Navigating Cybersecurity Trends: Insights from Azure Security Assessments
Mar 30, 2022 | Industry Insight
This article delves into the pivotal cybersecurity trends emerging from SecureSky's comprehensive security assessments of Microsoft Azure environments throughout 2021. Our analysis spans a diverse array of clients, from those in the initial stages of cloud migration to those operating in sophisticated cloud-native processing ecosystems.
In our practice of cloud security assessment and remediation support, we meticulously evaluate our clients' Azure security configurations against established industry best practices and recognized benchmarks. This evaluation serves as a foundation for our subsequent security hardening efforts. It's important to note that the initial security posture of many clients tends to reflect a reliance on default settings, likely due to the complexity of Azure's security options and a general lack of awareness about optimization opportunities.
Our findings, while initially indicating a lower security posture within our client base compared to the broader Azure user community, provide valuable insights into the cybersecurity trends shaping cloud security today. These insights are not only crucial for understanding the current landscape but also for guiding administrators across all levels of Azure maturity in enhancing their security measures.
Key Findings Snapshot
13% of applications used best practice configurations
17% of environments had appropriate monitoring and response capabilities
30% of all industries comply with best practices
55% and 57% of security control are established in cloud OS/Containers and Networks
55% have limited tenant-level access
Identifying Key Security Trends: A Framework-Aligned Approach
In 2021, SecureSky observed subtle changes in Microsoft's enhanced security controls and functionality. With that in mind, in this blog, SecureSky has identified trends within higher-level security categories rather than individual checks or findings themselves. Normalizing our results enables us to define comparable data and align each data set with the National Institute of Technology Cyber Security Framework (NIST CSF). These higher-level categories are:
- User and API Access / Identity and Entitlements
- Data Storage and Access Controls
- Application Configuration
- OS / Containers
- Network Security
Also evaluated across these categories were two Cloud Security Posture Management measurements:
- Protective Controls Configurations
- Activity Monitoring, Detection, and Response
Descriptions of these categories are provided in the Appendix below.
Enhancing Azure Security: Key Areas for Maturity Growth
In 2021, notable advancements in cybersecurity maturity were observed, particularly in the realms of User and API Access / Identity and Entitlements, with Azure Active Directory improvements leading the charge. A significant driver of this progress was the strategic implementation of Conditional Access Policies, streamlining Multi-Factor Authentication (MFA) deployment to mitigate user access risks effectively.
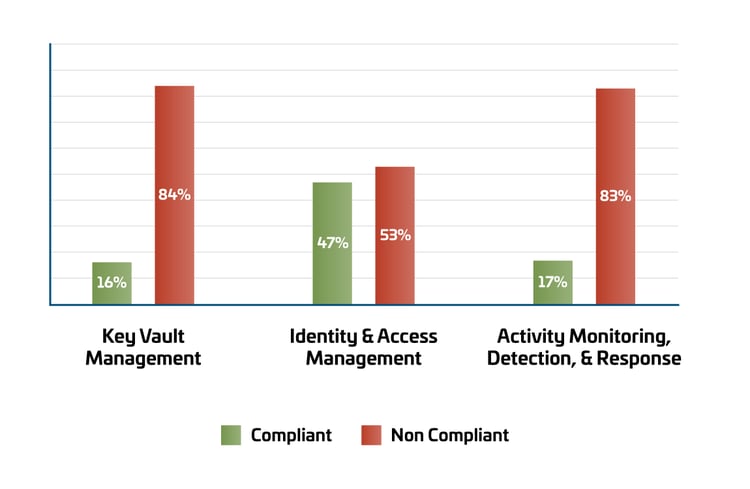
However, the journey to bolster Microsoft Azure's security posture reveals critical areas needing attention. Activity Monitoring, Detection, and Response configurations present the most significant room for improvement, with only 12% compliance. Closely following is the security of Data Storage and Access Controls, including Key Vault utilization, at 25% compliance. These figures highlight urgent areas for enhancement, especially considering the rapid adoption of modern application architectures and their associated risks.
