in Zero Trust across five key pillars, emphasizing the importance of robust user and device identity verification, as well as the adaptive control of access based on risk assessment. This model encourages organizations to attain a state where confidence in identity integrity and the security of networks, applications, and data is paramount, ensuring that access is precisely calibrated to the minimum necessary privileges.
The release of ZTMM 2.0 by DHS and CISA is a testament to the federal commitment to enhancing cybersecurity through the adoption of Zero Trust principles. As organizations navigate the complexities of modern IT environments, the Zero Trust Maturity Model offers a strategic blueprint for securing assets in an era where traditional defenses no longer suffice. This evolution towards a zero-trust framework is not just a trend but a necessary adaptation to the ever-changing threat landscape.
Enhancing Zero Trust Architecture: Key Elements and CISA's Update Process
In addition to the foundational aspects of ZTA, the Department of Homeland Security's Cybersecurity and Infrastructure Security Agency (CISA) outlines essential "cross-cutting" capabilities that are crucial for the interoperability and enhancement of zero trust principles across various organizational pillars. These capabilities, which have become increasingly feasible through cloud-based technologies, include:
-
Visibility and Analytics: This capability emphasizes the importance of monitoring and analyzing cyber-related data across the enterprise. By focusing on the analysis of observable artifacts and events, organizations can make informed policy decisions, enhance response activities, and build a comprehensive risk profile. This proactive approach aims to bolster security measures and prepare for potential incidents before they occur.
-
Automation and Orchestration: Zero trust leverages automated tools and workflows to streamline security responses across different products and services. This approach ensures that security functions are efficiently managed, maintaining the necessary oversight and interaction throughout the development process.
-
Governance: Effective governance involves defining and enforcing cybersecurity policies, procedures, and processes that align with zero-trust principles. This encompasses managing the enterprise's security posture and mitigating risks by federal requirements and the overarching goals of ZTA.
CISA's ZTMM Version 2.0 Update Process
Following the initial release of the Zero Trust Maturity Model (ZTMM) 1.0 in August 2021, CISA engaged in a comprehensive feedback collection process. This involved soliciting comments from a wide range of stakeholders, including agencies, vendors, consulting services, academic institutions, trade associations, individuals, and international organizations. Through a Request for Comment period, CISA received 378 comments, which were meticulously analyzed to inform the development of the updated ZTMM 2.0. This iterative process reflects CISA's commitment to refining and enhancing the ZTMM to better serve the evolving needs of organizations transitioning to a zero-trust architecture.
REVISED ZTMM MODEL AND PURPOSE
The ZTMM 2.0 draft can be found here.
Per CISA’s “Response to Comments” summary document :
- Commenters requested additional guidance and space to evolve along the maturity model, as well as current and plans to adopt cloud technologies. In response, CISA added the additional maturity stage “Initial” to the maturity model and realigned text for consistency across all pillars. CISA revised the guiding criteria for each stage to account for the new maturity model stage. These maturity stages are meant to be dynamic; planned progress from stage to stage may shift in scope over time.
