Enhancing Multi-Factor Authentication Effectiveness Through Continuous Threat Exposure Management
Oct 10, 2022
Continuous Threat Exposure Management (CTEM) represents a proactive approach to identifying and mitigating risks within an organization's attack surface. It emphasizes the importance of swiftly pinpointing real threats and implementing effective mitigation strategies to minimize risk exposure.
The Critical Role of Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is a security mechanism that requires users to provide multiple verification factors to gain access to a resource, enhancing protection against unauthorized access and account takeover attempts. Despite its significance, the effectiveness of MFA hinges on proper implementation and configuration. Inadequate deployment can leave MFA susceptible to various cyberattacks, such as phishing and man-in-the-middle attacks, undermining its intended security benefits.
To manage the risk of MFA solutions not doing their job, SecureSky regularly reviews areas such as the ones listed below
MFA Policies, Rulesets, or Conditions
SecureSky's approach to Continuous Threat Exposure Management includes a detailed analysis of MFA effectiveness, revealing potential vulnerabilities in what many consider a straightforward security measure. This analysis encompasses several key areas:
1. MFA Policies and Conditions:
-
- Examination of Multi-factor authentication solution settings to ensure policies are active, unaltered, and effectively triggering re-authentication under specific conditions, such as unusual activity or location changes.
In Azure Active Directory (AAD) these types of policies are referred to as Conditional Access Policies, and a policy inventory as illustrated below: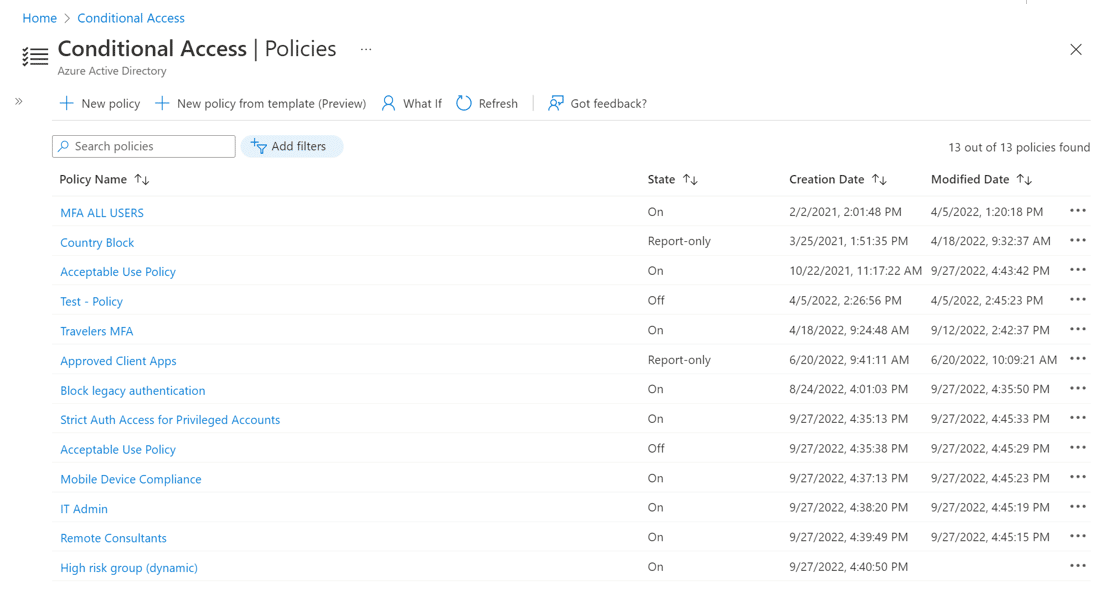
2. Frequency of MFA Multi-Factor Authentications (Days Between)
Reviewing the days between Multi-factor authentication is an indication that policies are working as intended, for example, all users are re-authenticated no greater than every 30 days, including users using the same devices and the same locations. The inverse of this is also true, as users not re-authenticating with the defined risk tolerance period is a strong indicator that there are conflicting policies enabled, or there are users not covered by the policy set.