The concept of "shared responsibility" in cloud security underscores the division of security management between cloud service providers and customers. This model suggests that as one moves up the cloud stack—from the foundational infrastructure to user and API access—the customer's responsibility for implementing security controls increases. Surprisingly, the analysis reveals that the extent of adequately hardened security configurations across these critical layers varies significantly, with compliance rates ranging from a mere 13% to just 47%.
This disparity underscores a pressing need for organizations to prioritize the hardening of security configurations within Azure environments. Given the shared responsibility model, customers must proactively address these vulnerabilities to safeguard their assets effectively. The low compliance percentages in such pivotal security domains call for immediate action to enhance risk management strategies and fortify Azure's security framework.
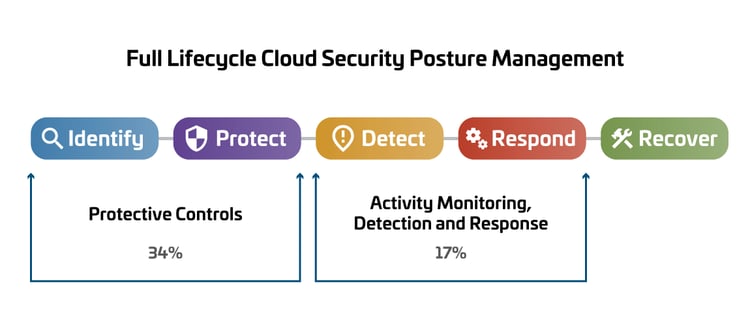
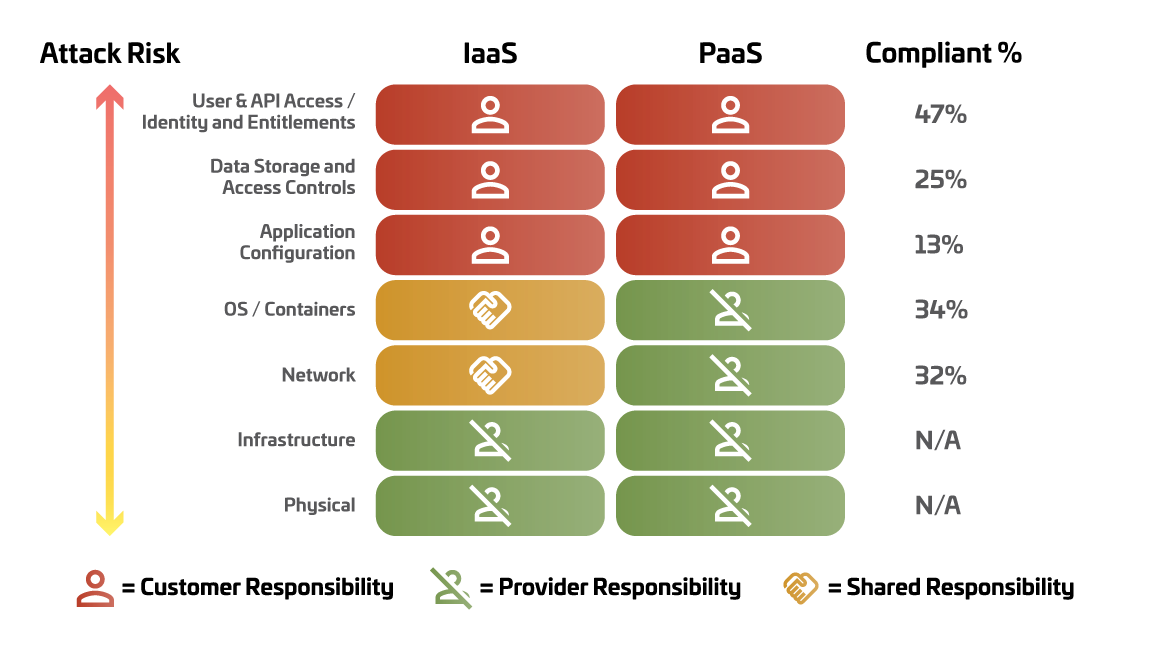 As described above, two measurements were evaluated across all levels, both resulting in troubling conclusions. Overall, across SecureSky clients prior to our working with them to harden their environments and deploy Managed Detection and Response services, only 34% of Protective Controls were deployed, and a mere 17% of configurations to enable adequate visibility and threat detection were in place.