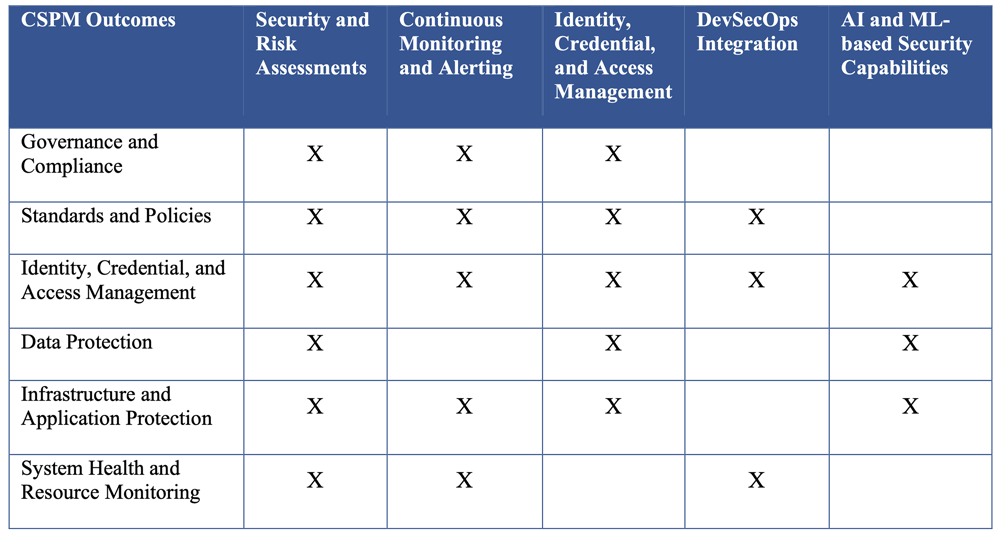
- Relative to current and plans of agencies to adopt cloud technologies, a related CISA publication, Cloud Security Technical Reference Architecture (Cloud Security Technical Reference Architecture v.2 (cisa.gov)), offers guidance related to Cloud Security Posture Management (CSPM) offerings usage to achieve security outcomes, such as:
- Commenters also looked for updates to the longer-term ZTMM In response, CISA updated the text preceding the model to reflect content updates and revised the purpose so the ZTMM is no longer a stopgap solution but continues to support federal agencies in designing and implementing their ZTA transition plans.
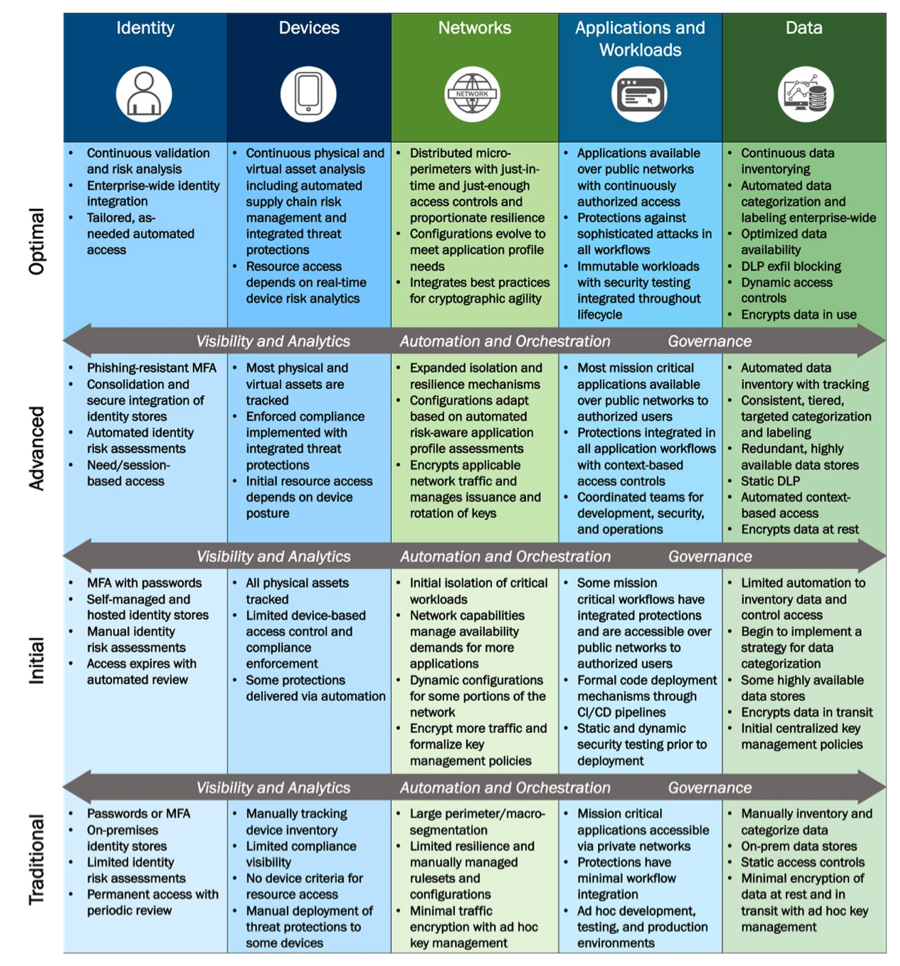
New functions that were added to the “Devices” pillar (see below) include Policy Enforcement & Compliance Monitoring, Asset & Supply Chain Risk Management, and Device Threat Protection.
