So far in our journey, we've laid the groundwork by introducing the concept of BEC attacks and exploring their rising prevalence. In Part 2, we delved into the mechanics of BEC attacks within O365...


So far in our journey, we've laid the groundwork by introducing the concept of BEC attacks and exploring their rising prevalence. In Part 2, we delved into the mechanics of BEC attacks within O365...

Welcome back to our series on safeguarding against Business Email Compromise (BEC) within Office 365. Previously, we've explored the rise of BEC attacks, their operational tactics, and essential ...
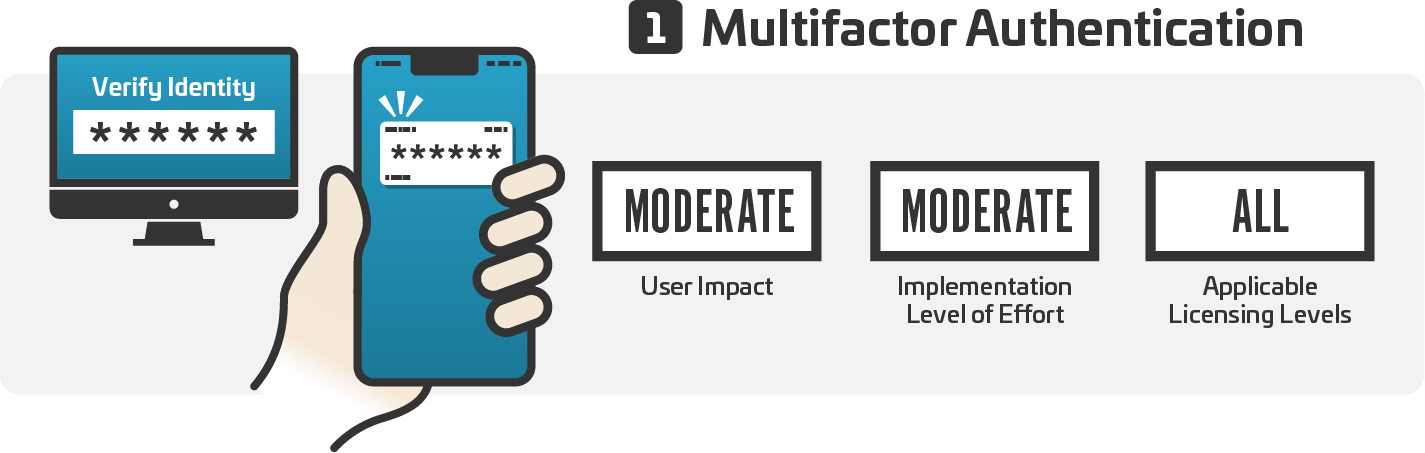
In the initial segment of this series, we unveiled the mechanics behind Business Email Compromise (BEC) attacks and explored the reasons behind their surge. The subsequent part delved into the ...

Business e-mail compromise (BEC) is a class of cybercrime that is growing rapidly. Over the past five years, BEC attacks have resulted in billions of dollars in losses from companies of all sizes...

Globally, businesses of every scale are confronting the escalating threat of Business Email Compromise (BEC), a cybercrime that has bilked organizations out of billions over the past decade. The...