Detecting Business Email Comprise (BEC) Attacks - Part 5
Nov 22, 2019
So far in our journey, we've laid the groundwork by introducing the concept of BEC attacks and exploring their rising prevalence. In Part 2, we delved into the mechanics of BEC attacks within O365 environments, leveraging insights from recent investigations. Part 3 was dedicated to unveiling critical Office 365 configuration settings that bolster defenses against BEC threats. Moving on to Part 4, we highlighted the pivotal role of logging and auditing features in O365 that empower organizations to uncover BEC attempts.
Now, in Part 5, we shift our focus towards empowering employees with the knowledge to spot BEC attacks in their tracks. We'll cover not only detection strategies but also how to recognize signs that an attack has been successful, potentially compromising an account.
As we continue, Part 5 will serve as a guide for employees to identify when they're the target of a BEC scheme. Stay tuned for Part 6, where we'll venture into the organizational dynamics behind BEC attackers, completing our comprehensive exploration of Business Email Compromise.
Enhancing Office 365 Security to Combat BEC
Our series zeroes in on the critical issue of Business Email Compromise (BEC). While our tips are tailored to thwart BEC attacks, it's important to remember they form part of a broader strategy needed to secure an Office 365 environment fully.
For those seeking comprehensive security measures for Office 365, consider consulting the CIS Benchmark for Microsoft 365 or Microsoft’s Secure Score for a more extensive security framework. Additionally, for organizations looking to deepen their defense mechanisms, SecureSky offers specialized Office 365 assessment and Managed Detection and Response (MDR) services. These services are designed to fortify your Office 365 setup, ensuring vigilant monitoring and swift response to any threats that arise.
Recognizing BEC Attacks
Business Email Compromise (BEC) attacks cleverly disguise themselves, often originating from legitimate accounts without requiring attachments or malware, making them particularly challenging to spot. However, certain signs can help you identify these deceptive communications:
Apply General Phishing Detection Techniques
The skills you use to dodge phishing attempts are also effective against BEC schemes. Keep an eye out for:
- Email Authenticity: Ensure the recipient or reply-to addresses are legitimate, avoiding phishing domains (e.g., ensuring the email is intended for "intendeddomain.com" rather than "intendedd0main.com").
- Link Safety: Only click on links if you're sure of their trustworthiness, and be cautious of URL shorteners which can obscure the actual destination.
Office 365 users have an advantage with two specific configuration settings:
- Email Flow Phishing Protection: As detailed in Part 4, configuring Office 365 to enhance the detection of phishing can be a significant deterrent against BEC.
- Exchange MailTips: This feature alerts users when they're emailing external addresses, adding an extra layer of scrutiny.
Discrepancies in Email Addresses
Be wary if an email's reply-to address differs from the From address. For example, an email from "brian@securesky.com" that requires replies to be sent to "brian@finance.com" should raise red flags.
Unusual Requests for Payment
Be alert to unexpected requests for changes in payment details. This includes modifications to bank account information, payment addresses, or company names. Such requests are common indicators of BEC fraud.
Suspicious Login Requests
BEC attacks may attempt to steal credentials by directing users to third-party sites under the guise of accessing work-related documents, like invoices. Always verify the authenticity of any site that an email link redirects you to, especially if it asks for login information.
Recognizing Signs of a Successful BEC Attack
Given the stealthy nature of Business Email Compromise (BEC) attacks, it's crucial to know the signs that indicate a successful breach. Being aware of these indicators can help you respond swiftly:
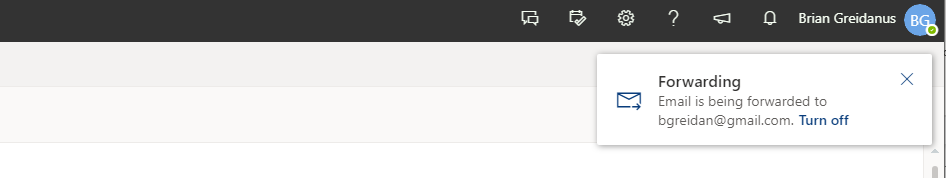
1. Altered Email Forwarding Rules
One of the clearest signs of a compromised account due to a BEC attack is unauthorized modifications to your email forwarding settings. If you notice unexpected notifications or changes in your account related to email forwarding, it's imperative to investigate these anomalies immediately.
2. Unusual Activity in Sent or Deleted Items
Regularly review your Sent Mail and Deleted Items folders. If you discover emails that you don't recognize, especially those sent to unfamiliar addresses, this could indicate a BEC actor has used your account to communicate or divert messages.
3. Bounce-Backs from Unknown Sent Emails
Receiving bounce-back messages for emails you don't recall sending is a red flag. This often means a BEC attacker has attempted to send bulk messages from your account, leading to undeliverable responses.
4. Modifications to Email Signature or Contact Details
Any unauthorized changes to your email signature, such as adjustments to your address or phone number, suggest an attacker has gained access. These alterations are made to misdirect communications to the attacker, furthering their fraudulent activities.
Fortifying Against BEC with Knowledge and Vigilance
Empowering employees with the ability to recognize and respond to BEC attacks is not just a strategy but a necessity in today's digital age. The insights shared in this series aim to transform users from potential victims into proactive defenders of their digital domains. By understanding the subtleties of BEC tactics, recognizing the signs of compromise, and knowing how to act swiftly, employees can significantly reduce the risk and impact of these attacks.
SecureSky's commitment to enhancing Office 365 security through comprehensive measures and Managed Detection and Response (MDR) services underscores the importance of a layered defense strategy. Together, we can create a more secure digital environment, one where BEC attacks are identified and mitigated before they can inflict damage. Stay vigilant, stay informed, and let's continue to strengthen our defenses against the ever-evolving threat landscape.
