Threat Investigation: Anatomy of a Business Email Compromise Attack - Part 2
Aug 5, 2019
Business e-mail compromise (BEC) is a class of cybercrime that is growing rapidly. Over the past five years, BEC attacks have resulted in billions of dollars in losses from companies of all sizes across numerous industries making BEC protection a critical strategy for organizations.
In Part 1, we provided an introduction to BEC and discussed why this cyber security threat is increasing. This post, Part 2 of SecureSky’s series, delves into a SecureSky BEC investigation, highlighting how BEC exploits O365 environments.
Investigating the Anatomy of a Business Email Compromise Attack
In the early months of 2019, SecureSky embarked on an investigation into an active BEC attack. Throughout our investigation, we uncovered that this was not an isolated incident; several other organizations had also been compromised. The financial toll on one targeted company exceeded $250,000, with additional losses incurred by others. It's important to note that our insight into the full extent of this campaign was limited, suggesting the actual financial impact could be substantially greater. Beyond monetary losses, the attack caused considerable operational disruptions, demanding extensive efforts to trace the breach and communicate with affected customers and partners to mitigate further risks.
This particular BEC campaign adhered to the typical attack sequence outlined in "The Unassuming Threat – Part 1." We have since reached out to all identified site owners, ensuring that any content altered by the attackers has been removed.
Initial Attack Sequence: Laying the Groundwork for BEC Protection
The onset of this BEC (Business Email Compromise) scenario didn't directly target SecureSky's client, subsequently referred to as "Client Target." The vector was an indirect one, originating from a compromised entity—a customer of Client Target. This breach was exploited to orchestrate a phishing attack on a Client Target employee, underscoring the intricate challenges of BEC protection.
Toward the end of 2018, an episode unfolded where "Employee Victim," a staff member at Client Target, received a seemingly benign email. This communication, purportedly from a familiar customer, included an attachment named “Remittance Advice #100033.xps.” Given the email's origin from a trusted customer, Employee Victim perceived the attachment as a routine notification of a settled bill. However, the reality was starkly different—the attachment was a phishing instrument devised by the BEC perpetrator, cunningly adorned with the customer’s logo to lend an air of authenticity.
Ex.1 Phishing Attachment with Customer Logo
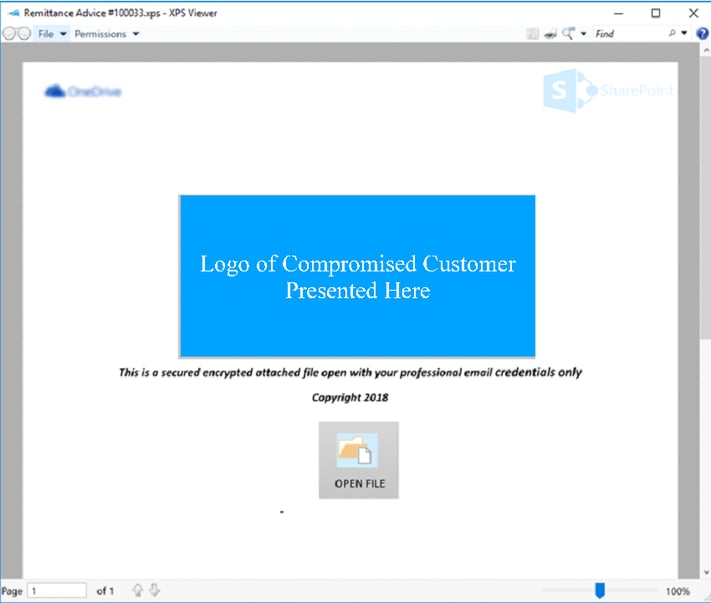
Assuming the e-mail was legitimate when the Employee Victim clicked the ‘OPEN FILE’ icon in the attachment, they were redirected to a SharePoint URL owned by another compromised organization. This page then prompted Employee Victim to open the SharePoint URL (Ex. 2).