As described above, two measurements were evaluated across all levels, both resulting in troubling conclusions. Overall, across SecureSky clients prior to our working with them to harden their environments and deploy Managed Detection and Response services, only 34% of Protective Controls were deployed, and a mere 17% of configurations to enable adequate visibility and threat detection were in place.
Comparing Microsoft Azure to Microsoft 365 Security Posture
This Azure security analysis is similar to SecureSky's compilation of security configuration findings related to our clients' Microsoft/Office 365 environments (https://blog.securesky.com/2021_security-control-trending), areas of maturation of security practices, as well as many areas of inadequate hardening. Interestingly, in overlapping categories, results are very comparable, for example:
- User and API Access / Identity and Entitlements - results between Microsoft/Office 365 and Azure show that only approximately half of security controls comply in each case.
- Application plug-Ins in Microsoft/Office 365 and Application Configuration in Azure - again, comparing application connections and ongoing application security, both studies indicate a low percentage of controls enabled, which is very concerning considering the rapidly expanding attack vectors at the application connection level.
- Activity Monitoring, Detection and Response – as with the Azure findings described above, SecureSky found a low percentage of organizations have the proper configuration of activity log settings from Microsoft/Office 365. Visibility and response automation is critical to properly detecting and responding to threats and is a rudimentary element of an enterprise security program.
Deeper Dive
In analyzing security program pillars across all elements of the cloud stack ("shared responsibility" model), SecureSky garnered additional critical insights, including:
Data Storage and Access Controls - Encryption and Key Vault Application Service Settings
When analyzing data storage and access controls for such data, a cloud buyer responsibility, and obviously high-risk areas, SecureSky found approximately 50% of companies reviewed attempted to follow encryption best practices. However, most illustrated at least some enablement gaps. Most concerning were severe weaknesses in Key Vault management techniques (16% compliant - deployed but not utilized) in securing applications and data storage.
User and API Access / Identity and Entitlements - Identity and Access Management (IAM)
Identity and Access Management (IAM) settings saw the most significant growth in maturity over the past year. With identity as the new "perimeter," the plethora of information surrounding credential theft leading to Account Take Over (ATO), privilege elevation, and lateral movement has rightfully focused security efforts on IAM.
This maturing confirms that efforts to simplify and enable flexible MFA deployment, with Conditional Access Policies and Just-in-Time privileges, have helped companies adopt modern authentication and reduce legacy protocols to minimize risk.
While widespread adoption of Conditional Access Policies has helped simplify MFA, SecureSky has also found that a lack of policy validation continues to leave companies exposed. Additionally, attackers focus on these flaws in MFA deployments and MFA or the vendor itself, such as the recent Duo and Okta security issues.
Finally, although companies are improving monitoring for certain authentications, we see a lack of focus on service accounts (internal and vendors), guest user access, and most importantly, application connections, creating unnecessary risk while attacks against these vectors continue to increase.
Activity Monitoring, Detection, and Response
As voiced throughout this blog, the most opportunity for improvement is related to logging and monitoring settings. For example, SecureSky observed that while many clients' legacy firewalls and traditional endpoints provided adequate logging, most companies were not taking advantage of native cloud detection and auditing capabilities to get visibility into east-west traffic. In addition, auditing was especially poor in the modern application stack (10%), consisting of PaaS-based services and dynamic workloads.
Cybersecurity for the Future
SecureSky has seen a positive shift in organizations hardening their User and API Access / Identity and Entitlements settings while taking advantage of functionality that helps simplify deployment for Multi-Factor Authentication. More specifically, there has been a positive shift in organizations taking advantage of Conditional Access Policies. Unfortunately, while there have been noticeable maturity improvements in this area, these broad/flawed policies and incomplete deployments leave clients' cloud environments at high risk.
