The Unassuming Threat: Business Email Compromise and the Role of Managed Detection & Response - Part 1
Aug 4, 2019
Globally, businesses of every scale are confronting the escalating threat of Business Email Compromise (BEC), a cybercrime that has bilked organizations out of billions over the past decade. The question then arises: how can your organization fortify itself against BEC?
This is where we step in. Welcome to the first entry in our six-part SecureSky series, dedicated to unraveling BEC and showcasing the pivotal role of managed detection & response in combating this cyber threat. This post lays the groundwork by introducing BEC and its growing prevalence. For those already acquainted with BEC, Part 2 delves into recent investigations and the specific vulnerabilities of Office 365 (O365) environments to these attacks.
Unveiling the Threat: Understanding Business Email Compromise
BEC employs deceit—primarily through social engineering and impersonation—to defraud businesses financially. Attackers meticulously craft a series of attacks exploiting software services like O365, making managed detection & response an essential defense mechanism.
To achieve their objectives, perpetrators use a sequence of elaborate attacks and approaches that exploit users of software services like O365 (see diagram below).
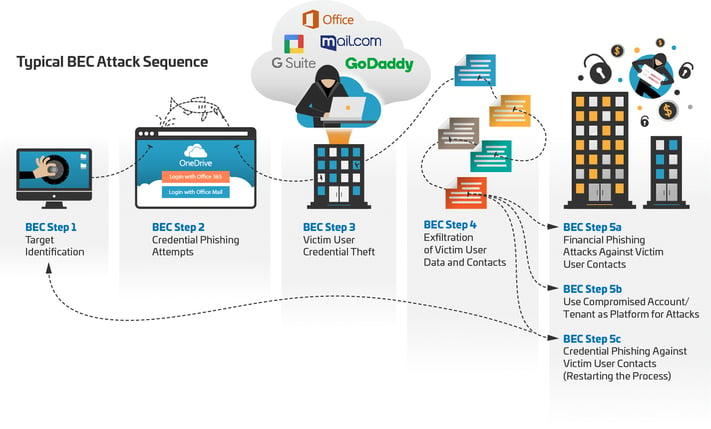
Breaking Down the BEC Attack Process and Managed Detection & Response Strategies
BEC attacks unfold in a meticulously planned sequence, starting with the identification of potential phishing targets. The attackers then launch phishing campaigns aimed at these selected individuals, to steal their credentials. Successful credential theft marks a pivotal moment in the attack, allowing the perpetrator to access and extract sensitive data and contacts from the victim's account.
Upon gaining unauthorized access, attackers typically adopt one of three strategies, each exploiting the compromised account to further their malicious objectives:
-
Financial Phishing of Contacts: If the compromised account plays a role in financial operations, attackers often engage in financial phishing. They target the user’s contacts, attempting to deceive them into making unauthorized financial transactions. This underscores the importance of managed detection & response services in monitoring unusual financial request activities linked to user accounts.
-
Exploiting Administrative Privileges: Attackers prize user accounts with administrative access within the Office 365 environment. Such accounts can be leveraged as launchpads for broader attacks, making it crucial for organizations to employ managed detection & response solutions that can identify and mitigate unauthorized use of administrative privileges.
-
Continuation of Credential Phishing: With access to a user's contacts, attackers may persist in credential phishing efforts, aiming to compromise additional accounts within the organization. This tactic highlights the need for comprehensive managed detection & response mechanisms capable of detecting and responding to successive phishing attempts within the network.
Threat Severity: What is the Impact of BEC?
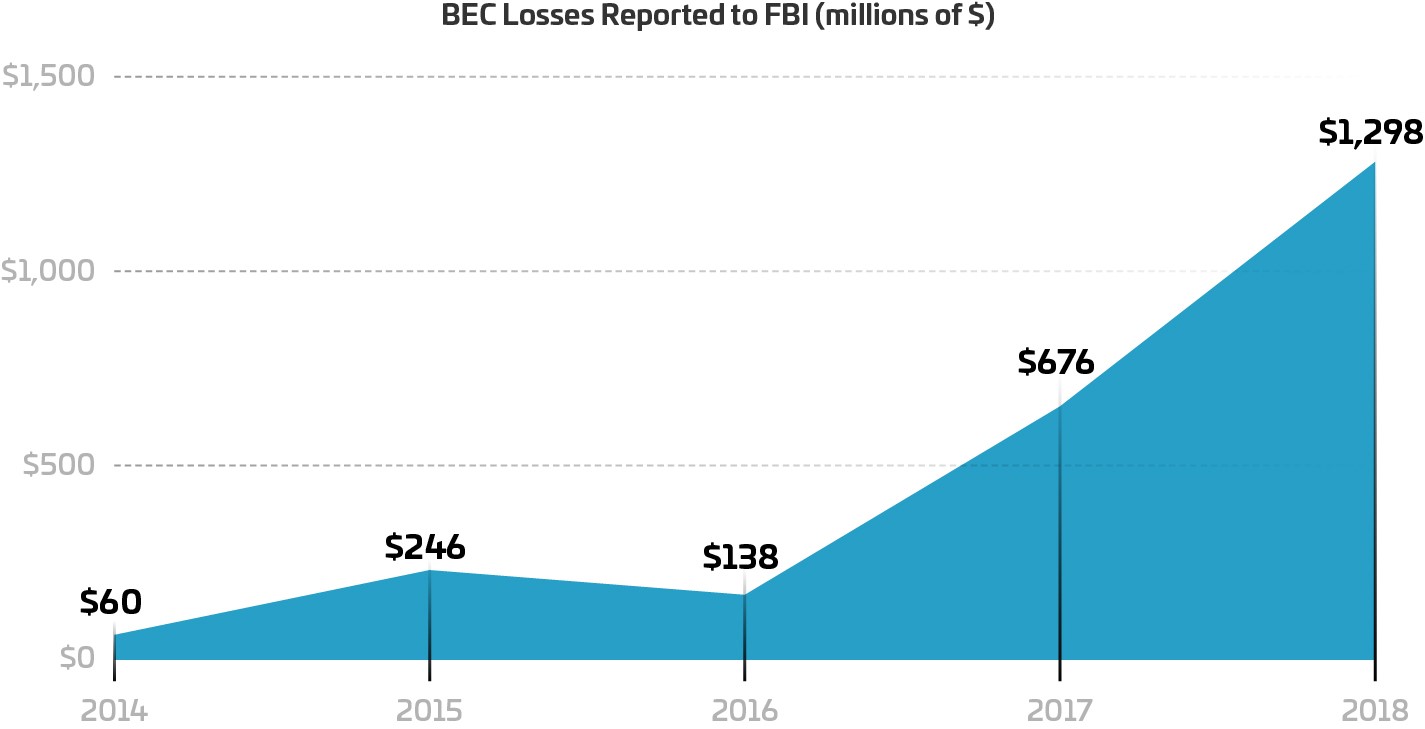
We've seen BEC become a very systemic problem for organizations of any size. Attacks are growing rapidly in the U.S. especially. According to the FBI, BEC crimes cost U.S. businesses over $1.3 billion in 2018 alone and have been steadily increasing since 2016 (see below for losses figure).