Ex.2 SharePoint Page with URL Link
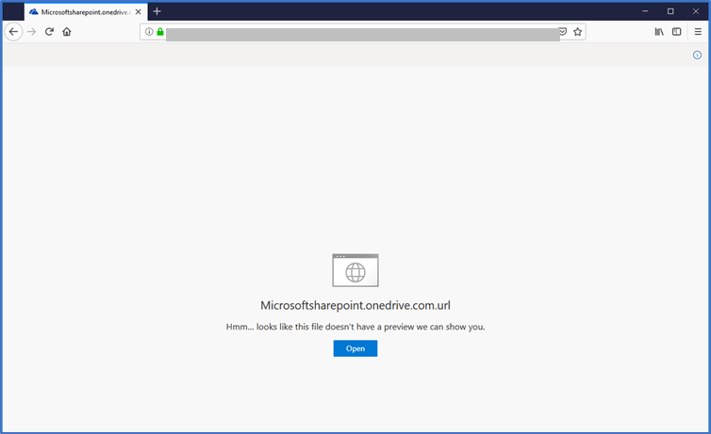
At this point, you might be wondering – why all this redirection and clicking through SharePoint? Why not send the phishing link directly in the e-mail? The attacker is trying to entice users into clicking malicious links in areas where malicious sites are least likely to be detected by security technology. Phishing links in e-mails are more likely to generate a warning or be blocked (via e-mail protection services like Proof Point) than phishing links on SharePoint pages, which do not always have the same levels of protection.
When Employee Victim clicked the ‘Open’ icon on the SharePoint page, they were finally redirected to an attacker-controlled phishing site designed to look like a Microsoft One Drive login page. The perpetrator’s objective with this fake One Drive page was to trick the Employee Victim into providing their credentials by directing them to click on either login button (Ex. 3).
Ex. 3 Attacker Phishing Page Mimicking Microsoft OneDrive Login

Once clicked, the login buttons brought Employee Victim to a credential capture page that mimics a Microsoft account login (Ex 4).
Ex. 4 Phishing Credential Capture Page
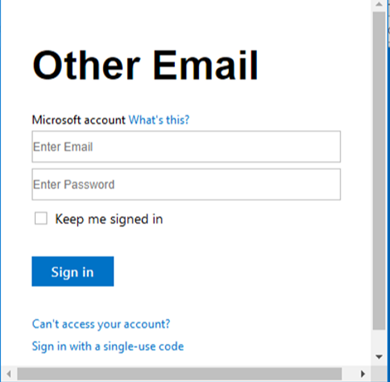
Unfortunately, due to Client Target's existing relationship with the customer, Employee Victim trusted the e-mail and links as legitimate and submitted valid user credentials to the phishing site. Once armed with official credentials, the attacker was able to gain access and authenticate to Client Target's O365 environment and perform actions by impersonating the Employee Victim, including reading and sending e-mails.
Second Attack Sequence: Phishing Via Company Office 365 Tenant
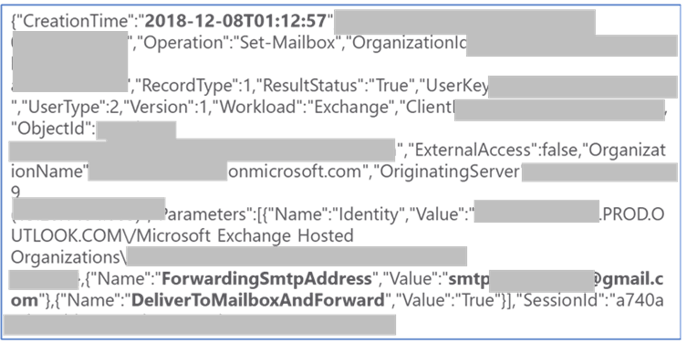
Upon accessing the Employee Victim’s e-mail, the attacker immediately created a rule to forward incoming e-mails from the Employee Victim's inbox to an attacker-controlled Gmail account.
This forwarding enabled the attacker to see and archive inbound e-mails to Employee Victim, including any potential responses to phishing e-mails the attacker planned to send from the compromised account (Ex. 5).
Ex. 5 Log Establishing E-mail Forwarding
Five days after this action, the attacker sent phishing e-mails to 879 customer e-mail addresses from Employee Victim’s account. The phishing e-mails included the same ‘Remittance Advice #100033.xps’ credential phishing attachment that compromised the Employee Victim. However, instead of using the customer company’s logo in the document, Client Target’s logo was now used (Ex. 6).
Ex. 6 Client Target Logo now used in Phishing E-mail from Employee Victim Account

Two days after the phishing attacks began, Client Target was alerted by a customer that Employee Victim was sending phishing e-mails. Client Target then changed Employee Victim’s credentials and hired a third-party security consultant (not SecureSky) to investigate the incident.
The consultant reviewed the access history of Employee Victim’s account and confirmed that the attacker’s external access to the Victim Company O365 environment had been removed. Victim Company assumed that the incident was closed.
