Optimizing Office 365 Settings to Shield Against BEC Attack - Part 3
Sep 4, 2019
In the initial segment of this series, we unveiled the mechanics behind Business Email Compromise (BEC) attacks and explored the reasons behind their surge. The subsequent part delved into the operational dynamics of BEC attacks within O365 ecosystems. Now, in this third installment, we're set to outline pivotal Office 365 configuration adjustments that can fortify defenses against BEC attacks.
The upcoming articles will shed light on the logging and auditing features within Microsoft Office 365 that signal potential BEC compromises (Part 4), guide employees on recognizing BEC attack attempts (Part 5), and hypothesize on the organizational framework of BEC operations (Part 6).
1.0 Essential Office 365 Security Configurations Against BEC Attacks
While our focus remains squarely on Business Email Compromise, the security recommendations throughout this series are specifically tailored to thwart BEC attacks. However, it's crucial to acknowledge that these suggestions do not encompass the full spectrum of strategies required to secure an Office 365 setup comprehensively. For a broader security overview, organizations are encouraged to consult the CIS Benchmark for Microsoft 365 or Microsoft’s Secure Score for extensive protective measures.
For entities seeking an external evaluation of their Office 365 security posture, SecureSky offers specialized Office 365 assessment and Managed Detection and Response (MDR) services. These services are designed to enhance security measures, ensure continuous monitoring, and facilitate swift responses to threats within the Office 365 environment, providing an additional layer of defense against BEC attacks.
2.0 Top Office 365 Security Configuration Settings to Defend Against BEC Attacks
A critical initial step in safeguarding against Business Email Compromise (BEC) attacks is preventing account compromises. The most effective strategy for this is the implementation of Multi-Factor Authentication (MFA) across your entire user base.
MFA enhances security by requiring users to provide multiple forms of verification before gaining access. Typically, in Office 365 environments, this involves (1) entering a password and (2) verifying access through a mobile device. This dual-layer authentication significantly reduces the risk of unauthorized access.
For scenarios where enabling MFA for every user might not be feasible, prioritizing its activation for Azure Active Directory privileged roles is essential. Compromising a privileged account could lead to a full-scale attack on the Office 365 ecosystem, underscoring the importance of protecting these critical access points with MFA.
The following PowerShell can be used to confirm if MFA is implemented in your environment:
PowerShell script to confirm MFA status
| Get-MsolRole | Where-Object {$_.Name -like "*Admin*"} | ForEach-Object { Get-MsolRoleMember -RoleObjectId $_.ObjectId } | Select-Object EmailAddress, @{N="MFA Status"; e={$_.StrongAuthenticationRequirements.state}} -Unique |convertto-json |
It is common for BEC attackers to set up mail forwarding rules to auto-forward messages to an external mailbox, as presented in the following screenshot:
Forwarding enabled on user account in Office 365 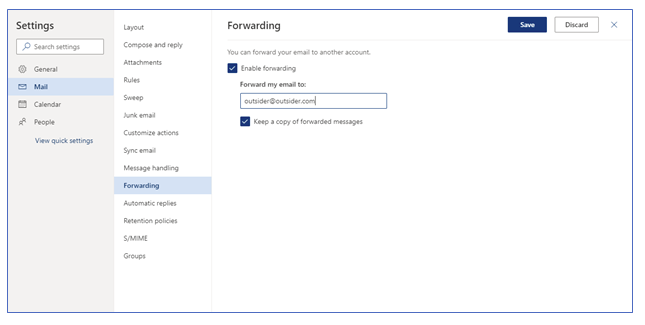
This forwarding intends to ensure that the attacker can see and archive inbound emails to compromised accounts including any potential responses to phishing emails the attacker sends.
Because of this risk, users should not be permitted to create auto-forwarding rules to inboxes that are not located within the organization.
To confirm that no current rules exist that forward emails to external domains, log in to Microsoft 365 Admin Center, select Exchange, and Mail Flow. From the Mail Flow menu, confirm that no unauthorized rules exist that permit forwarding to external domains.