SecureSky continues to see significant gaps in Activity Monitoring, Detection and Response, and Data Storage and Access Controls across all elements of the cloud stack ("shared responsibility" illustration), representing a high risk. The most gaps identified in environments assessed were found in key management and application logging, representing the most opportunity for organizations to improve their cloud security posture.
Recommendations
Throughout this blog, we have stressed the importance of proper configuration and visibility as part of your tactical roadmap. With the dynamic nature of cloud environments, we should also stress the importance of continuous assessments to ensure the ongoing validation of security-hardened configurations.
For more strategic recommendations, see our eBook, The Modern Enterprise-Level Security Stack (https://securesky.com/resources/ebooks/), which includes the following recommendations applicable to securing all cloud environments:
- Understand the current capabilities and roadmaps of security tools and audit settings available from your cloud provider(s) of choice, compared with your current security technology stack. In cloud migration planning and deployments, incorporate security measures in your strategies.
- Review your existing cloud licensing to find redundant functionality you may be paying for twice. You may find this type of redundancy as part of your legacy security technology stack and cloud-native functionality that is included with your current licenses. Determine if the tools available to you provide adequate cloud coverage to assess risk or security control status real-time, as well as provide automation capabilities for security posture management enforcement and threat response.
- Fully deploy your modem security architecture, extend your zero-trust model to include cloud resources and invest in training and optimize security controls to detect, investigate and respond to threats using new automated techniques.
- Extend and modify your enterprise risk program to include data flows and other risk factors associated with each cloud environment, for example authentication policies, access controls, file sharing, guest users, and application connections.
- Message corporate leaders on the current and future state of cloud security, and address the upcoming realities with those executives who voice such opinions as “the fox is watching the henhouse,” “we are putting all of our eggs in one basket,” or “the cloud will never be as secure as on-premise.” As discussed throughout this paper, major IaaS and SaaS providers will soon be much more secure than on-premise solutions because of their ability to tightly integrate operational and security tools, automate functions that were once almost exclusively manual and to collect and apply massive amounts of threat intelligence. The caveat to this, of course, is the ability of IT and security practitioners to take advantage of capabilities to address organization their shared responsibilities.
Appendix
User and API Access / Identity and Entitlements
This category covers users, user permissions, Azure Active Directory settings, groups and roles, Multi-Factor Authentication settings, guest users, and their permissions, among a few settings assessed. Identity and Access Management (IAM), controls to ensure approved individuals can access specific resources at certain times, is a subcategory in this category.
Data Storage and Access Controls (including Key Management)
This category compares SQL Server, PostgreSQL, and MySQL settings against industry best practices, ranging from encryption settings for databases, firewall rules, network access, Azure Key Vault, Kubernetes, resource locks, and security-related settings within the Microsoft Azure Storage Account service.
Application Configuration
This category covers security-related settings with the Microsoft Azure Application Service and includes everything from programming language version support, remote file transfer configuration, and application secrets storage settings.
OS / Containers
Settings within this category pertain to virtual machine disk encryption settings, patching and updates, virtual machine extension provisioning, and general virtual machine security settings.
Network Security
This category looks at Network Security Group rules for misconfigurations, default rule settings, and remote protocol-specific configuration settings.
Protective Controls
Settings within this category look at whether an organization subscribes to the extra security settings as part of the standard tier and whether an organization takes full advantage of the various settings within this area of Microsoft Azure. This also includes both Microsoft (Defender for Cloud Apps, Microsoft Defender Endpoint, etc.) and third-party products and cloud-native security policy and controls settings.
Activity Monitoring, Detection and Response
Diagnostic and activity log settings are the primary focus of this category, where logs are stored and the configuration settings of those storage mechanisms. Also, as the category name indicate it include Detection and Response enablement.
SecureSky’s core assessment does not include evaluation of patch management of workloads, although we do see confusion in the interpretation of the “shared responsibility” model related to patching, as well as inconsistency between cloud and on-premises environments.