Third Attack Sequence: Escalating to Financial Fraud via Compromised Domains
Even after the attacker's access to Client Target's Office 365 (O365) environment was cut off, the underlying threat persisted, evolving into a more financially motivated exploit.
The true potential of Employee Victim's account came to light only after the initial access was revoked. The attacker realized that the real value lay not in the mere access to the O365 environment but in exploiting Employee Victim's critical role in Accounts Payable. The implicit trust that Employee Victim's contacts placed in their billing instructions presented a golden opportunity for financial manipulation.
Initially, the attacker's efforts seemed focused on credential phishing. However, a shift in strategy was observed 30 days post-revocation of access to Employee Victim's account, just when Client Target believed the ordeal was over. The attacker, now blocked from direct access, pivoted to a different tactic—creating look-alike phishing domains. For instance, a subtle misspelling from "clienttarget.com" to "cleinttarget.com" was employed, a classic phishing maneuver aimed at maximizing fraudulent gains from the attack.
The phishing emails sent from these domains meticulously mimicked Employee Victim's email format, including their signature, font size, and even the use of Client Target's logo. But this time, the aim wasn't to harvest credentials but to commit financial fraud directly. The attacker sought to reroute payments destined for Client Target to bank accounts under their control.
Ex. 7 Phishing E-mail from Employee Victim Account
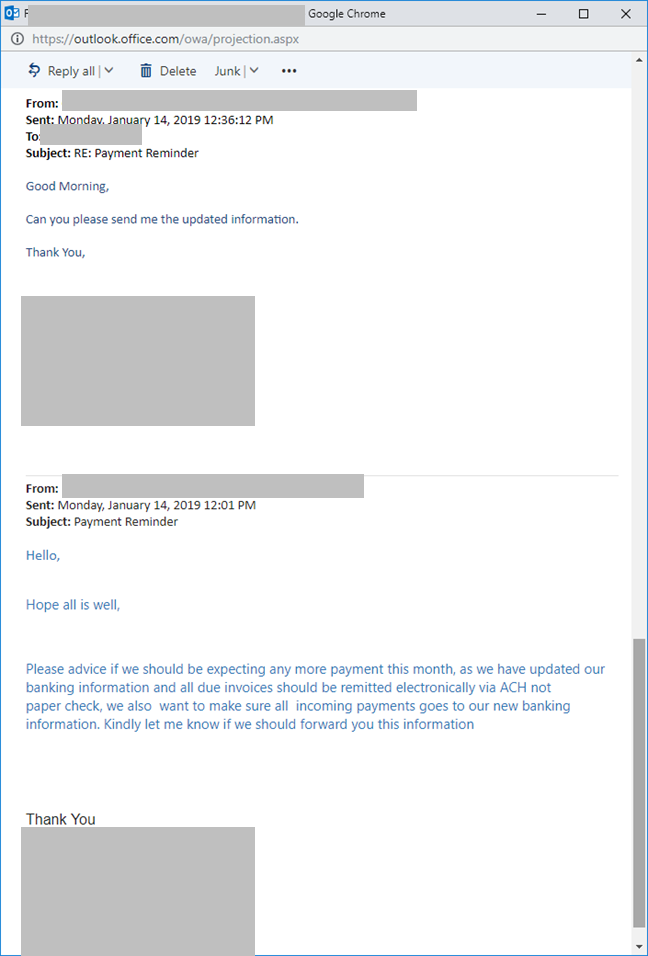
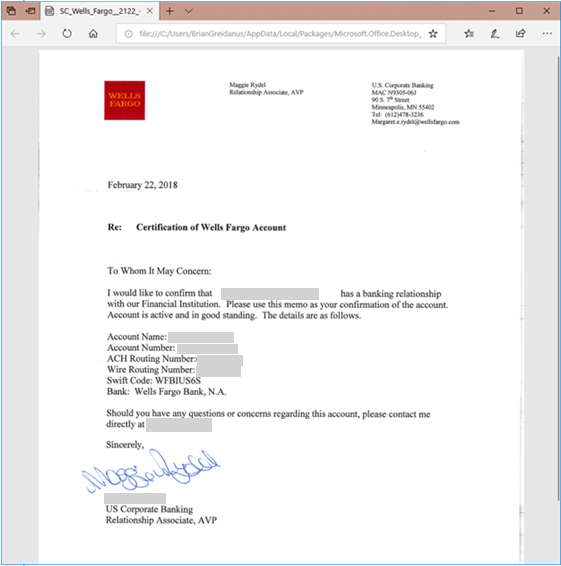
This new set of e-mails notified the recipient that Client Target's bank account information had changed. When the recipient requested details, the perpetrator responded with a falsified Wells Fargo Bank certification letter (Ex. 8). This new payment information pointed to bank accounts controlled by the attacker.