Below is an overview example indicating such issues, with the ability to drill down to analyze specific users and groups to remediate such conflicts or coverage gaps.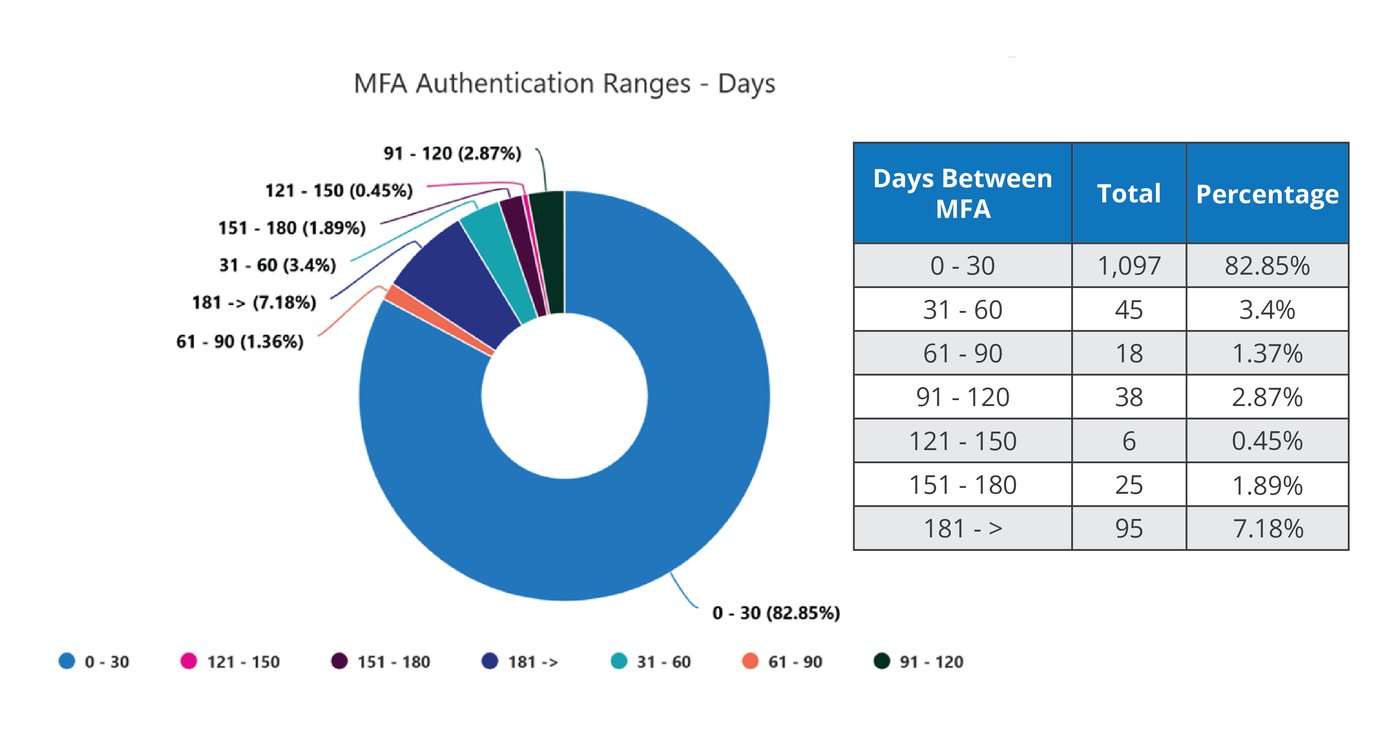
3. Days Since Last Login
This analysis can indicate two risk factors. The first is a signal that there are user accounts that require maintenance, meaning disabling dormant user or guest accounts.
The second is to identify “break glass” accounts, or accounts set up to bypass normal access controls in a critical emergency. While such accounts are a necessary evil, they must be regularly audited, because they typically are used for root systems and offer highly privileged access. Mandatory policies for break glass accounts include a credentialing process, notification of access, and a time duration upon the credentials.
