Configuration of Office 365 to Detect BEC Attacks - Part 4
Sep 25, 2019
Welcome back to our series on safeguarding against Business Email Compromise (BEC) within Office 365. Previously, we've explored the rise of BEC attacks, their operational tactics, and essential configuration settings for protection. In this fourth installment, we delve into Office 365's logging and auditing capabilities, crucial for detecting BEC threats. Upcoming posts will guide employees on recognizing BEC targeting (Part 5) and speculate on the structure of BEC attackers (Part 6).
Office 365 Security Configuration Resources
This series zeroes in on BEC, offering targeted recommendations. For comprehensive Office 365 security guidance, refer to the CIS Benchmark for Microsoft 365 or Microsoft’s Secure Score. SecureSky provides Office 365 assessments and MDR services to bolster your security posture against threats.
Essential Office 365 Security Settings for BEC Detection
1. Mailbox Auditing: Activate mailbox auditing to log mailbox access and actions, providing visibility into unauthorized activities. Enable Mailbox Auditing.
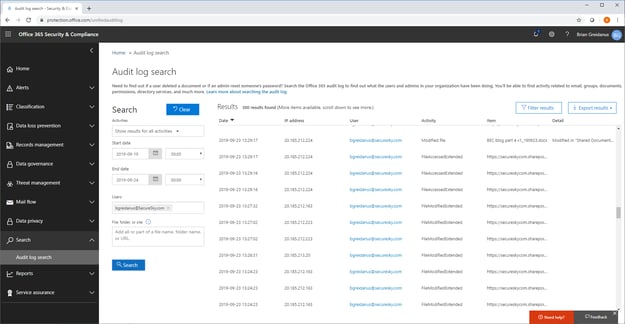
2. Office 365 Audit Log Search: Utilize Audit Log Search for a 90-day historical analysis by privileged personnel, aiding in security investigations. Audit Log Search menu is presented in the following screenshot:
Audit Log Search Output
3. Email Flow Phishing Protection: Customize mail flow rules to shield users from phishing, including notifications for external emails, blocking unscannable attachments, and flagging emails with suspicious content or URL shorteners.
The following five email rules should be considered for implementation in Office 365 environments:
- Implement a mail flow rule that provides a notification to users when messages are received from outside the company. These notifications can aid user awareness for messages that are internal vs. external.
- Implement a rule that blocks email attachments that cannot be inspected. If alerted, a warning message should be sent to the end user.
- Create a mail flow that blocks emails containing executable content. If alerted, a warning message should be sent to the end user.
- Where feasible, implement a rule that notifies the email recipient of the use of keywords associated with phishing and Business E-mail Compromise attacks. For instance, user warnings can be prepended to emails with attachments with filenames that include keywords “remittance”, “invoice”, “bill”, “payroll”, to ensure that the recipient is aware that these messages could potentially be phishing attacks.
- Implement a rule that notifies the email recipient of the use of URL shorteners, which are used frequently in phishing attacks. For instance, user warnings can be prepended to emails that include URL shorteners, including “bit.ly”, “goo.gl”, and “tinyurl.com”, , to ensure that the recipient is aware that these messages could potentially be phishing attacks.
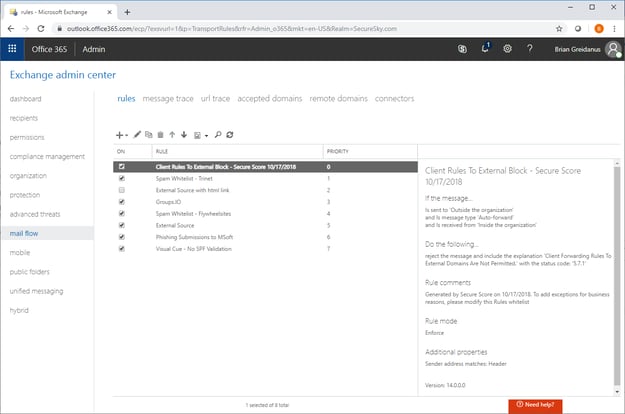
The Mail flow rule creation menu is presented in the following screenshot:
Mail flow Rule Creation Menu
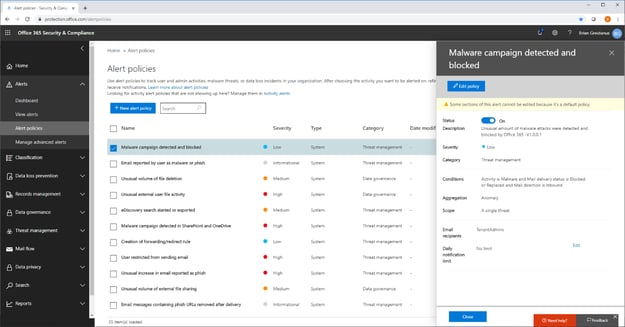
4. Alert Policies: Activate all default alert policies appropriate to your licensing level to monitor for unusual activities indicative of security breaches.
All default alert policies for the purchased licensing level (more default alerts exist at higher tiers) should be enabled in Office 365 environments, as presented in the following screenshot:
Alert Policies
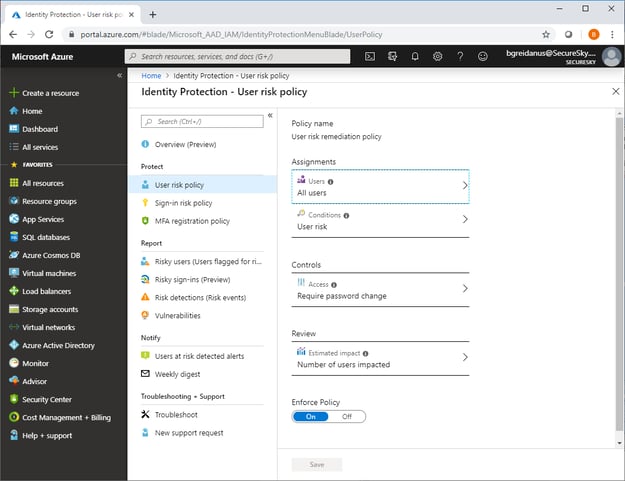
5. Risky Sign-In and User Detection: Implement Azure AD Identity Protection policies to evaluate sign-in risks and enforce security measures like MFA for suspicious login attempts.
A policy should be created for risky sign-ins in Azure Active Directory Identity Protection, as presented in the following screenshot:
Azure Active Directory Identity Protection User Risk Policy

When configured, user and sign in risk policies generate alerts based on the following sign in characteristics:
- Users with leaked credentials Offline
- Sign-ins from anonymous IP addresses
- Impossible travel to atypical locations
- Sign-ins from unfamiliar locations
- Sign-ins from infected devices
- Sign-ins from IP addresses with suspicious activity
An example alert is presented in the following screenshot:
Effective BEC detection in Office 365 necessitates regular log reviews and vigilant monitoring of configuration settings. Whether managed internally or by an MDR provider, maintaining these practices is vital for identifying and responding to potential BEC incidents promptly.