PowerShell script to confirm finding status:
| get-transportrule |where-object {$_.senttoscope -eq "notinorganization"} |select-object senttoscope, fromscope, messagetypematches, actions |convertto-json |
Exchange MailTips are messages that are displayed to users as they are composing messages in Outlook. MailTips are intended to provide warnings to users when potentially inappropriate or insecure emails are being sent.
The different Exchange MailTips policies, descriptions, and best practice settings are presented in the following table:
Exchange MailTips Configuration Settings
|
Configuration Attribute |
Description |
Best Practice Setting |
|
MailTipsAllTipsEnabled |
Confirms that MailTips is enabled. |
True |
|
MailTipsExternalRecipientsTipsEnabled |
Displays a warning when an email recipient is outside of the sender’s organization. |
True |
|
MailTipsGroupMetricsEnabled |
Enables MailTips to use Exchange GroupMetrics data, which maintains member counts of all distribution groups in the organization. |
True |
|
MailTipsLargeAudienceThreshold |
Establishes the number of recipients considered a “Large Audience” by MailTips |
25 or other appropriate value |
|
MailTipsMailboxSourcedTipsEnabled |
Enables MailTips to notify the sender if the recipient has a full mailbox or has Out of Office notifications enabled. |
True |
The MailTips setting most relevant to security is “MailTipsExternalRecipientsTipsEnabled.” This setting can alert a user responding to a phishing email that the email is being sent to an external domain. This setting can also assist in situations where an email address may have been mistyped.
The following PowerShell can be used to confirm Exchange MailTips Settings in your environment.
PowerShell script to confirm Exchange MailTips setting status:
| get-organizationconfig |select-object *tip* |convertto-json |
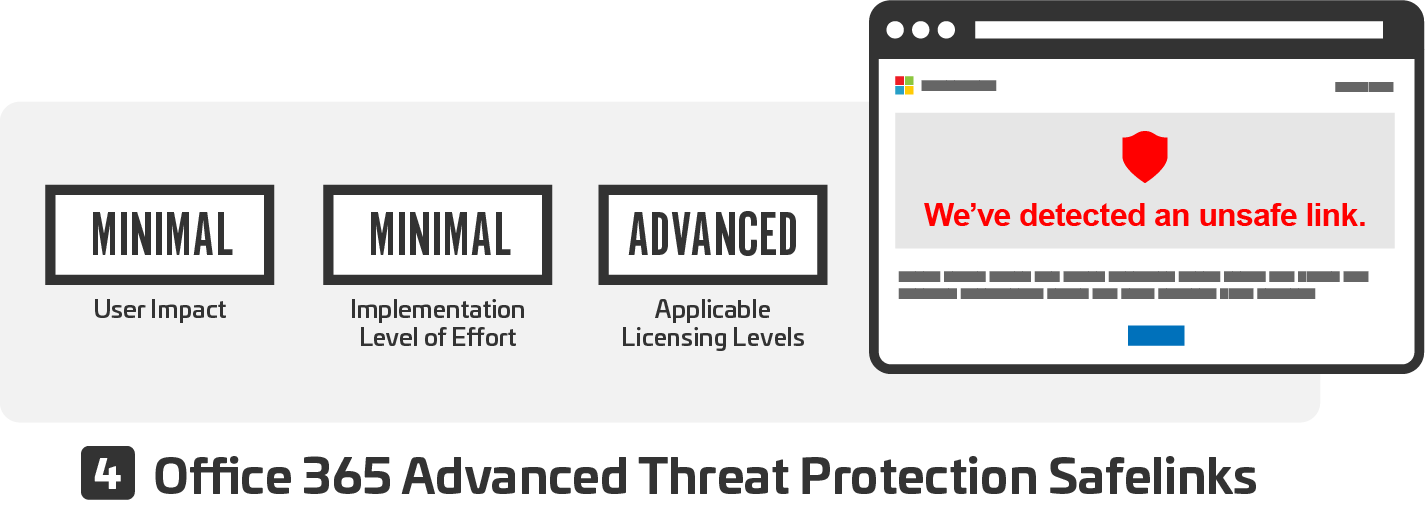
Office 365 Advanced Threat Protection (ATP) Safe Links for Office Applications expands phishing protection to Office 365 applications and provides time-of-click verification of URLs within Office applications for safe access.