The below graphic is an example of an environment with a large exposure of stale or broken glass accounts.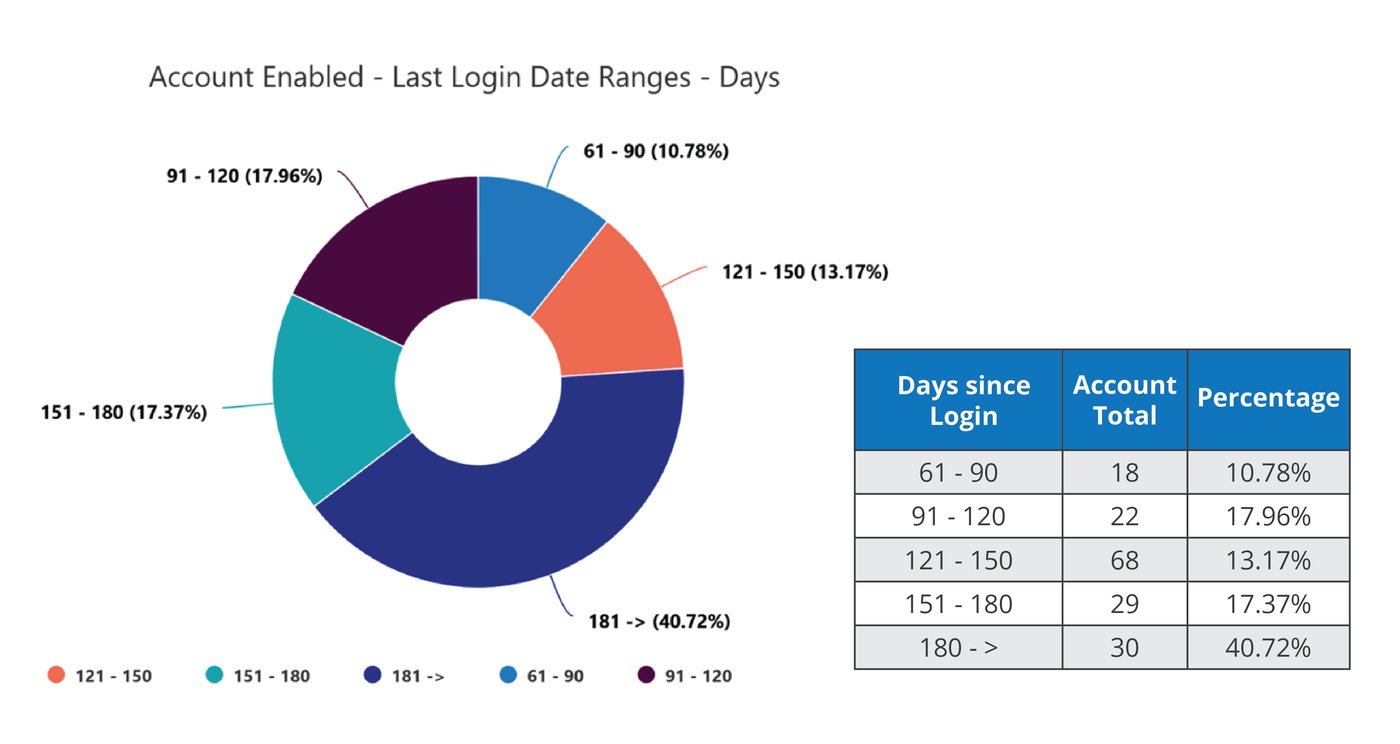
4. Authentication Type Trend
Authentication type is what technology or connection triggered an authentication, for example, primary/SSO access, per-user MFA (typically configured to not trip as often when access is from a trusted IP address and/or device), additional tool/policy-driven conditions, or by an application.
On a macros basis, this trending analysis is an indication of how policies are actually working, especially during phases when such policies are being expanded or tuned. An example of this type of trending is shown in below.