From 2015 to 2107, Google and Facebook lost a combined amount of $123 million to a BEC cyber-attack that was organized by an individual in Lithuania. While the tech giants were able to recover the stolen funds, a majority of smaller businesses hit by these attacks are not so fortunate.
Threat Frequency: Why is BEC on the Rise?
The short answer as to why BEC attacks are increasing at an exponential rate is simply because it works, especially against Office 365 environments. Criminals have adopted this method of cyber-attack for several reasons, including:
They are inexpensive and easy to initiate – BEC attacks do not require the use of malware or 0-day exploits; BEC attacks typically start with phishing e-mails and can be executed at scale with minimal cost and expertise.
O365 Infrastructure Enables Sustainment – If an attacker can access an O365 account with administrative privileges in the O365 tenant, the compromised tenant environment can be used as a phishing platform to launch attacks against other organizations.
Potential High Financial Returns – If an attacker can compromise a user that has high trust relationships with other companies (e.g., an executive or employee who works in Accounts Payable or Billing departments), those relationships can be leveraged to commit financial fraud.
Minimal Risk – Because logging and auditing in O365 environments have historically been poor, and losses from BEC are typically distributed across several organizations so that significant financial losses do not occur for individual organizations, the chances of BEC actors being caught is low.
Fortifying Against BEC Attacks: A Managed Detection & Response Strategy
Preparing your organization to withstand BEC attacks requires a proactive and comprehensive approach. At SecureSky, we equip our clients with the knowledge and tools necessary for an effective defense against these cyber threats. A robust strategy for BEC preparedness encompasses three critical pillars:
-
O365 Configuration and Hardening: Strengthening your O365 environment through proper setup and security hardening is foundational. This step ensures that your digital infrastructure is less susceptible to BEC intrusions.
-
Implementing BEC Detection Capabilities: Utilizing managed detection & response services within O365 is key to identifying and mitigating BEC threats promptly. Continuous monitoring and analysis of threat events enable organizations to respond swiftly to any indicators of compromise.
-
Employee Education and Support: Empowering your team with the knowledge to recognize BEC attempts is crucial. Providing training and technological support helps employees identify misuse of their O365 accounts and understand their role in the organization's broader BEC protection strategy.
Equipped with the right managed detection & response tools and comprehensive training, the vulnerability of your organization to BEC attacks can be significantly diminished.
We invite you to engage with the rest of our series, where we'll delve deeper into optimizing O365 configurations for BEC defense (Part 3), enhancing logging and auditing functions indicative of BEC activities (Part 4), and guiding employees on recognizing BEC targeting (Part 5). The concluding installment will explore potential organizational structures behind BEC operations (Part 6).
Subscribe to our blog to stay updated on crucial cloud security developments and learn how managed detection & response can safeguard your organization against BEC and other cyber threats.
Business Email Compromise Series