Refining Zero Trust Architecture: CISA's Comprehensive Update to Guidance and Content
Enhanced Detail and Clarity Across Zero Trust Pillars
In response to feedback for more detailed guidance on implementing Zero Trust Architecture (ZTA), the Cybersecurity and Infrastructure Security Agency (CISA) has meticulously updated the Zero Trust Maturity Model (ZTMM). This revision includes expanded content, additional functions for each pillar, and clearer definitions of cross-cutting capabilities, ensuring a more granular approach to ZTA implementation. Key updates across the ZTA pillars include:
-
Identity Management Enhancements:
- Introduction of secure, passwordless Multi-Factor Authentication (MFA) methods, including PIV (Personal Identity Verification) like FIDO2 and Windows Hello.
- Emphasis on robust two-factor MFA techniques, utilizing authentication apps and number matching for enhanced security.
-
Device Security Strengthening:
- Enhanced Policy Enforcement & Compliance to cover software and configuration management.
- Updated Automation, Orchestration, and Governance functions to include device de-provisioning, offboarding, and remediation for non-compliance.
- Addition of Device Threat Protections for centralized security management.
-
Network Infrastructure Improvements:
- Advanced Network Segmentation to support micro-segmentation based on application profiles.
- Introduction of Network Traffic Management and resilience strategies, integrating elements of Threat Protection into Visibility & Analytics, and expanding Traffic Encryption functions.
-
Applications and Workloads Security:
- Refined Application Access controls to include contextual information, enforce expiration, and adhere to least privilege access.
- Updated Application Threat Protections and Security Testing to embed protections and testing within application development workflows.
- New Secure Application Development and Deployment Workflow to formalize code deployment, restrict production access, and support immutable infrastructure principles.
-
Data Protection Advances:
- Broadened Data Encryption to encompass enterprise-wide encryption, key management policies, and cryptographic agility.
- Enhanced Data Inventory Management and introduced Data Categorization to improve data understanding and classification.
- New Data Availability function to ensure access to historical data, emphasizing the importance of data accessibility.
Cross-Cutting Capabilities Focus: Visibility and Analytics, Automation and Orchestration, and Governance capabilities have been detailed further, offering pillar-independent maturity paths and updated recommendations to support interoperability across ZTA functions.
CISA's updated ZTMM reflects a comprehensive effort to provide organizations with the detailed guidance necessary for a successful transition to a zero-trust security model. By addressing specific stages and functions within the ZTA framework, CISA aims to facilitate a more secure, manageable, and effective implementation process for federal agencies and beyond, aligning with modern cybersecurity requirements and challenges.
ZTA Beyond the Federal Government
The ZTA principles and ZTMM promulgated by CISA for federal agencies equally apply to all organizations.
Certainly, many technologies and services assist companies with applying ZTA concepts. Unfortunately, however, in today’s commercial marketplace the term “zero trust” is overused and often used incorrectly to imply “built-in” security.
If you are new to zero trust, in future blogs SecureSky will explore practical application and measurement of the ZTA principles, including:
- Creating a secure identity management system, including ongoing validation of the effectiveness of controls such as MFA.
- Applying identity and endpoint policies to drive conditional and adaptive access management for more granular control.
- Assessing, continuously monitoring, and enforcing secure configurations of networks, applications, cloud services, and data stores aligned with zero trust principles.