Ex. 8 Falsified Banking Letter Sent to Employee Victim Contacts
Unraveling the Layers of BEC Fraud
The fraudulent bank documents, seemingly legitimate PDF scans, were meticulously altered using editing software. SecureSky's analysis revealed the documents bore multiple layers of counterfeit information, suggesting they were repurposed across various BEC schemes.
The subsequent wave of attacks emanated from a different compromised Office 365 (O365) tenant, where the attacker wielded administrative rights. Utilizing these privileges, the attacker hosted the deceptive domain (cleinttarget.com) and launched phishing emails targeting Client Target's network.
Upon detecting further suspicious activities, Client Target enlisted SecureSky's expertise. Our immediate action involved coordinating with the domain registrar to dismantle the phishing domain. Further investigation, guided by DKIM authentication headers from the phishing emails, led us to the compromised O365 tenant. Despite revoking the attacker's access, the battle against fraudulent domains persisted, with new ones being neutralized shortly thereafter.
In the process of aiding the compromised tenant in securing their O365 environment, it became evident that the attacker had long exploited this platform, hosting phishing domains targeting numerous global entities. SecureSky undertook the responsibility of alerting all affected companies, showcasing the interconnected challenge of BEC protection and the necessity for collective vigilance and response strategies.
Final Attack Sequence: Escalating Financial Phishing Tactics
The resilience of the attacker in this case was unmistakable. Even after the initial breach into Client Target's Office 365 (O365) environment was neutralized and several phishing domains were dismantled, the attacker adapted their strategy once more.
Several Client Target's contacts, having engaged with earlier phishing attempts, became the focus of the attacker's renewed efforts to siphon funds. Leveraging compromised GoDaddy email accounts, the attacker resumed their phishing campaign, targeting these contacts with renewed vigor.
More than two months following the breach of the Employee Victim's account, a fresh wave of phishing emails was dispatched. These emails were cunningly disguised:
- The "From" address mirrored Employee Victim’s official email, lending credibility to the messages.
- Replies were redirected to an "accountant.com" address, a domain previously linked to malicious activities, further complicating the detection of fraud.
- The source of these emails was traced back to a legitimate GoDaddy webmail account belonging to another compromised entity. SecureSky promptly alerted the affected company, leading to the account's deactivation.
- These emails deceitfully requested the issuance of physical checks to a new payee and address, diverging from Client Target's standard procedures.
- The specified mailing address led to a location known for criminal activities, suggesting the attacker planned to personally collect the fraudulent payments. This prompted immediate notification to both the property management and law enforcement agencies.
Despite shutting down this channel, the attacker persisted, attempting to reach Client Target's customers through yet more compromised email accounts. SecureSky intervened, contacting the account owners and their service providers to revoke the attacker's access. Approximately two and a half months after the initial compromise, the relentless BEC campaign began to wane.
Threat Investigation: Concluding Insights on BEC Protection
This incident of Business Email Compromise (BEC) serves as a stark reminder of the potential rapidity and severity of damage these attacks can inflict. Effective BEC protection hinges on a triad of critical strategies:
-
Office 365 Configuration: Enhancing O365 with robust security settings is crucial for safeguarding environments from BEC threats. Implementing the recommended configurations can significantly bolster the defense of any organization against such attacks. (Refer to Part 3 for detailed guidance.)
-
Office 365 Threat Detection: Activating comprehensive auditing and logging features within O365 is essential for early detection of BEC attempts. These tools enable organizations to swiftly identify and respond to potential compromises. (Insights on this can be found in Part 4.)
-
Security Awareness: Empowering employees with the knowledge to recognize BEC targeting is fundamental. Understanding the indicators of a compromise allows for quicker identification and mitigation of threats. (Part 5 will delve deeper into this aspect.)
Armed with the appropriate tools, configurations, and awareness training, the vulnerability to BEC attacks can be markedly reduced. We invite you to continue exploring our series for in-depth discussions on O365 configurations for BEC protection, the role of logging and auditing in identifying BEC compromises and enhancing employee vigilance against these sophisticated attacks. The upcoming final post will explore potential BEC attacker organizational structures (Part 6).