Use of this functionality requires separate ATP licensing, or to purchase a licensing level that includes ATP. This is the only setting in this guidance that requires additional licensing.
|
Configuration Attribute |
Description |
Best Practice Setting |
|
EnableSafeLinksForClients |
Specifies whether Safe Links is enabled for clients |
True |
|
AllowClickThrough |
Specifies whether to allow users to click through to the original blocked URL |
False |
|
TrackClicks |
Specifies whether to track user clicks related to blocked URLs |
False |
|
EnableATPForSPOTeamsODB |
Specifies whether ATP will provide time-of-click verification of URLs within SharePoint, OneDrive, and Microsoft Teams for safe access. |
True |
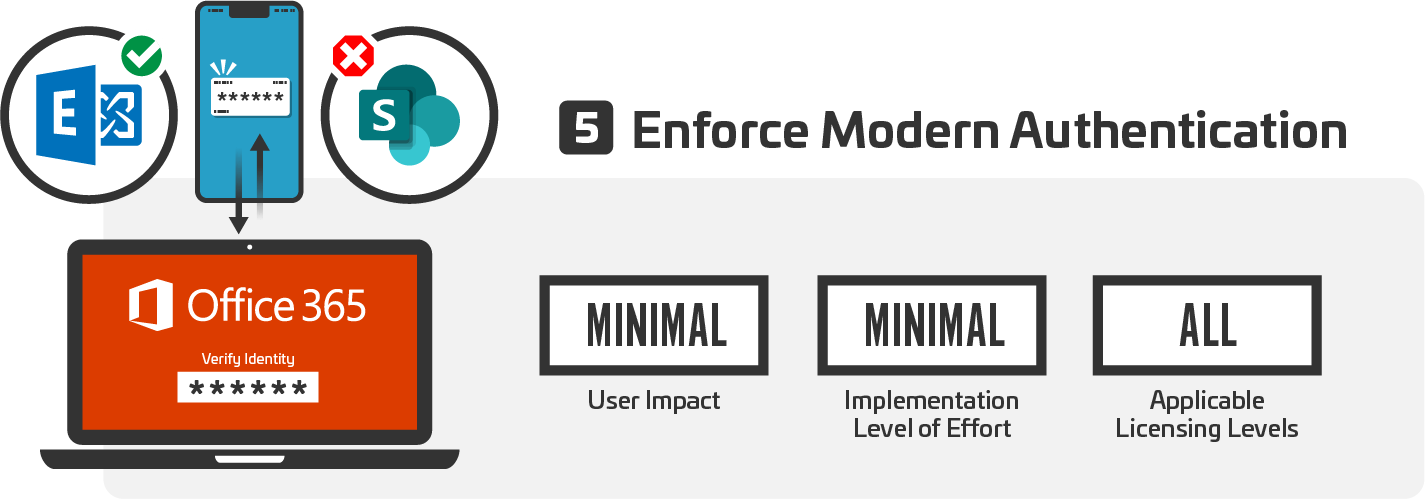
Office 365 can be configured in a hybrid environment. As a result, it includes functionality to enable backward compatibility with older versions of Outlook and other Office applications. In some situations, this legacy compatibility can allow users to bypass more modern controls like Multifactor Authentication. Wherever possible, this backwards compatibility should be disabled.
To confirm that modern authentication for Exchange is enabled, use the following PowerShell:
| Get-OrganizationConfig |select-object Name, OAuth2ClientProfileEnabled |convertto-json |
To confirm that legacy authentication for SharePoint is disabled, use the following PowerShell:
| Get-SPOTenant | select-object LegacyAuthProtocolsEnabled |convertto-json |
Let us know if you need more information on Microsoft Office 365 Configuration, we would be happy to share to our experience. Get More Info
Business Email Compromise Series