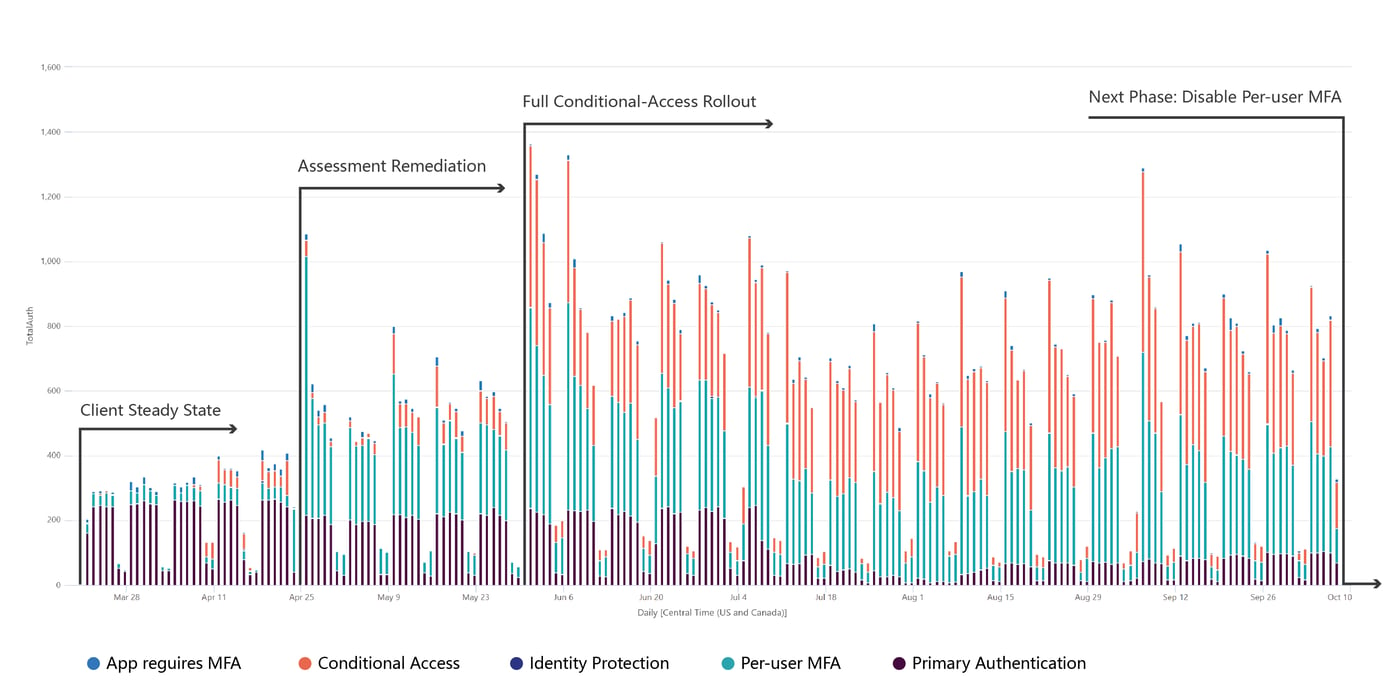
Multi-Factor Authentication Method
Authentication method is “how” a person provides an additional identification factor, beyond their initial credentials, for example by acknowledgment or receipt of a code via text or phone call on or to a registered or known device, biometrics on a known device (such as Windows Hello for Business), use of a physical security key, or connection to an authenticator application registered to the user, such as Microsoft or Google Authenticator, Duo Mobile, or Authy, again with an acceptance process or by the application generating a time-limited OATH verification code.
Each method has its pros and cons, balancing risk with user convenience. This is a particularly important analysis, again, to understand that the MFA methods the organization wishes to use are being utilized.
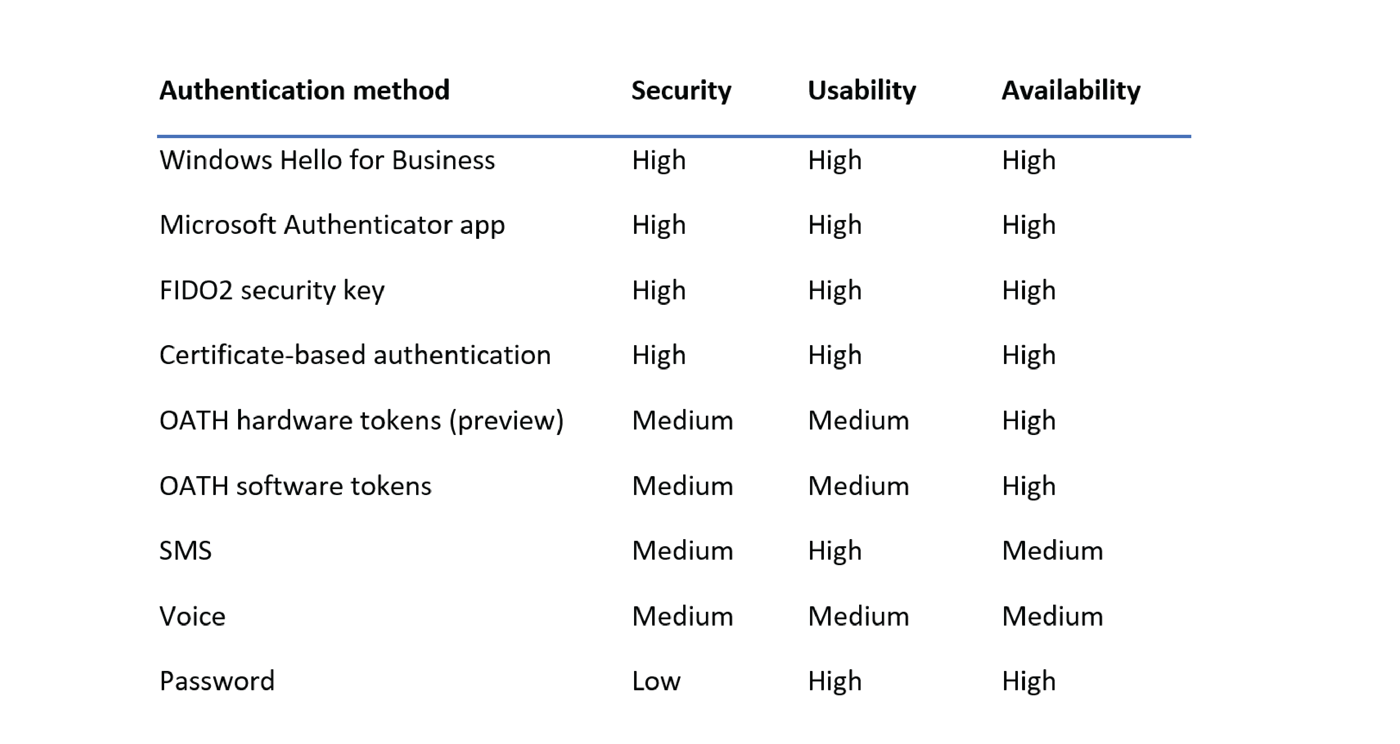
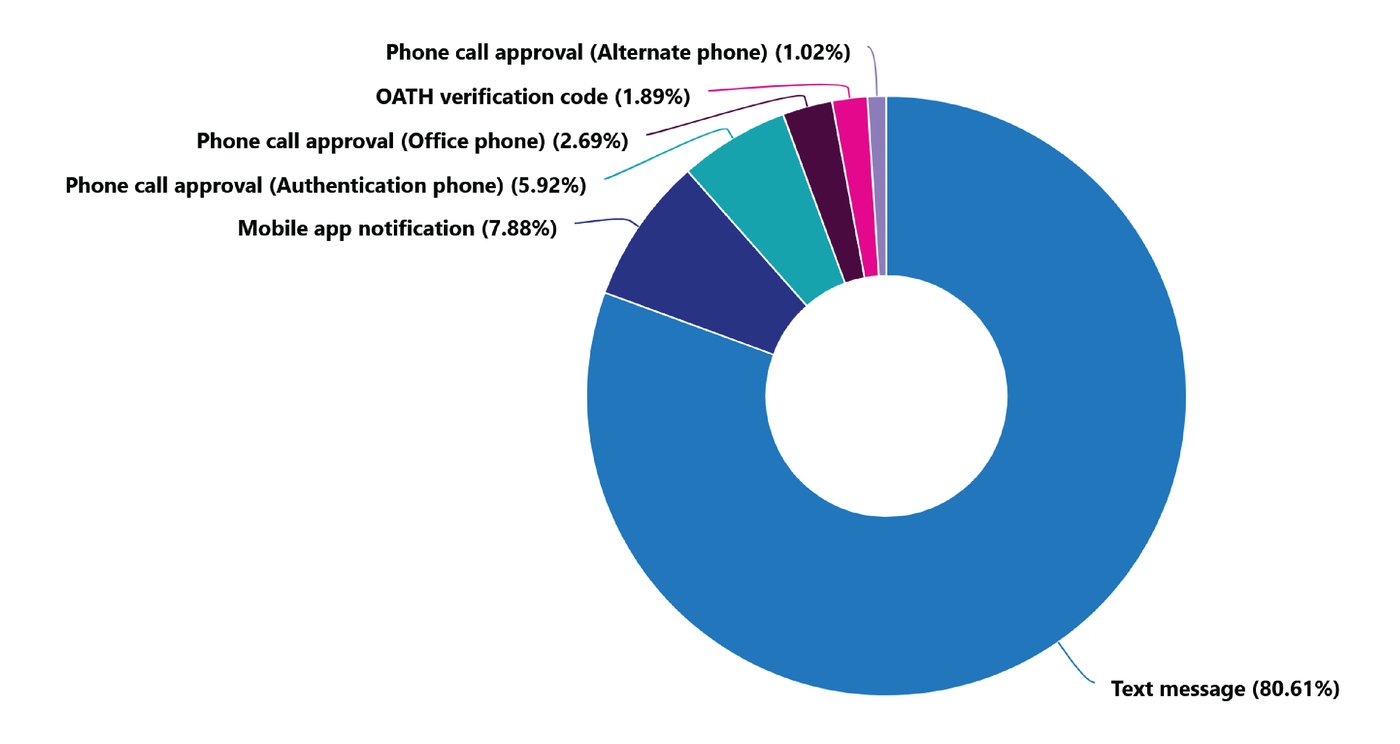
This analysis should be segmented by type of user group/access, with more stringent methods being used as privileges increase.
An example of this analysis shows the percentages by method of authentication method. The below environment indicates a user environment primarily using text messaging, or SMS as labeled in the above chart. While below this specific method, there are multiple sub-methods, for example, texts requesting simple yes/no user validation, adding geo-based intelligence, or even number matching from an additional data source, the below analysis would trigger additional research given simple text messaging's susceptibility to social engineering. The recent "MFA bombing" (also known as "MFA fatigue") attack on Uber, in which the user was tricked into pressing "yes" [meaning, yes, this authentication request was really made by the user] by an overload of push notifications lacking additional context or interaction requirements is a prime example of the weaknesses of this authentication method.
Ensure Critical Cybersecurity Controls
Each graphical example included above is a macro or high-level representation of the data. The tools used by SecureSky allow quick mining and drill-down of the data to identify the root cause of gaps in policy or account coverage. Additional areas of authentication and identity management exposure hunting performed by SecureSky not represented in this overview include non-interactive sign-ins, guest users, and detailed Conditional Access analysis.
MFA effectiveness analysis is a crucial component of SecureSky's Continuous Threat Exposure Management services, ensuring that critical security controls like MFA are functioning as intended. This comprehensive review not only highlights potential policy gaps and coverage issues but also supports the continuous improvement of security measures against evolving threats. For organizations looking to strengthen their security posture, understanding and optimizing MFA effectiveness is a vital step.
If you have any questions related to multi-factor authentication or exposure management, please feel free to contact us by completing our contact form or emailing info@securesky.com.
